
Un nuovo infostealer emerge dalle underground criminali e il suo nome è “123 | Stealer”. L’autore di questo software è un hacker che si nasconde sotto lo pseudonimo di koneko. Offre in affitto il malware per 120 dollari al mese, presentandolo come uno strumento universale per il furto di informazioni riservate.
Il programma è progettato con particolare attenzione alle prestazioni e alla mobilità. Secondo l’autore, “123 | Stealer” è scritto in C++, non richiede librerie aggiuntive e le sue dimensioni sono di circa 700 kilobyte. Il malware viene distribuito come un file eseguibile autonomo compatto, il che ne complica il rilevamento da parte degli antivirus .
Tuttavia, l’utilizzo di questo strumento presenta alcune sfide tecniche. Per funzionare, l’aggressore deve configurare un proprio server proxy basato su Ubuntu o Debian. Questo requisito non solo aumenta il livello di stealth e rende più difficile tracciare il traffico di comando e controllo, ma richiede anche che l’utente disponga di competenze tecniche di base.
Le funzionalità di “123 | Stealer” includono il furto di dati da browser popolari come Chrome e Firefox . Il malware è in grado di estrarre password, cookie e cronologia di navigazione salvati. Di particolare interesse è la funzione mirata al furto di wallet di criptovalute, che evidenzia la rilevanza di tali attacchi nel contesto del crescente interesse per le risorse digitali.
Inoltre, il programma può intercettare processi e file in esecuzione sul dispositivo infetto, nonché interagire con le estensioni del browser. Il pannello di controllo supporta oltre 70 estensioni per browser basati su Chromium e Gecko, inclusi programmi di messaggistica istantanea e altre piattaforme popolari.
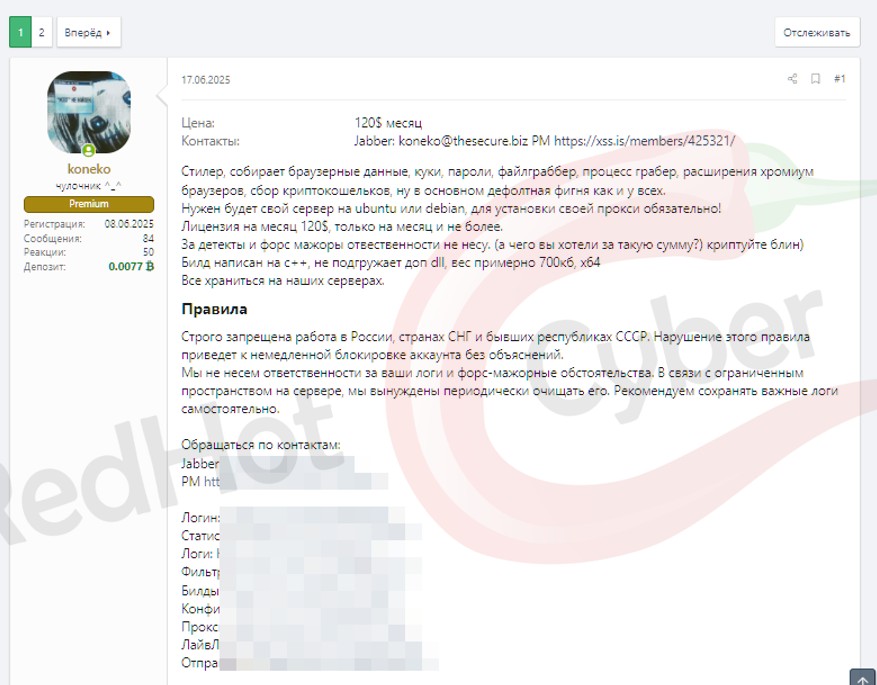
Di seguito quanto riportayto nel forum underground XSS in lingua russa da parte degli sviluppatori.
123 Stealer raccoglie i dati del browser, i cookie, le password, il file grabber, il process grabber, le estensioni del browser chrome, la raccolta di portafogli di criptovalute, e per lo più cose predefinite come tutti gli altri.
È necessario un proprio server su ubuntu o debian, per installare il proxy è obbligatorio!
Licenza per un mese 120$, solo per un mese e non di più.
Per i rilevamenti e le cause di forza maggiore la responsabilità non è responsabile. (e cosa volevate per una tale somma?) cryptuite damn)
La build è scritta in c++, non carica dll aggiuntive, peso circa 700kb, x64
Tutto memorizzato sui nostri server.
Regole
È severamente vietato lavorare in Russia, nei paesi della CSI e nelle ex repubbliche dell’URSS. La violazione di questa regola porterà al blocco immediato dell’account senza alcuna spiegazione.
Non siamo responsabili per i vostri log e per cause di forza maggiore. A causa dello spazio limitato sul server, siamo costretti a pulirlo periodicamente. Vi consigliamo di salvare autonomamente i log più importanti.
L’emergere di “123 | Stealer” è l’ennesima conferma dello sviluppo attivo del mercato del malware basato sul modello “malware as a service” (MaaS). Nell’ambito di questo schema, gli autori forniscono accesso a strumenti di spionaggio informatico e furto di informazioni a un canone mensile. Strumenti già noti come RedLine e LummaC2 vengono distribuiti in modo simile .
La base di tali programmi è la raccolta di dati riservati, che vengono poi venduti o utilizzati per hackerare account, commettere frodi e altri attacchi. Tuttavia, le capacità di “123 | Stealer” rimangono incerte: nella comunità underground, solo gli strumenti che hanno dimostrato la loro efficacia nella pratica e si sono guadagnati la fiducia dei criminali informatici sono i più richiesti.
Gli esperti di sicurezza informatica sottolineano che la diffusione di tali programmi abbassa la soglia di accesso all’ambiente criminale informatico. Anche gli utenti con conoscenze tecniche minime possono lanciare attacchi che utilizzano metodi avanzati di furto di informazioni.
Se le affermazioni di “123 | Stealer” fossero vere, la sua architettura modulare e il supporto per più piattaforme potrebbero effettivamente rappresentare una seria minaccia sia per gli individui che per le organizzazioni. È ancora troppo presto per valutare il reale impatto del nuovo malware, ma aziende e privati sono già invitati a essere estremamente vigili, ad aggiornare le proprie misure di sicurezza e a monitorare costantemente eventuali segnali di fuga di dati.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…