
Redazione RHC : 12 December 2025 08:25
A recent study by Datadog Security Labs reveals an ongoing operation targeting organizations using Microsoft 365 and Okta for single sign-on (SSO) authentication. This operation uses sophisticated techniques to bypass security controls and steal session tokens.
As employees prepare for year-end performance reviews, this complex phishing scam has begun to spread, turning what appeared to be a pay raise into a cybersecurity threat.
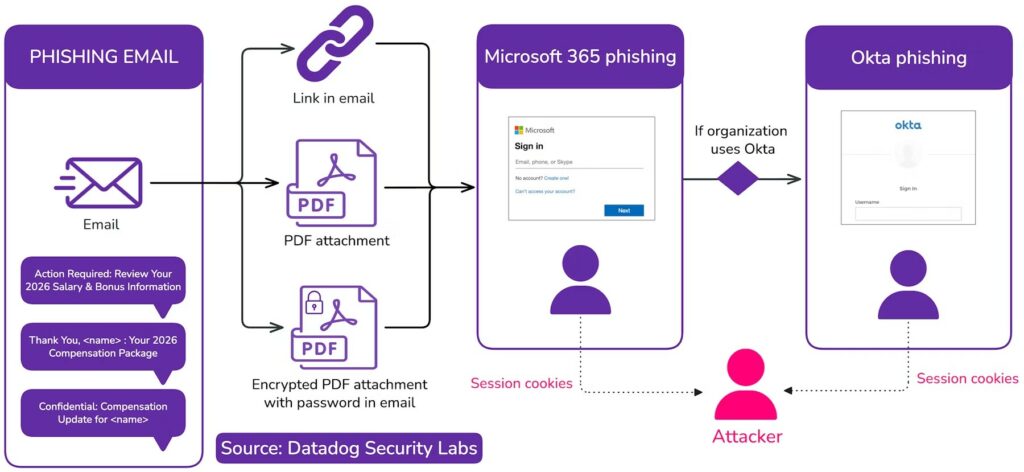
Since early December 2025, this campaign has been unscrupulously exploiting company benefits. Unsuspecting recipients have received emails disguised as official communications from human resources departments or payroll services, including ADP or Salesforce.
Subject lines are designed to spark immediate urgency and curiosity , using phrases like “Action Required: Review 2026 Salary and Bonus Information” or “Confidential: Compensation Update.”
According to the report , security researchers say that “phishing URLs include a URL parameter that indicates the targeted Okta tenant. It forwards any requests to the domain The original .okta.com, ensuring that all customizations to the Okta authentication page are preserved, making the phishing page appear more legitimate.
Some attacks use encrypted PDF attachments with the password provided in the email body— a classic tactic for bypassing email security scanners.
The threat becomes even more subtle if the victim accesses a fake Microsoft 365 login page. The malicious code stealthily examines browser traffic. Once it detects that the user is authenticating via Okta, using a specific JSON field called FederationRedirectUrl , the traffic is immediately intercepted.
Once the user enters their credentials, a client-side script called inject.js runs. It tracks keystrokes to capture usernames and passwords, but its primary goal is session hijacking.
The infrastructure behind these attacks is rapidly evolving.
Threat actors use Cloudflare to hide their malicious sites from security bots and are constantly refining their code.
 Redazione
Redazione