
Redazione RHC : 12 November 2025 07:23
After four years, OWASP has updated its TOP 10 list of the most dangerous web application risks, adding two new categories and revising the ranking structure.
The organization has released a draft of the 2025 release, which is open for comment until November 20. This document is a near-final version of the OWASP Top 10, reflecting current threats to web developers and administrators.
As in the previous edition, Broken Access Control remained in first place. This category has been expanded to include SSRF vulnerabilities , which previously ranked tenth.
Security Misconfiguration ranks second, up from fifth in the 2021 ranking. Supply Chain Issues ranks third. This is an expanded version of the Vulnerable and Obsolete Components category, which includes issues and compromises in the dependency ecosystem, build systems, and deployment infrastructure. According to OWASP, these risks were among the professional community’s top concerns during the survey.
Cryptographic Failures, Injection (including XSS and SQL injection), and Insecure Design followed: all three categories dropped two spots, occupying fourth, fifth, and sixth place, respectively. Authentication Failures, Software or Data Integrity Failures, and Logging & Alerting Failures maintained their previous positions, from seventh to ninth.
A new category in the top ten is “Incorrect Handling of Exceptional Conditions,” which concludes the list. It includes errors in exception handling, incorrect responses to anomalies, improper error handling, and logic failures that occur under non-standard system operating conditions.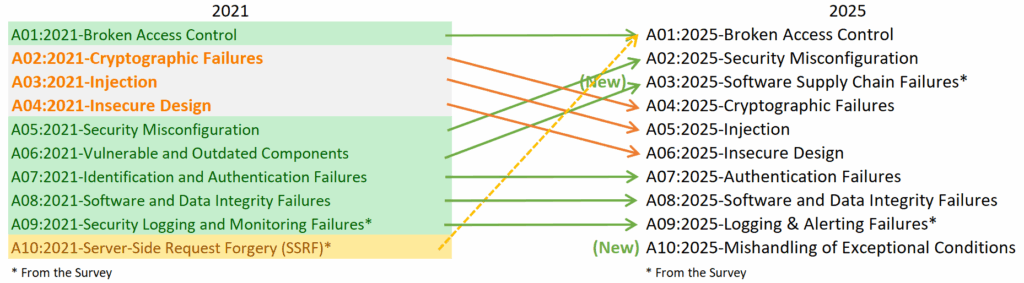
Top 10 OWASP Changes from 2021 (OWASP)
OWASP representatives emphasized that the structure of the 2025 list differs from that of 2021. The analysis now takes into account the number of applications tested during the year and the number of systems where at least one instance of a specific Common Weakness Enumeration (CWE) was detected .
This approach allows us to monitor the prevalence of vulnerabilities across the entire range of tested products , regardless of the number of occurrences of the same issue within a single application. A total of 589 CWEs were used for the analysis, compared to just 30 in 2017 and approximately 400 in 2021.
To assess exploitability and technical impact, OWASP used CVE data, grouping it by CWE and calculating average values based on CVSS scores. Due to the limitations of automated testing, only eight categories were selected based on this data. The remaining two were derived from a community survey in which experts identified the risks they considered most critical in practice.
The OWASP Top 10 2025 ranking therefore reflects a shift in community attention from classic implementation errors to the configuration, architecture, and supply chain issues that increasingly lead to compromises in modern web applications.
 Redazione
Redazione