Worldline payment terminals, widely used in Switzerland, have been exposed to an attack that allows anyone to gain complete control of the device in just a minute . The vulnerability affects the Worldline Yomani XR model, installed in supermarkets, cafes, repair shops, and other locations that accept credit cards.
Despite its seemingly secure appearance and sophisticated vandal-proof design, the terminal allows passwordless root access via the backdoor if an attacker gains physical access.
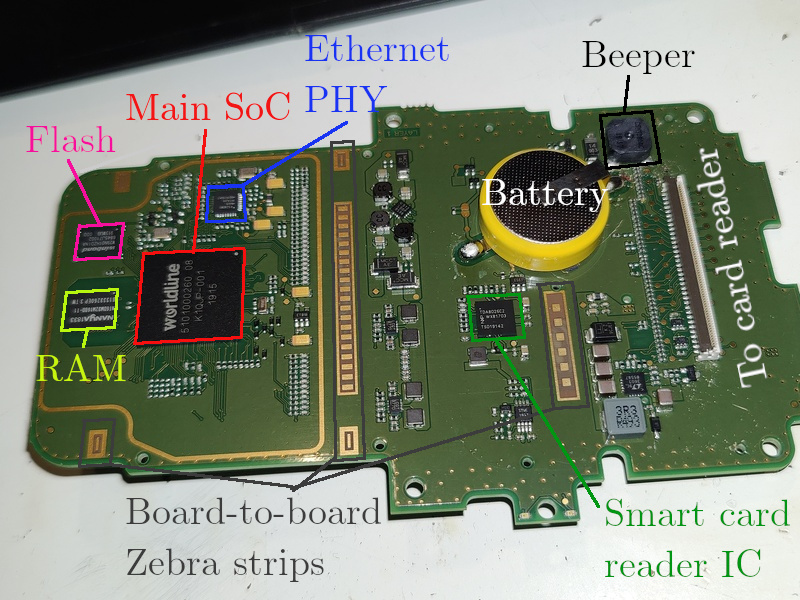
Analysis revealed an unused debugger connector on the terminal’s rear panel, hidden under a small flap.
After connecting a standard serial cable and booting the device, the specialist observed a standard Linux boot. The terminal was running kernel version 3.6, compiled with Buildroot in early 2023, with BusyBox utilities and uClibc libraries.
Once the boot process is complete, a login prompt appears on the serial console. Typing “root” immediately accesses the system shell without any authentication.
The device is physically designed for a high level of security. It uses a dual-core processor based on Arm architecture, a compact electronic board, and a sophisticated tamper detection system.
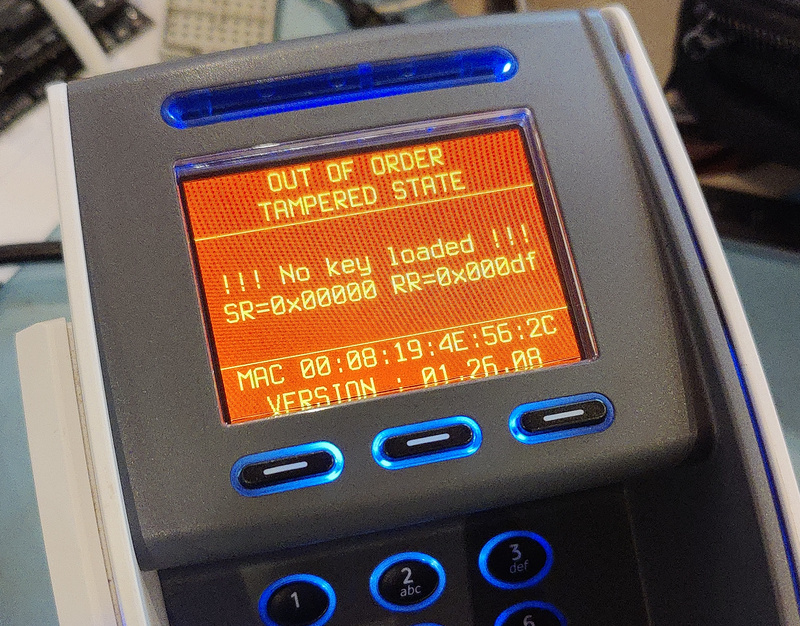
Attempts to open the case or puncture the circuit board activate safety mechanisms, including a permanent lock and a red screen . A separate battery maintains protection even in the event of a power outage.
However, the identified vulnerability bypassed all these measures: the debug interface was unprotected. This allowed access to an unencrypted Linux environment responsible for networking and business logic . A second, more secure environment, running on a dedicated processor, controls the keyboard, screen, and card reader and is activated only when security conditions are met.
Although it cannot be controlled directly via the Linux shell, accessing the first environment still poses a risk: malicious code can be injected, network traffic can be intercepted, or system updates can be interrupted.
At the time of publication, there have been no confirmed cases of user data being compromised due to this vulnerability, but experts emphasize the seriousness of the issue. The Worldline provider has been notified, and according to open sources, the issue has already been fixed in subsequent firmware versions.
However, the identified vulnerability points to a broader problem: similar flaws may also be found in terminals from other manufacturers. Unprotected service interfaces, left open for diagnostics or maintenance, often become a weak point even in carefully designed devices . Therefore, when designing and implementing large-scale payment solutions, it is important to consider not only strong encryption and vandalism protection, but also the elimination of any unauthorized access paths, including debug ports and test connectors.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
