
Redazione RHC : 12 November 2025 11:47
Researchers have discovered a vulnerability in the new Midnight ransomware , based on the old Babuk source code. The malware is marketed as an “advanced” version of the malware, but attempts to speed up and enhance the encryption process have proven unsuccessful: Norton researchers have managed to create a free decryptor for the affected data.
Experts say Midnight is based on Babuk’s source code, which was leaked into the public domain in 2021 and subsequently used as the basis for dozens of malware projects.
Midnight almost entirely replicates the structure of its predecessor, but the developers decided to change the encryption scheme: the malware uses ChaCha20 to encrypt the contents of files and RSA to encrypt the ChaCha20 key.
However, researchers discovered a flaw in the RSA key usage, allowing them to partially recover the data and then create a full decryptor . The tool is free and has already been released publicly.
Like Babuk, Midnight encrypts only portions of files to act faster and paralyze the system. The size of the encrypted blocks depends on the file size: large documents or databases become unreadable almost instantly . In recent builds, the malware has expanded its target list to cover almost all file formats, with the exception of executable files (.exe, .dll, and .msi).
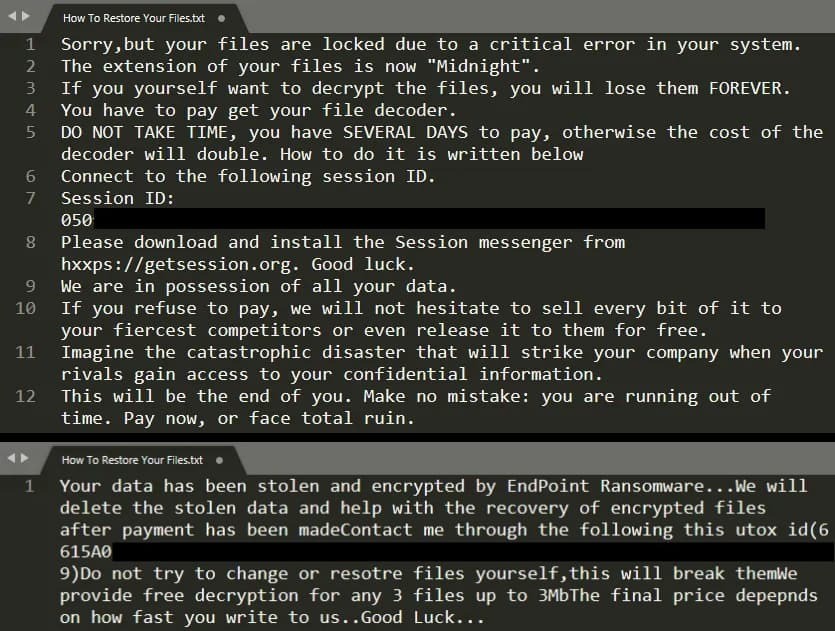
Infected devices end up receiving files with the .midnight or .endpoint extension, sometimes this tag is embedded directly into the file’s contents. The victim is left with a standard ransom note (How To Restore Your Files.txt) and sometimes even a log file such as report.midnight or debug.endpoint, which shows how the script is working.
 Redazione
Redazione