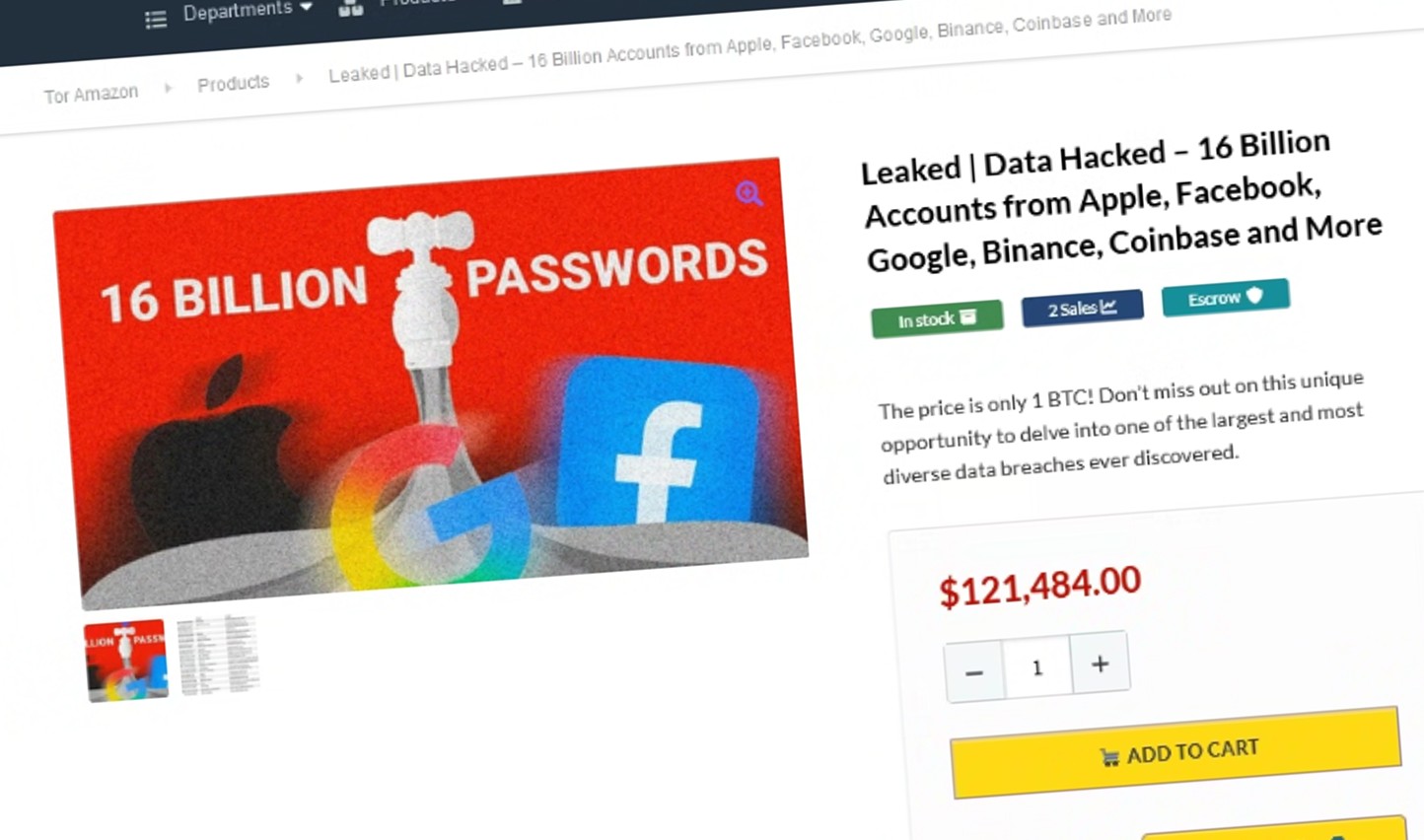
The Darklab team, Red Hot Cyber‘s community of threat intelligence experts, has identified an ad on the dark web marketplace “Tor Amazon”, the criminal counterpart of the popular e-commerce site on the clear web. The listing offers an unprecedented archive: 16 billion compromised credentials from leading platforms such as Apple, Facebook, Google, Binance, Coinbase, and many others.
The listing, priced at 1 Bitcoin (about $121,000), represents one of the largest and most diverse collections of data ever to appear in the underground circuits.
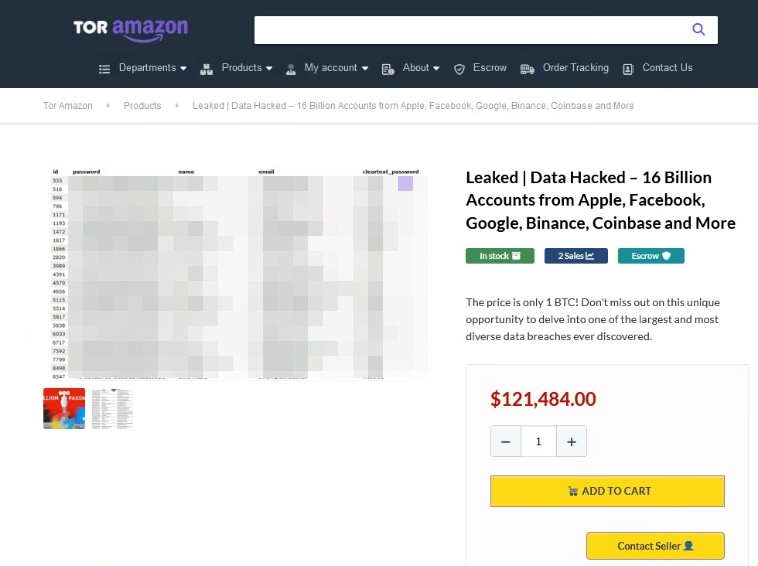
According to Darklab’s analysis, the packet does not originate from a single data breach, but from 30 distinct collections generated through malware campaigns.
The malicious actors would have exploited corrupted files and social engineering techniques to infect victims’ devices, harvesting credentials primarily from users who reused weak passwords or did not activate advanced security measures.
This feature makes the dataset particularly interesting from an investigative perspective, as it allows us to observe not only platform vulnerabilities, but also users’ bad habits and the real impact of the malware on daily security.
Selling on Tor Amazon reflects the growing threat of criminal marketplaces, which replicate the typical logic of legitimate e-commerce: escrow systems for transactions, buyer feedback, post-sales support.
For cybercriminals, data represents an immediately monetizable resource through:
For researchers and analysts, however, the dataset constitutes a precious source for:
The discovery made by Darklab highlights how the dark web criminal ecosystem is evolving towards increasingly structured and competitive models.
At the same time, it reiterates the need to adopt minimum protection measures—password managers, multi-factor authentication, continuous monitoring of data leaks—which remain the most effective defenses against threats of this magnitude.
In this scenario, the monitoring and analysis conducted by communities like Darklab proves crucial for uncovering phenomena that, if ignored, risk compromising entire digital ecosystems.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
