
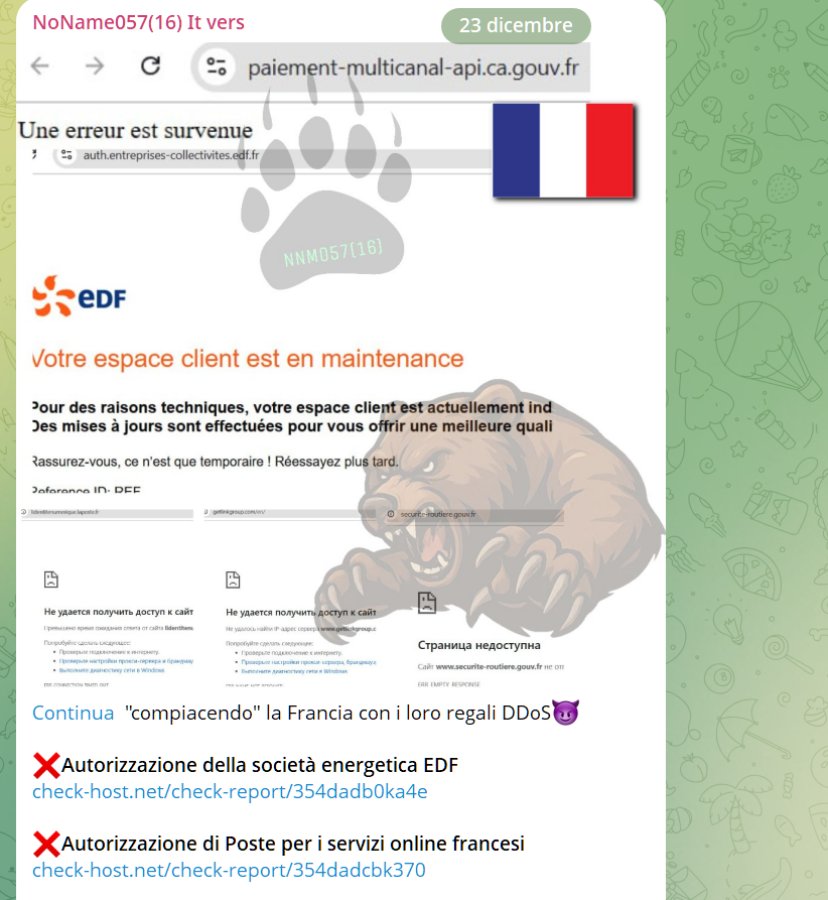
According to internal sources at RedHotCyber , the digital offensive that is causing problems for the National Postal System in France has been officially claimed by the pro-Russian hacker collective NoName057(16).
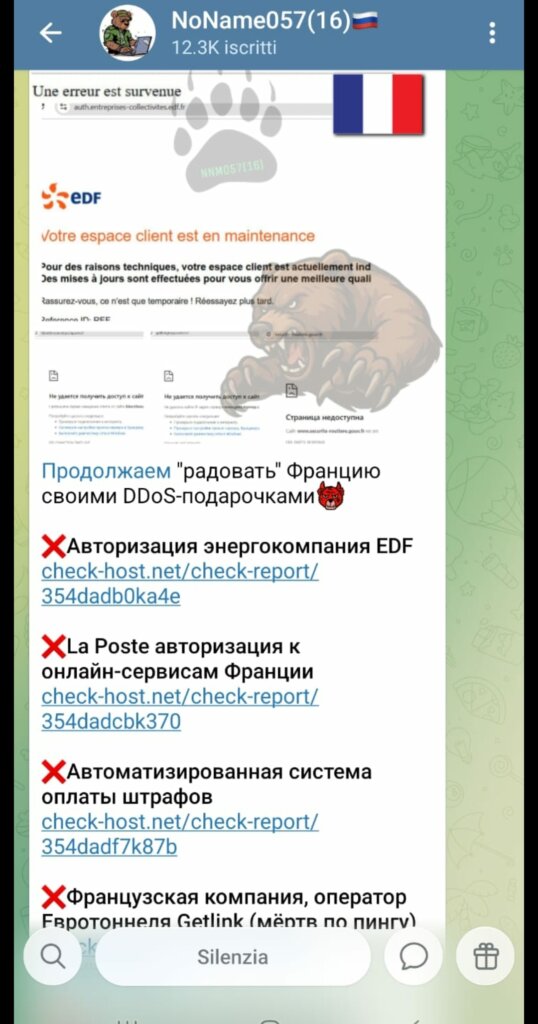
Analysts confirm that the action is part of a targeted disruption strategy aimed at hitting essential services in European countries, using server overload techniques to bring national logistics to their knees.
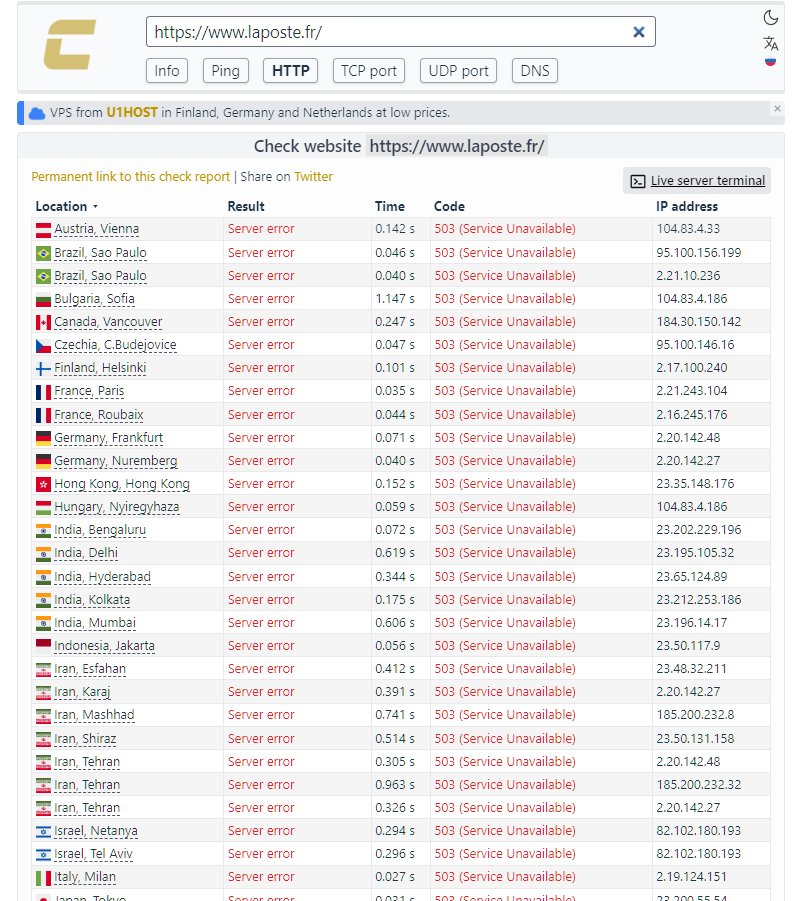
The operational disruption is critically affecting the management of Banque Postale , the group’s financial arm. Users are unable to access their accounts via online banking, a disruption that, combined with difficulties with digital payments, is creating significant tensions right in the middle of the holiday shopping season.
Despite the chaos created on web portals, La Poste management has issued a reassuring statement regarding the protection of sensitive data. Currently, there is no evidence of personal information exfiltration or customer database breaches , suggesting that the attack was primarily designed to disrupt service, not for identity theft.
The most complex situation is in the logistics and shipping sector. The parcel tracking system is offline, making it impossible for citizens to track their orders. In many areas, including several in the capital Paris, the collection and delivery of goods have been partially suspended, causing a backlog of shipments in warehouses.
The authorities across the Alps see this incident as yet another chapter in Russia’s so-called “hybrid warfare . “
Just ten days ago, the French Ministry of the Interior was the target of a similar cyber intrusion, confirming an escalation in the digital conflict aimed at undermining citizens’ trust in public institutions.
For those who physically visit post offices, the experience is marked by long waits and manual procedures. Many branches have had to suspend operations due to technical issues with their systems, reverting to analog working methods that drastically slow down the provision of every service, from registered mail to financial services.
This DDoS (Distributed Denial of Service) attack struck with surgical timing, exploiting the traffic peak just before Christmas . NoName’s goal appears to be to maximize media and social impact by targeting a symbol of French daily life at a time of maximum logistical vulnerability for the entire country.
While security experts work to restore full functionality of systems, the threat of new waves of attacks remains high . The resilience of France’s critical infrastructure is now under scrutiny, highlighting the need for more robust defense protocols against organized groups operating for political propaganda purposes through cyber sabotage.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
