Today is always more important and significant to be efficient in controlling our own infrastructures; actions to put in place for this verification process shall require both proactive and post-action approach: the last aspect is fundamental when an attack or in general any malicious behavior is conducted on a targeted system and we have to know all about this action, from its start to its finalization. The paradigm “it’s happened and I have to know all about it” is checked as well by Loki.
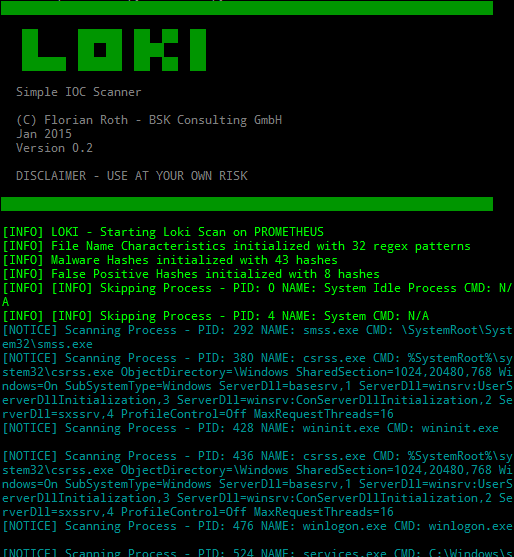
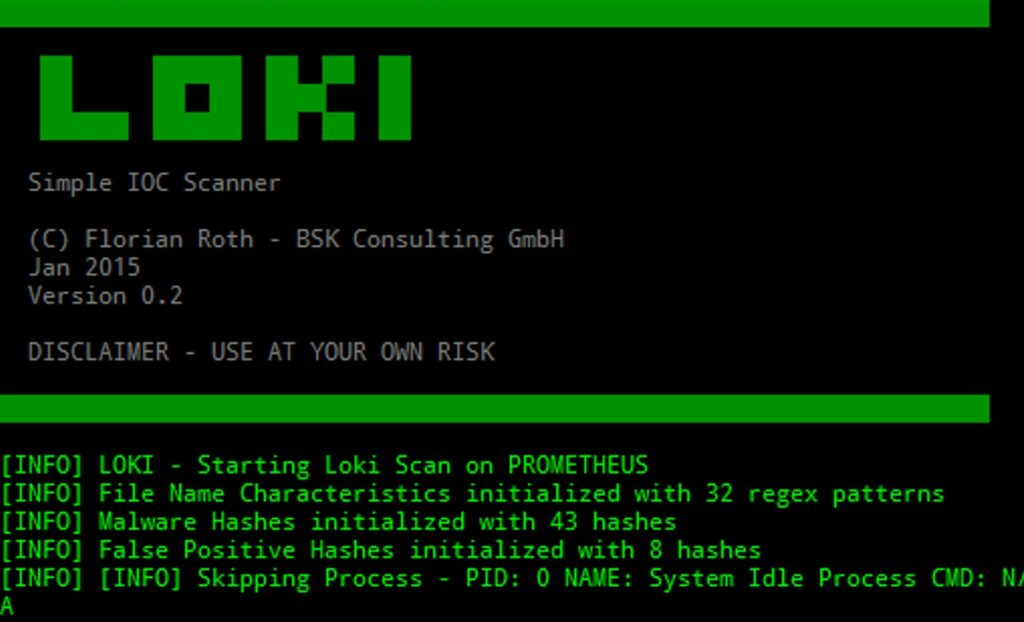
Loki is an open source tool, developed in Python by Florian Roth (aka Neo23x0) and it is a very simple and usable tool suite for IOC (Indicator of compromization) discovery in our own systems. The strength of Loki is the interaction with a dynamic set of rules freely updateable that is applied to filesystem elements and not only (for example on Windows side it inspects even the shared memory for example); users can customize rules or write new ones in order to be constantly updated with the latest IOC patterns.
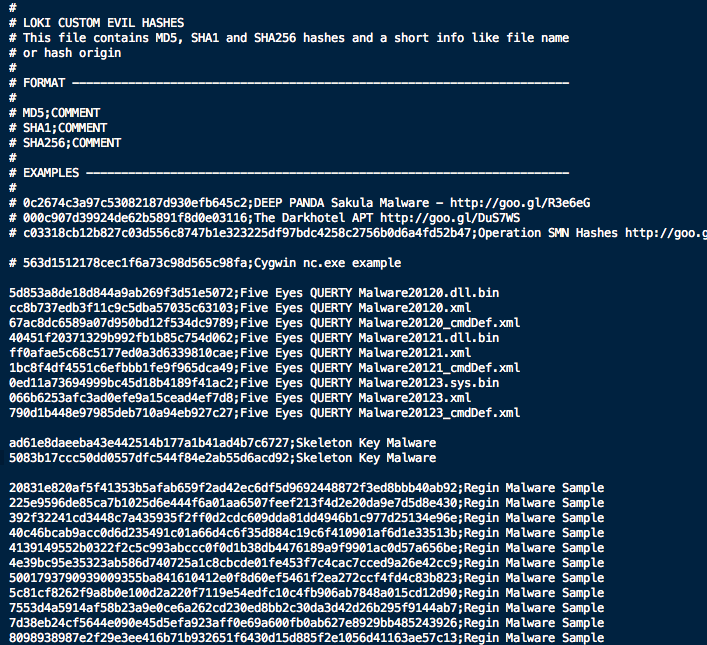
As mentioned in Florian Roth’s official repo, the detection is based on four search methods:
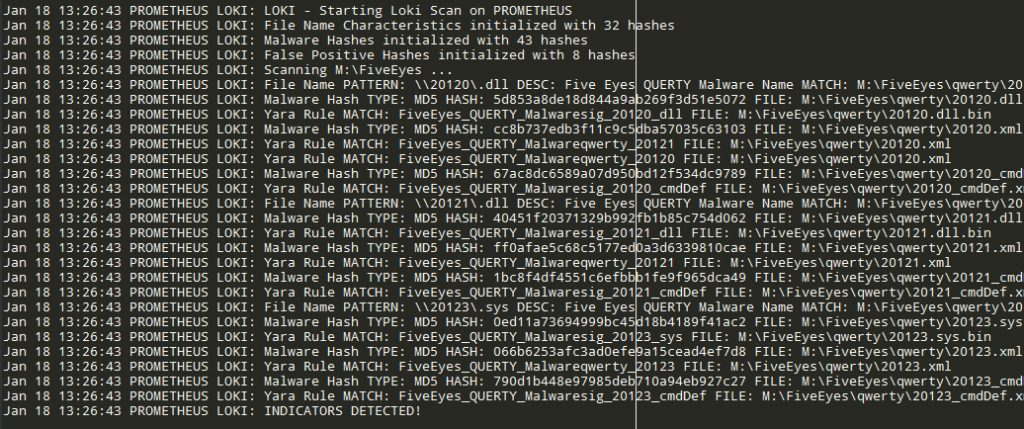
Loki can be run on Linux, Mac and Windows locally only. My forked version provides the possibility to run centrally locally with the implementation of –ip option: this tries to map a remote filesystem through SSH connection (SSHFS package is required) and assumes this mapping as scan starting point. This is very useful for centralized infrastructures in order to collect in one single point every scan results, with addition of the new –locallogging option it is even possible to redirect log into Syslog/Event Viewer in order to collect data as operative system logs.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
