Global attention to cybersecurity continues to grow in a context dominated by digital transformation and the rapid spread of artificial intelligence (AI) technologies, making it easier to identify vulnerabilities and conduct complex attacks. In this context, a country’s ability to ensure protection, coordination, training, and international cooperation has become a key indicator of national stability.
In the 2024 Global Cybersecurity Index, Egypt and Qatar achieved a maximum score of 100, placing them among the 12 highest-performing countries globally. This result was achieved thanks to compliance with the index’s five pillars: legislative framework, technical protection, organizational structure, capacity development programs, and international collaboration .
Full compliance with these criteria places both states among global role models, within the group of 46 countries considered at the forefront of cybersecurity.
At the same time, Saudi Arabia has consolidated its position as a regional leader in investments in the sector.
In 2024, Saudi Arabia’s cybersecurity spending reached approximately $4.8 billion (equivalent to 15.2 billion riyals), a 14% increase over the previous year. According to data from the National Cybersecurity Authority, this trend reflects an ongoing process of strengthening digital infrastructure and national cyberspace defense measures.
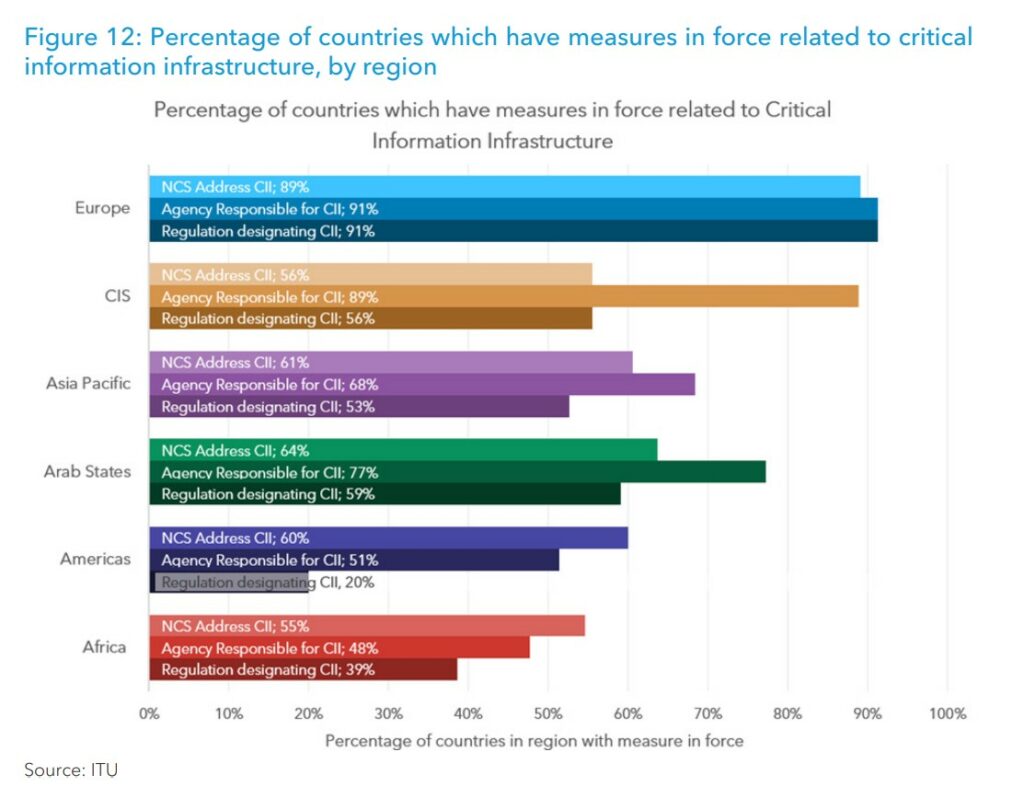
The GCI 2024 report, however, highlights marked heterogeneity among Arab countries. Beyond the countries with the highest scores—including the United Arab Emirates, Oman, Bahrain, Jordan, and Morocco , with scores between 95 and 100—there are also countries still in the process of consolidating. Algeria, Libya, Tunisia, and Kuwait rank in the intermediate range, with scores between 55 and 85, indicative of evolving systems that require further investment in technical capabilities and international cooperation.
Iraq, Lebanon, Mauritania, Sudan, Syria, and Palestine are in an early stage of building regulatory frameworks, with scores between 20 and 55. Yemen is at the bottom of the regional rankings, with scores below 20 points, reflecting a cybersecurity ecosystem still in its infancy.
The situation is further complicated by the sharp increase in threats in the Middle East. Phishing remains one of the most widely used techniques, supported by advanced social engineering methods. DDoS attacks have seen a particularly significant increase, rising 236% in the second quarter of 2025. At the same time, attacks against Microsoft Office applications, credential theft, spyware, API intrusions, and reconnaissance activities have also increased.
Ransomware and extortion operations account for approximately half of attacks with an identifiable motive. Offensive attacks leveraging artificial intelligence are also growing, particularly to automate the search for system vulnerabilities and make phishing campaigns more effective. Estimates suggest that a single cyber incident in the region costs an average of approximately $8 million, nearly double the global average. The most affected sectors are communications, energy, transportation, healthcare, and finance, confirming the urgent need for structural investments and coordinated policies to protect economic activities and essential services.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
