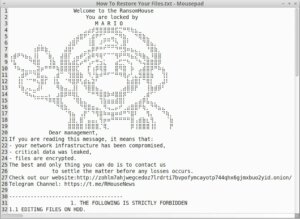
Researchers at Check Point, a pioneer and global leader in cybersecurity solutions, have discovered a phishing campaign in which attackers pose as fil...
23/12/2025
The Red Hot Cyber community is made up of a collection of people who actively collaborate, with different roles, to create targeted content focused on information security and technology, with the aim of spreading awareness and culture, and generating a mentality of widespread attention to IT risk and technology in general. All free of any political contamination.
| Nessun autore trovato con i filtri selezionati. |