
Attackers are using an advanced phishing technique, known as CoPhish, that leverages Microsoft Copilot Studio to trick users into granting unauthorized access to their Microsoft Sign In ID accounts.
A recent report details the attack and highlights how, despite Microsoft’s efforts to strengthen its consent policies, significant vulnerabilities remain in cloud-based AI tools.
The growing adoption of tools like Copilot by organizations highlights the need for careful oversight of low-code platforms . In this space, user-configurable features designed to boost productivity can inadvertently facilitate phishing.
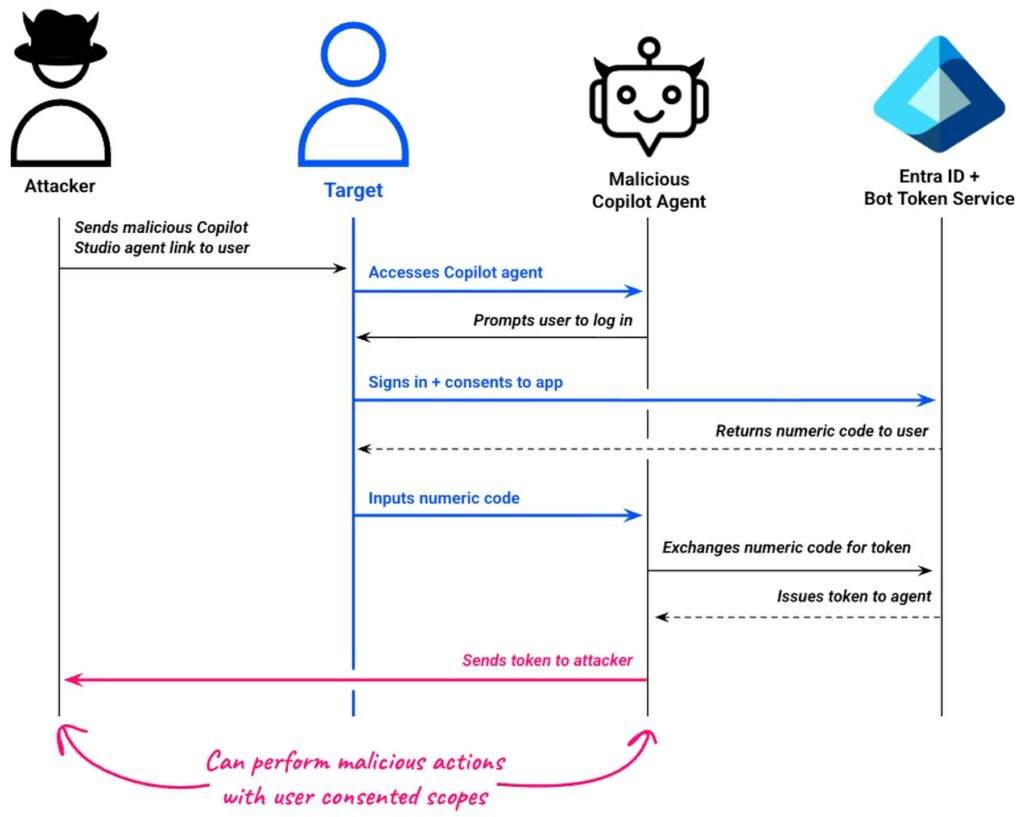
This attack, discovered by researchers at Datadog Security Labs , uses customizable AI agents hosted on legitimate Microsoft domains to disguise traditional OAuth consent attacks , making them appear trustworthy and circumventing users’ suspicions.
Attackers are able to design and create harmless-looking chatbots to obtain users’ login credentials and, subsequently, OAuth tokens that can be used to perform malicious actions, such as accessing calendars or reading emails.
OAuth consent attacks, classified under the MITRE ATT&CK T1528 technique, involve tricking users into approving malicious app registrations that request broad permissions to access sensitive data.
Attacks conducted within Entra ID environments involve attackers creating application logs to gain access to resources made available by the Microsoft Graph, such as email or OneNote. This is done by using phishing links that trick victims into granting consent. Once approval is obtained, the resulting token gives the attacker the ability to impersonate the user, allowing data exfiltration or further compromise.
Over the years, Microsoft has implemented stronger defenses, such as restrictions on unverified applications. Additionally, a July 2025 update established the default setting of “microsoft-user-default-recommended,” which automatically blocks access to permissions considered high-risk , such as Sites.Read.All and Files.Read.All, unless administrator approval is granted.
However, there are still gaps: unprivileged users can still approve internal apps for permissions like Mail.ReadWrite or Calendars.ReadWrite, while administrators with roles like Application Administrator can allow any permission on any app.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
