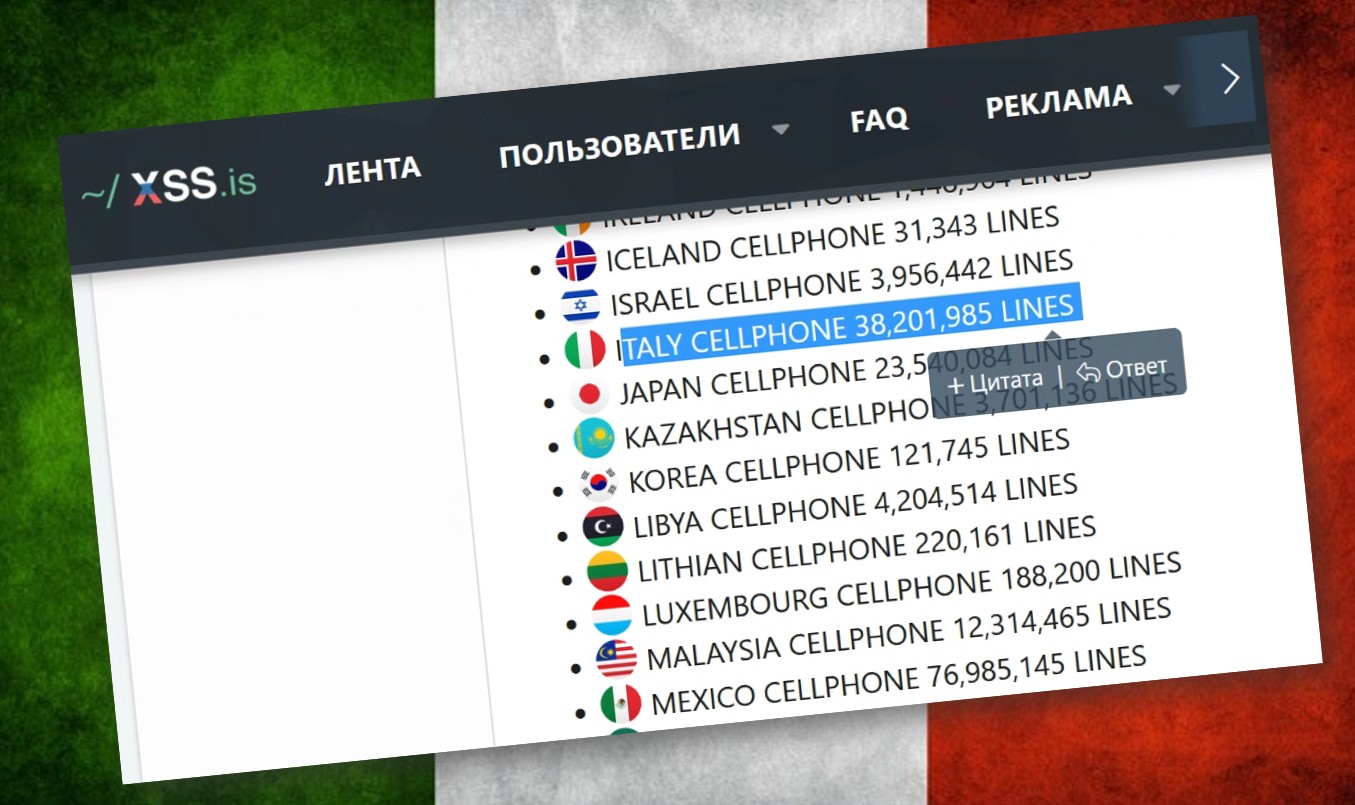
Seven out of ten Italians have their phone numbers included in this database. But what does it mean to have such a large number of phone numbers concentrated within a given territory today?
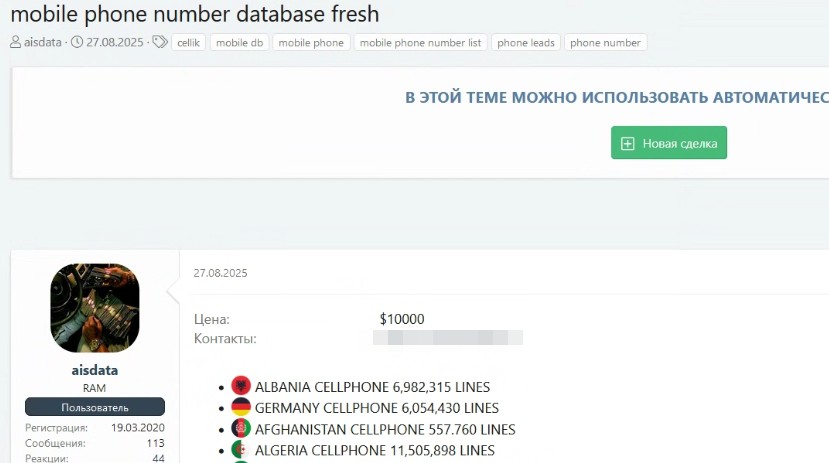
A new announcement on the Russian-language underground XSS forum, accessible upon submission in its onion version, has raised particular concern within the cybersecurity community. In the post, DarkLab researchers revealed the sale of a huge database containing over 38 million phone numbers of Italian citizens, with a price tag of several thousand dollars.
The availability of such an archive poses a real risk, since even the phone number alone, when combined with basic information such as location, can be exploited to orchestrate Smishing campaigns, which are SMS scams that trick users into clicking malicious links or providing sensitive data.
Smishing attacks are distinguished by their ability to appear extremely credible: criminals can impersonate well-known entities, banks, couriers, or service companies, convincing victims to interact with messages that appear legitimate. With such a large database, campaigns could be targeted to specific geographic areas, increasing the effectiveness of the scam.
Not only ordinary citizens, but also major companies and organizations are at risk of being affected. Knowing the phone numbers of employees or customers, attackers could create fake websites that perfectly imitate company portals to steal credentials, banking details, or other confidential information. A concrete example could involve a bank sending fake password update SMS messages, or a fake package delivery confirmation from a well-known courier.
The risk is twofold: on the one hand, the direct theft of victims’ personal and financial data, and on the other, the possibility of accessing critical company accounts, with devastating consequences for the information security and reputation of the companies involved.
Paragraph attention must be paid to the most vulnerable groups, such as the elderly and young people, who often lack full awareness of the risks associated with the digital world. Their lack of experience or sensitivity to these threats makes these segments of the population prime targets for cybercriminals.
The case of the database for sale on the XSS forum once again reiterates the importance of developing a widespread cybersecurity culture. Do not open suspicious links, never provide personal information via SMS, and always verify communications with official sources are fundamental rules for protecting yourself from this type of fraud.
Smishing is a form of cyber attack that uses SMS as a fraud vehicle. The term comes from the combination of “SMS” and “phishing” and represents one of the most widespread and insidious threats of recent years.
In practice, victims receive a text message that appears to come from a trusted source, such as a bank, courier, government agency, or online service. The SMS usually contains a link to a fake website, deliberately created to look like a legitimate one.
Once the link is clicked, the user may be tricked into entering sensitive data (such as credentials, one-time passwords, credit card numbers) or downloading malware that compromises the device. In other cases, the SMS prompts the user to contact a fraudulent phone number where a fake operator attempts to extort information.
The effectiveness of Smishing lies in the trust many users place in SMS, which is still considered a “secure” and direct channel. This very perception leads many people to underestimate the danger, making attacks extremely profitable for criminals.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
