
Redazione RHC : 14 December 2025 22:36
A tool has been released that allows for the discreet monitoring of WhatsApp and Signal user activity using just a phone number. The tracking mechanism covers over three billion accounts and allows for the reconstruction of a person’s daily routine with alarming accuracy: the time of return home, periods of active smartphone use, hours of sleep, travel, and prolonged periods of disconnection from the internet. An additional side effect is accelerated battery and mobile data consumption, which goes unnoticed by the device owner.
The method is based on the specifications of message delivery protocols in popular messaging apps. The algorithm relies on service acknowledgements for receiving data packets and analyzes the round-trip time (RTT) . Applications automatically respond to these requests at a low network level, even before verifying the message content, ensuring that the other party receives measurable responses regardless of whether communication is actually in progress.
Anyone can send so-called “pings” to the victim’s device: the app responds instantly, but the response time varies significantly depending on the smartphone’s status, connection type, and reception conditions . Using Wi-Fi, a mobile network, an active screen, or standby mode creates different time profiles, easily identifiable with frequent measurements.
The vulnerability was first described by researchers at the University of Vienna and SBA Research in a paper published last year. The authors demonstrated that stealth requests can be sent at high frequency (up to fractions of a second) without triggering notifications, pop-ups, or interface messages , even if no conversation has ever taken place between the parties.
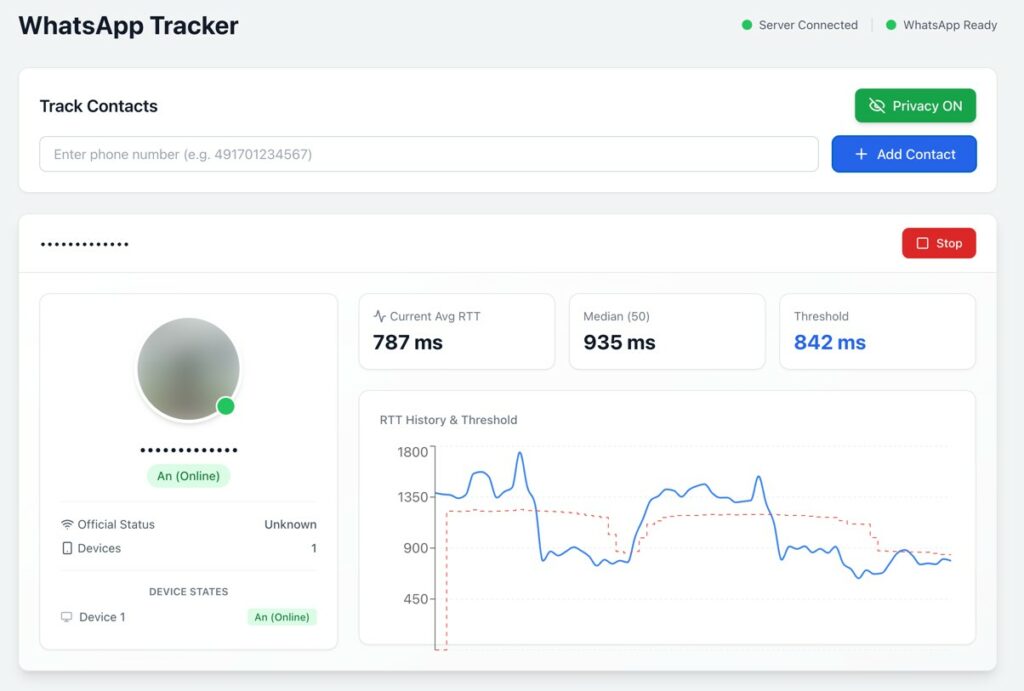
Now, these theoretical discoveries have been put into practice. A researcher known by the pseudonym gommzystudio has published a working proof-of-concept on GitHub demonstrating how easy it is to extract sensitive phone usage data. It clearly demonstrates how, using a single phone number, it’s possible to determine whether a device is active, inactive, or completely disconnected from the network, as well as identify additional behavioral indicators.
Another key trick is to send reactions to nonexistent messages. These requests aren’t visible to the recipient, but they still trigger automatic delivery confirmations. The app first reports receipt of a network packet and only then checks whether the associated message exists, ensuring the spy chain remains completely hidden.
Experiments have shown that such checks can be performed at intervals of approximately 50 milliseconds without leaving any traces in the user interface. However, the smartphone begins to consume significantly more power, and the amount of data transferred increases dramatically. The only way to detect this is to physically connect the device to a computer and analyze its internal logs.
Interpreting latencies opens up a wide range of observation possibilities. Low RTT values typically correspond to active phone use with the screen on and a Wi-Fi connection. Slightly slower responses indicate active mobile network activity. High latencies are typical of idle mode on wireless access, while very high latencies indicate sleep mode on a cellular connection or poor reception. A lack of response indicates airplane mode or a complete shutdown, while significant fluctuations in response time indicate the owner has moved.
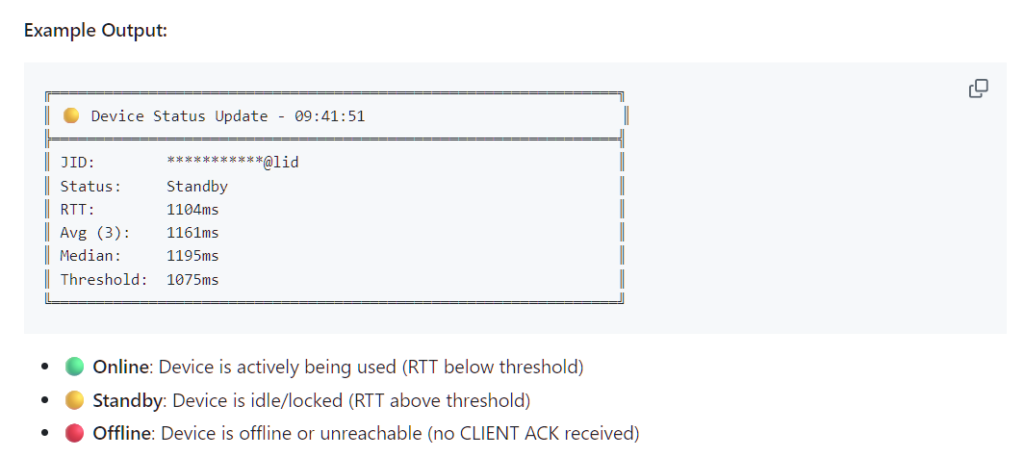
By accumulating these measurements, we can build a detailed behavioral picture. Stable Wi-Fi readings typically coincide with staying at home, long periods of inactivity with sleeping, and characteristic mobile network patterns indicate travel and outings.
The repository containing the tool quickly attracted the attention of the community: in a short time , the project accumulated hundreds of “likes” and dozens of forks . Although the author emphasizes the research and educational nature of the work, anyone can download and use the program, making the potential for abuse quite real.
The attack’s impact on device battery life deserves special attention. Initial research has revealed that an attacker can almost completely drain a device’s battery in just a few hours without logging in to either the account or the device itself . Under normal use, a typical smartphone loses less than 1% of its battery life per hour. However, in WhatsApp tests, the iPhone 13 Pro consumed approximately 14% of its battery in the same period, the iPhone 11 18%, and the Samsung Galaxy S23 approximately 15%.
Signal proved more resilient by implementing a confirmation rate limit. Under similar conditions, the battery drained only 1% per hour, as the system blocked excessive requests. WhatsApp did not have such limits at the time of the experiments, making the attack significantly more effective.
As of December 2025, the vulnerability remains exploitable in both WhatsApp and Signal.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
 Redazione
Redazione