
Some spyware producer is probably doing gymnastics… tearing their hair out. But it’s the usual charade: someone finds, someone cashes in, someone integrates, and then the researcher on duty comes along to ruin the party—for ethics or some other theatrical reason.
A security flaw was recently discovered in WhatsApp that allows zero-click remote code execution (RCE). This vulnerability is already being actively exploited by attackers on Apple platforms, including iOS, macOS, and iPadOS.
Researchers at DarkNavyOrg have discovered a flaw by exploiting two vulnerabilities, CVE-2025-55177 and CVE-2025-43300, in a proof-of-concept. This weakness allows devices to be compromised silently, without requiring any user intervention.
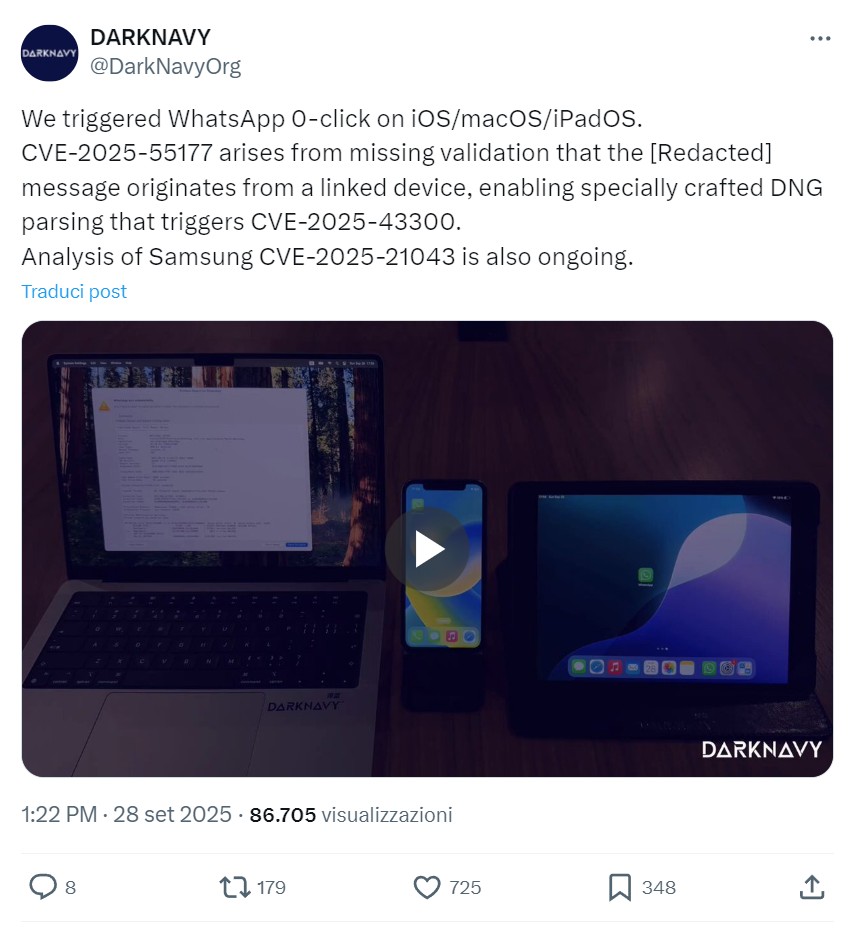
Victims receive a malicious DNG image file via WhatsApp and, after automatic analysis, gain complete control of the device. Exploitation begins with CVE-2025-55177, a critical flaw in WhatsApp’s message handling logic.
By default, WhatsApp is unable to determine whether an incoming message actually originates from an authorized connected device. An attacker can bypass initial security checks and include a spoofed DNG file in the victim’s chat history by modifying the message’s source.
Because WhatsApp processes messages automatically, even before the user views them, the payload is delivered without notifying the victim. Once delivered, the malformed DNG payload triggers the second vulnerability, CVE-2025-43300. This vulnerability resides in the DNG file parsing library, where improper bounds checking causes a memory corruption error.
When WhatsApp’s media processing engine attempts to parse the malformed DNG structure, it overwrites critical memory regions, allowing an attacker to hijack the execution flow and run arbitrary code on the target device. Successful exploitation results in complete device compromise, and in this scenario, attackers can perform all the typical spyware actions:
Victims have no ability to inspect or block the malicious payload before execution, and standard endpoint protections may not flag the malformed DNG file as malicious.
DarkNavyOrg is currently investigating associated zero-click exploits. A Samsung-related vulnerability (CVE-2025-21043) has been identified by the group as currently under investigation. This recent series of discoveries highlights the ongoing difficulty in safeguarding sophisticated file parsers within cross-platform messaging apps, where even secure formats like DNG can be exploited as attack channels.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
