
In the cyber threat landscape, few malware programs are as persistent and widespread as Formbook . What began as a simple keylogger and form grabber has evolved into a powerful infostealer sold under the Malware-as-a-Service (MaaS) model, making it accessible to a wide range of cybercriminals. Its ability to exfiltrate credentials from browsers, email clients, and other software makes it a favored tool for gaining initial access to corporate networks.
In this article, we will analyze a sample of a multi-stage dropper designed to distribute the Formbook infostealer, and, based on the evidence collected, we will illustrate the countermeasures proposed by ELMI to prevent, detect, and respond to this type of threat.
HELMETS has been operating in the IT sector as a System Integrator for forty years, offering professional consultancy and supporting private and public companies in the development of innovative projects .
The company is currently strongly focused on Digital Transformation, with particular reference to the technological areas related to process digitalization, cyber security, asset management, generative artificial intelligence, and blockchain.
Infostealer in Action: Formbook Technical Analysis
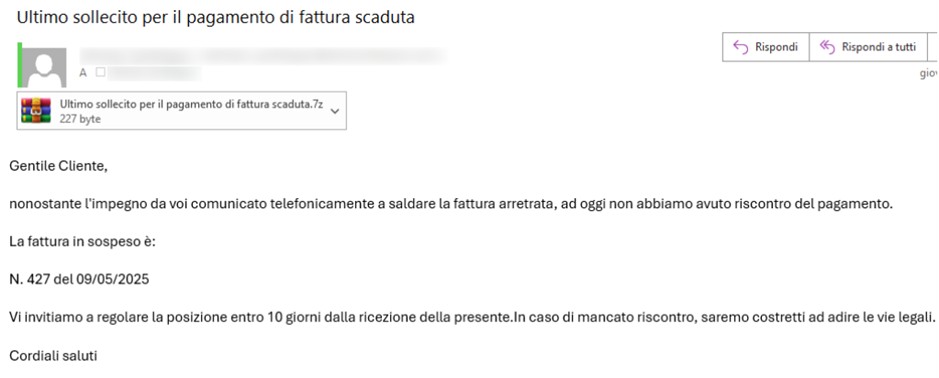
As observed in several recent campaigns documented by the National Cybersecurity Agency ( ACN ), Formbook distribution occurs primarily through malspam (Malware Spam or Malicious Spam) : malicious emails packaged to appear legitimate (fake invoices, shipping documents, quotes, or company communications). The message typically contains an attachment (.zip/.rar compressed archives or Office files with macros disabled) or a link that, when clicked, downloads an obfuscated JavaScript file. In the sample analyzed, this file is the initial dropper that starts the infection chain.
The goal of the initial phase is to trick the user into manually executing the attachment—thus relying on social engineering rather than software vulnerabilities. This approach, combined with code obfuscation techniques and the use of legitimate cloud services to host subsequent payloads, makes the campaign particularly insidious and difficult to block with perimeter controls alone.
The analysis therefore began with a JavaScript sample, revealing a complex infection chain that uses PowerShell as an intermediate stage and culminates in the fileless execution of the final payload. The threat actor implemented multiple obfuscation and evasion techniques and leveraged a legitimate service (Google Drive) to host the payload, making network-based detection more difficult.
This analysis documents each phase in detail, mapping the observed Tactics, Techniques, and Procedures (TTPs) to the MITRE ATT&CK framework and providing the Indicators of Compromise (IoCs) necessary for detection and mitigation.
The goal is not just to dissect malware, but to understand how a single file fits into the vast cybercrime ecosystem, fueling the black market for data and how it can significantly impact the operation and confidentiality of systems.
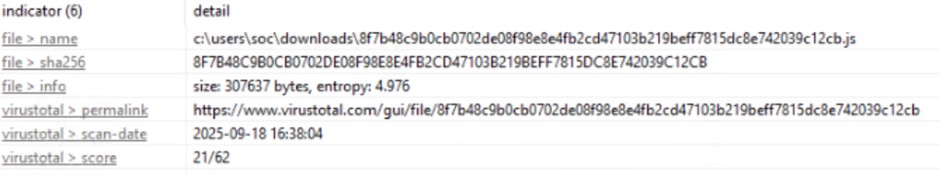
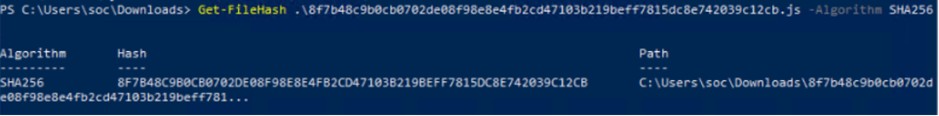
File Name 8f7b48c9b0cb0702de08f98e8e4fb2cd47103b219beff7815dc8e742039c12cb.js
File Type .js
SHA256 8f7b48c9b0cb0702de08f98e8e4fb2cd47103b219beff7815dc8e742039c12cb
Size 300 KB
Entropy 4976
Formbook infection chain: from phishing to fileless execution
The attack unfolds through a well-defined chain of events, designed to increase stealth and the likelihood of successful infection.
The initial sample is distributed via malspam campaigns, one of the most common distribution techniques for Formbook, as documented by the ACN. The effectiveness of this first phase is not based on software vulnerabilities, but entirely on social engineering, designed to deceive and induce the user to take decisive action.
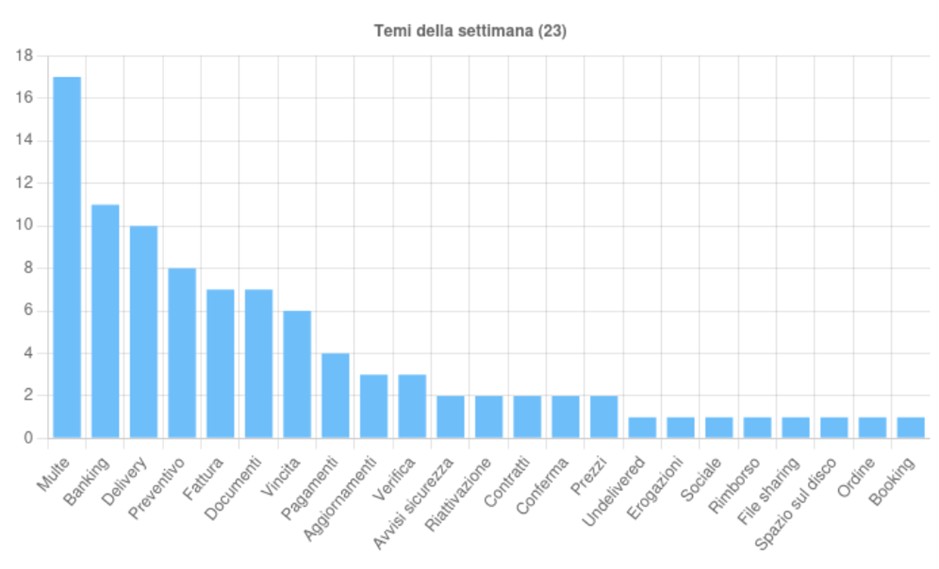
23 themes identified, exploited to spread malicious campaigns in Italy, during the week of September 20-26
The threat actor creates an email that appears to be a legitimate and urgent communication, such as a fake invoice, shipping document, or quote. The body of the message is usually short and encourages the victim to download an attachment or view an external document via a link.
The detected campaigns related to the Formbook malware distribute it via emails with compressed attachments such as ZIP, TAR, 7z.
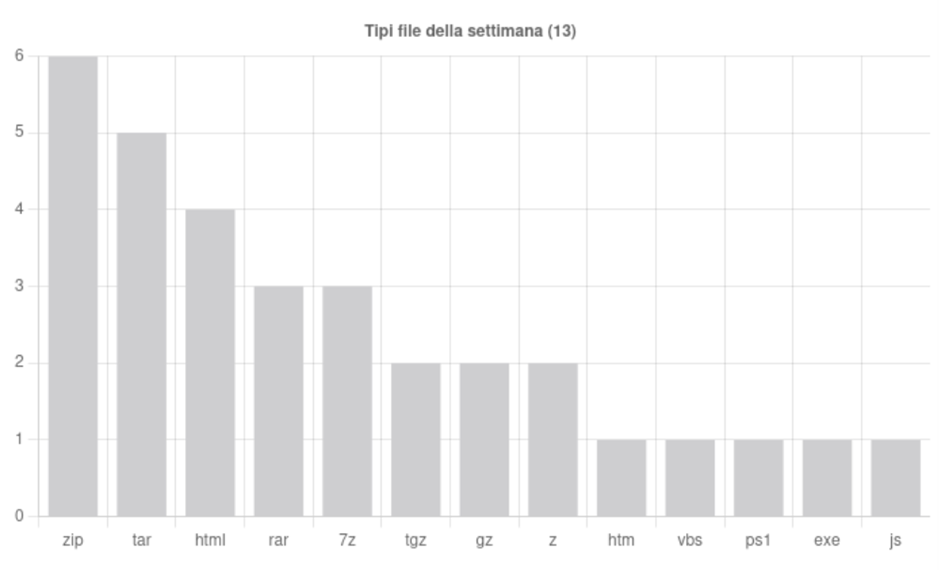
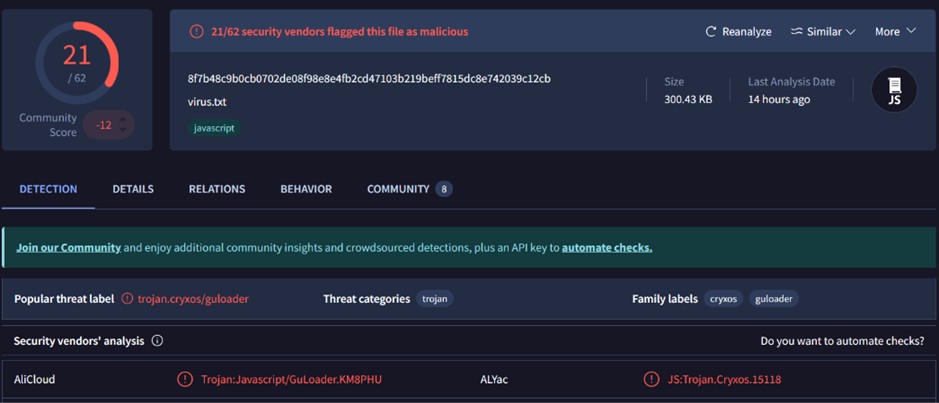
Once the archive is downloaded and extracted, we find ourselves faced with a text file with the .js extension. Analyzing the file’s hash using the main TI engines, we note that it is flagged as a Trojan.
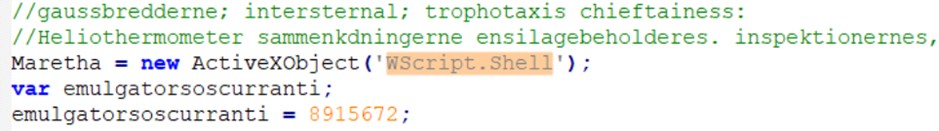
The source code is heavily obfuscated: after an initial formatting pass, the syntactic structure is readable, but the operational functions are deliberately hidden by meaningless variable names and code fragmentation. The analysis therefore focused on identifying features that enable interaction with the operating system. The key discovery was the extensive use of ActiveXObject to instantiate system COM objects:
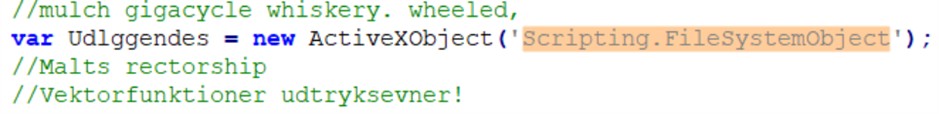
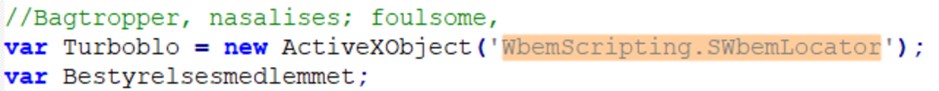
The main logic of the script is an assembly loop: it decodes and concatenates hundreds of small strings to build in memory the payload of the next stage, a PowerShell script, which will be saved in the %APPDATA% folder under the name “Plaidtry”.
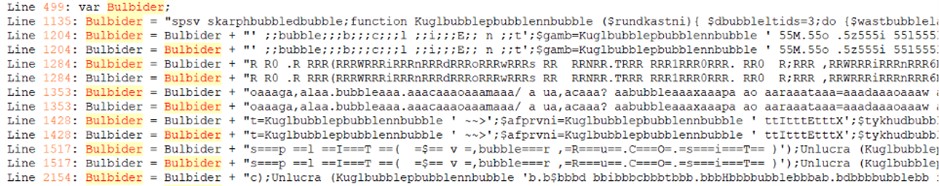

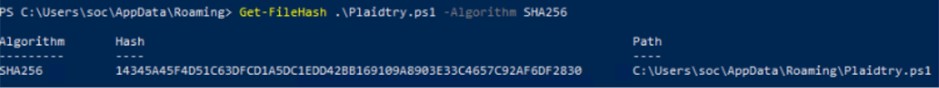
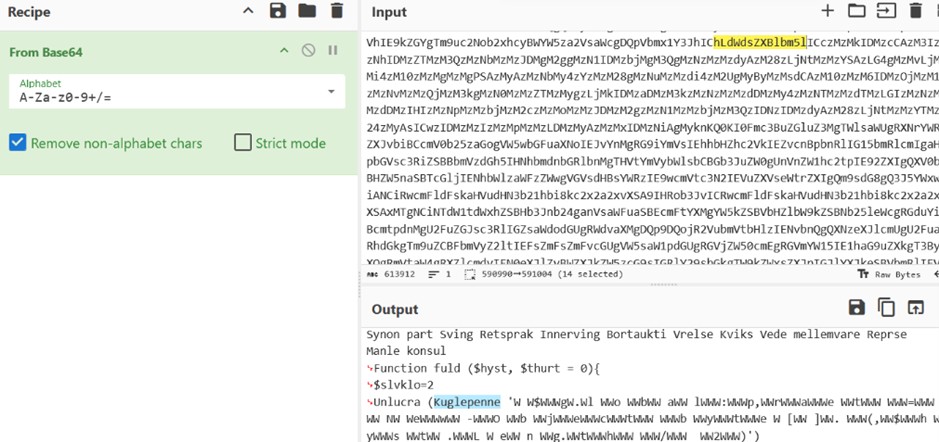
The Plaidtry.ps1 script is itself obfuscated, but with internal logic. It contains a de-obfuscation function ( Kuglepenne ) that reconstructs the actual commands by sampling characters from obfuscated strings. By running this function in a safe environment (PowerShell ISE), we were able to decode the commands step by step.
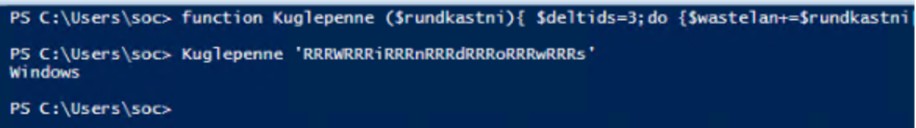
De-obfuscation example
The core of the script is the download logic. It sets a Firefox user agent to mask the request, then uses the Net.WebClient.DownloadFile method to download a payload from the previously decoded Google Drive URL. The file is saved as %APPDATA%Pidg.chl
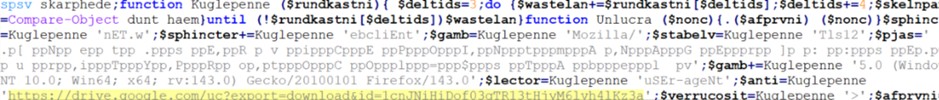
De-obfuscated PS script
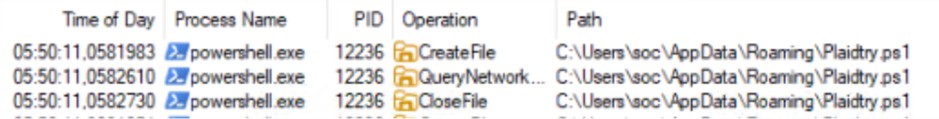
PROCMON Detail
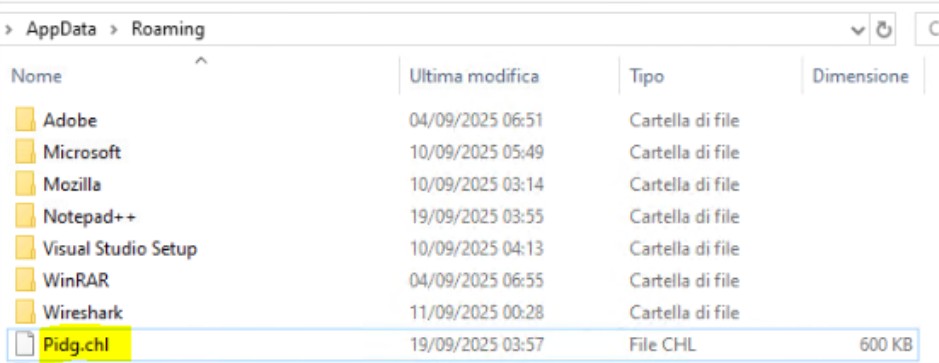
Folder Detail
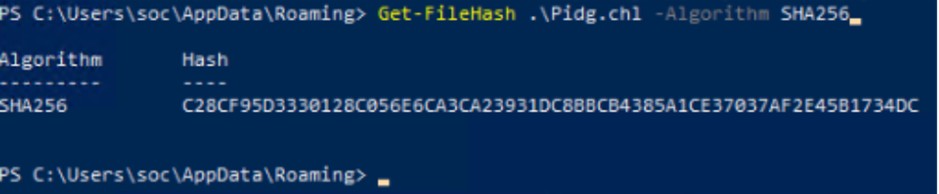
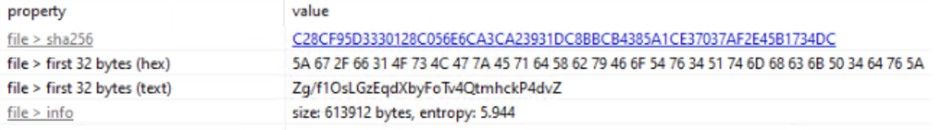
The Pidg.chl file is not an executable. It’s a text file containing a single, long string encoded in Base64. By using PowerShell to decode this string, we uncovered the final and most dangerous stage of the attack: a PE injector.
This script, also highly obfuscated, is designed to execute an .exe file without ever writing it to disk. Its key components are:
The script’s logic is as follows: it decodes the large Base64 string to reconstruct the bytes of the Formbook executable in memory. It then allocates a new region of memory within the running powershell.exe process, copies the Formbook bytes there, and finally starts a new thread at that location.
The result is that Formbook begins execution as a thread within a legitimate PowerShell process. At this point, the infostealer would begin its malicious activity: logging keystrokes, stealing credentials saved in browsers, capturing data from web forms, and sending it to another C2 infrastructure controlled by the attacker.
After reconstructing the infection chain and the techniques used by Formbook, it’s possible to outline the main mitigation and containment actions. The goal is to reduce the attack surface, block the spread, and preserve evidence for triage/IR.
Mitigation
Eradication
Prevention
Communication and disclosure
Analysis of this sample demonstrates a clear trend toward complex, fileless infection chains. The threat actor has invested significant effort in evading detection at every level: obfuscating the initial scripts, using legitimate cloud services to host the payloads, and finally injecting the actual malware into memory.
This layered methodology represents a significant challenge for traditional security solutions based on signatures and file analysis. It highlights the need for advanced, ongoing behavioral monitoring (XDR) capable of detecting anomalous activity by otherwise legitimate processes like PowerShell. Ultimately, the analysis allowed us to reconstruct the entire attack chain and extract valuable IoCs and TTPs to strengthen defense postures against similar threats.
The TTPs observed during the analysis were mapped onto the MITRE ATT&CK framework.
| Tactics | Technical ID | Technical Name | Description |
| Execution | T1059.007 | JavaScript | The initial infection starts from a JavaScript script. |
| Execution | T1059.001 | PowerShell | PowerShell is used as an intermediate stage for evasion and download. |
| Evasion Defenses | T1027 | Obfuscated Files or Information | Both the JS and PS scripts are heavily obfuscated to prevent parsing. |
| Evasion Defenses | T1562.001 | Disable or Modify Tools | The script attempts to disable services and check the status of Windows Defender. |
| Evasion Defenses | T1055 | Process Injection | The final FormBook payload is injected into a legitimate process in memory. |
| Execution | T1047 | Windows Management Instrumentation (WMI) | The JS dropper uses WMI to attempt to stealthily execute the PowerShell script. |
| Command and Control | T1105 | Ingress Tool Transfer | The loader downloads the final payload from an external web resource (Google Drive). |
| Command and Control | T1573.002 | Encrypted Channel: Asymmetric Cryptography | An HTTPS (TLS) connection is used to download the payload, encrypting the traffic. |
8f7b48c9b0cb0702de08f98e8e4fb2cd47103b219beff7815dc8e742039c12cb
C28CF95D3330128C056E6CA3CA23931DC8BBCB4385A1CE37037AF2E45B1734DC
14345A45F4D51C63DFCDD1A5DC1EDD42BB169109A8903E33C4657C92AF6DF2830
https://drive.google.com/uc?export=download&id=1cnJNHiDoF03QTRl3tHyM6lvh4lKo3a
Sources: ACN.GOV.IT , CERT-AGID
ELMI’s support in prevention and detection strategies
ELMI offers an integrated threat prevention, detection, and response program specifically designed to counter infostealer campaigns based on phishing and fileless execution. The solution combines integrated solutions, combining technology with a consulting and training approach.
Technical measures are the first line of defense against infostealers, requiring a multi-layered security architecture that integrates dedicated tools and processes. Within its Security Competence Center , ELMI offers a set of integrated solutions that cover the entire defense cycle.
The Security Competence Center also integrates Network Operation Center (NOC) services, dedicated to the management and continuous monitoring of the network, and Managed Services , which enable remote management of the IT infrastructure, allowing all company components to be configured and controlled remotely.
The strengths of ELMI’s Security Competence Center lie in its integrated approach to cyber incidents, its 24/7 operational availability across the country, and its ability to offer customized, comprehensive services, thus ensuring consistent and comprehensive protection.
The goal is not just to provide individual tools, but to build a coordinated defense together with the customer, capable of anticipating threats, accelerating detection and ensuring an immediate response.
The effectiveness of the entire process is guaranteed by the expertise of a multidisciplinary team , composed of specialized figures such as network engineers, system administrators and security analysts, with a solid operational background and an end-to-end vision of the IT infrastructure.
Effectively addressing cyber risk requires a structured, personalized, and progressive approach. ELMI’s support is divided into three key phases:
Thanks to an integrated consultative and operational approach, ELMI accompanies clients throughout the entire process of strengthening their security posture , ensuring a progressive reduction in risk and greater resilience against complex and constantly evolving threats.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
