
Following the case of the 568 endpoints of an Italian industrial machinery company, another compromised access related to an Italian software engineering company has ended up for sale on an underground forum frequented by Initial Access Brokers and ransomware actors.
The listing, posted by the user spartanking, offers full access to a server with local administrator privileges and remote control via AnyDesk.
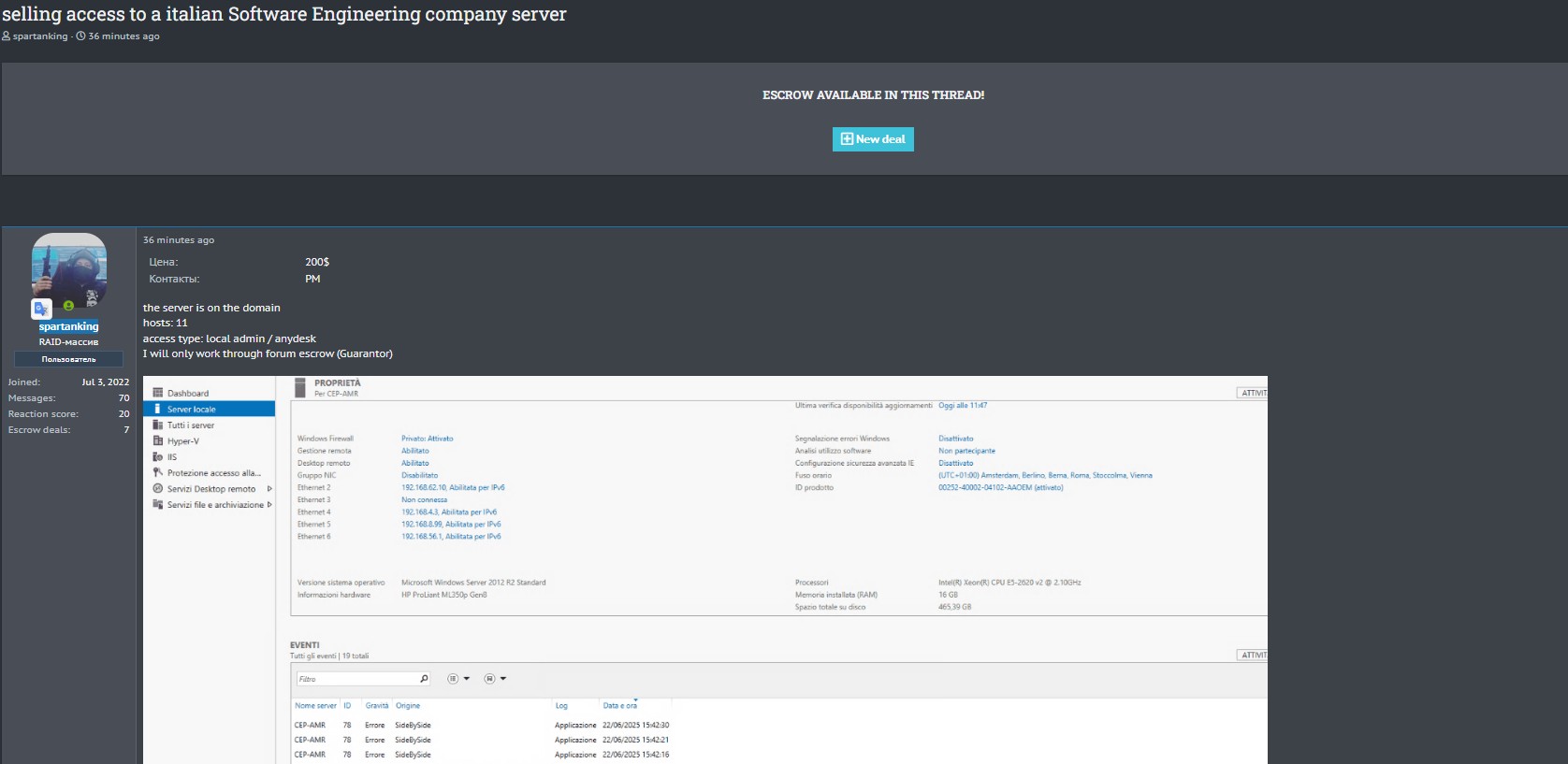
The ad clearly states that the compromised system is joined to an Active Directory domain. As stated in the post:
The access would therefore allow elevated privileges on at least one server. In a screenshot, the compromised system is noted to be aMicrosoft Windows Server 2012 R2 Standard installed on anHP ProLiant ML350p Gen8, with 16 GB of RAM and 465 GB of disk space.
The images accompanying the announcement provide several clues:
Although access is offered for sale at a relatively low price ($200), which does not reduce its potential impact. Low-cost access is often purchased by:
The continuous publication of Italian corporate access shows that our Country is by no means immune to the practices of Initial Access Brokers. Tech SMEs, often convinced that they are “too small to be a target”, are instead vulnerable and attractive.
The spartanking case, with its 7 active escrows, also confirms that these sellers are building a lasting and profitable reputation, a sign that the Italian access market on the dark web is anything but marginal.
That understanding before an Initial Access Broker is observing or analyzing a company network is today one of the most valuable pieces of information for preventive defense. These actors sell access ports that are already open, and knowing in advance if you have ended up on their radar allows you to strengthen weak points, segment the network, update access policies and implement timely countermeasures. Waiting for access to be sold – and then perhaps used by a ransomware group – means intervening when the damage is already in progress.
This is where Cyber Threat Intelligence (CTI) comes into play, which does not limit itself to observing the past, but analyzes patterns, behaviors, reputation and movements of actors in the gray areas of the web. Threat intelligence allows companies to monitor marketplaces, underground forums, Telegram channels and the dark web to detect suspicious sales, data leaks or compromised credentials. In an era where SMBs are being targeted as often as large companies, CTI is not a luxury for the few, but a necessity for all.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
