
Redazione RHC : 8 December 2025 17:56
An increasingly aggressive campaign, directly targeting remote access infrastructure, has prompted threat actors to actively attempt to exploit vulnerabilities in Palo Alto Networks’ GlobalProtect VPN portals .
On December 5, Palo Alto Networks issued an urgent advisory, urging customers to adopt multi-factor authentication (MFA) , limit portal exposure through firewalls, and apply the latest patches.
Organizations using the popular VPN solution to secure remote work have been put on high alert, according toGrayNoise ’s monitoring report, which detected scans and exploitation efforts from over 7,000 unique IP addresses globally .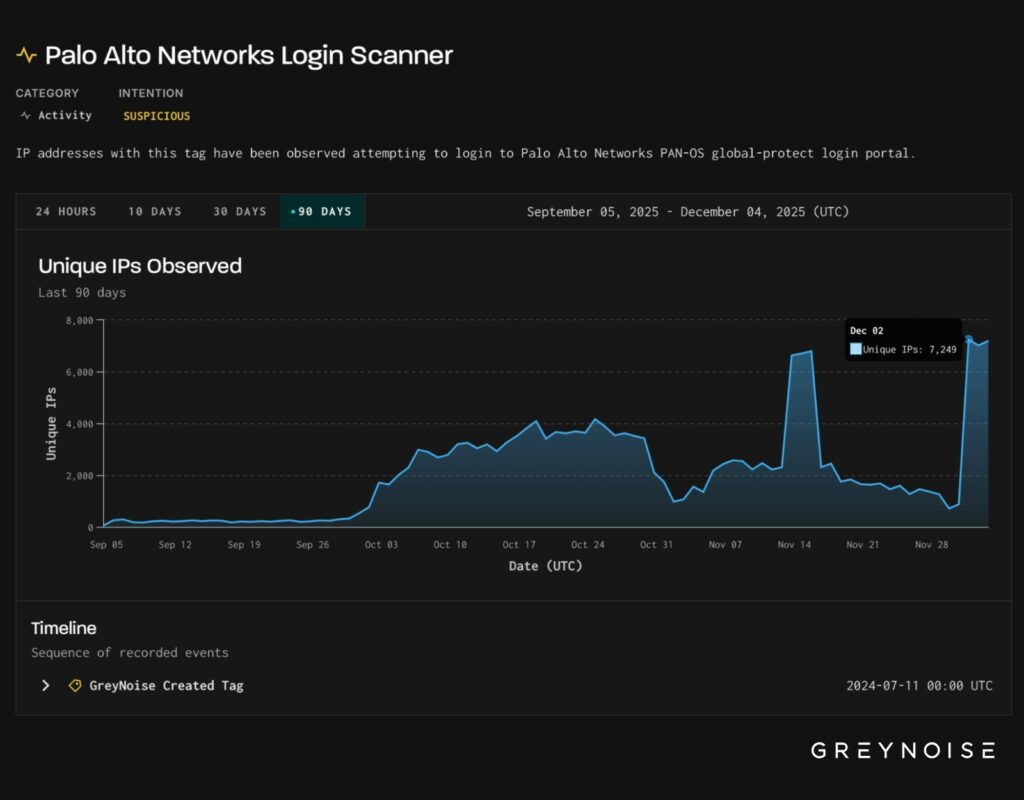
Targeting observed by Ip (Source: GreyNoise)
Starting in late November 2025, attacks exploiting vulnerabilities in GlobalProtect gateways have been detected, primarily those publicly accessible through UDP port 4501.
Palo Alto Networks’ GlobalProtect has long been a prime target due to its ubiquity in enterprise environments. Legacy flaws, such as CVE-2024-3400 (a critical command injection vulnerability, fixed in April 2024 with a CVSS score of 9.8), continue to plague unpatched systems.
Recent waves exploit misconfigurations that allow pre-authentication access, including default credentials or exposed admin portals. Attackers use tools such as custom scripts that mimic Metasploit modules to enumerate portals, brute-force logins, and drop persistent malware.
According to data from Shadowserver and other threat intelligence feeds, IP sources include residential proxies, Bulletproof hosting providers, and compromised VPS instances in Asia, Europe, and North America.
Indicators of compromise include anomalous spikes in UDP traffic on port 4501, followed by HTTP requests to the /global-protect/login.urd endpoints. In confirmed breaches, intruders exfiltrated session tokens, enabling lateral movement into corporate networks.
 Redazione
Redazione