
Gli analisti di Citizen Lab hanno segnalato che oltre 20 app VPN presenti sul Google Play Store presentano gravi problemi di sicurezza che minacciano la privacy degli utenti e consentono la decrittazione dei dati trasmessi. In totale, queste app sono state scaricate 972 milioni di volte.
Gli esperti affermano che i provider VPN che distribuiscono app problematiche sono chiaramente collegati tra loro, sebbene affermino di essere aziende separate e utilizzino vari metodi per nascondere la vera situazione.
Il rapporto di Citizen Lab si basa su ricerche precedenti che hanno individuato collegamenti tra tre provider VPN presumibilmente con sede a Singapore: Innovative Connecting, Autumn Breeze e Lemon Clove. Tutte queste aziende erano state precedentemente collegate a un cittadino cinese e ora i ricercatori hanno trovato ulteriori sovrapposizioni tra le app, nonché collegamenti ad altre app VPN e ai loro sviluppatori.
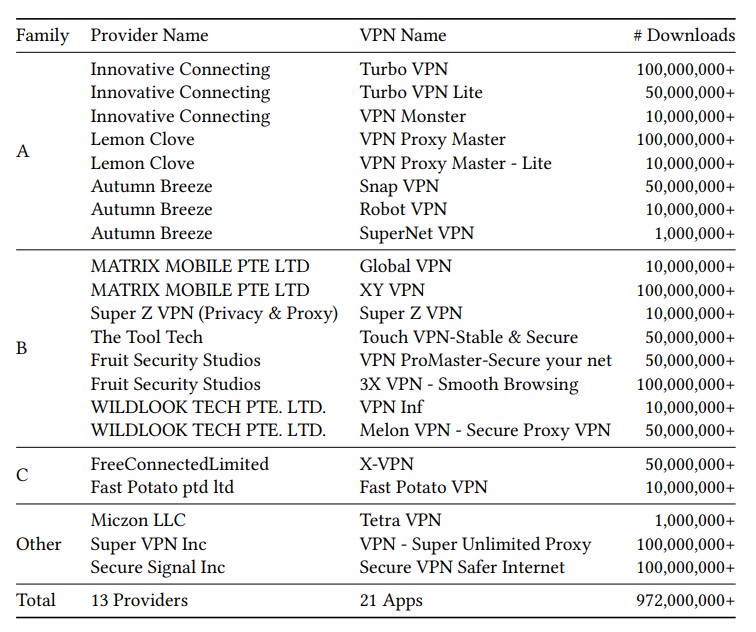
Secondo il rapporto, otto app VPN create da Innovative Connecting, Autumn Breeze e Lemon Clove condividono codice, dipendenze e password hard-coded comuni, consentendo potenzialmente agli aggressori di decrittografare tutto il traffico utente. Insieme, queste app hanno più di 330 milioni di installazioni sul Google Play Store.
Tutte e tre le aziende, precedentemente collegate a Qihoo 360 (un’azienda cinese di sicurezza informatica sanzionata dagli Stati Uniti nel 2020), offrono servizi VPN e si affidano al protocollo Shadowsocks, originariamente progettato per aggirare il Great Firewall cinese.
I ricercatori sottolineano che il protocollo utilizza la crittografia simmetrica ed è vulnerabile a vari attacchi a causa dell’uso di cifrari obsoleti e password hard-coded. Inoltre, la sua interazione con il sistema di tracciamento delle connessioni del sistema operativo consente agli aggressori di assumere il controllo delle connessioni delle vittime.
Otto applicazioni (Turbo VPN, Turbo VPN Lite, VPN Monster, VPN Proxy Master, VPN Proxy Master – Lite, Snap VPN, Robot VPN e SuperNet VPN) supportano i protocolli IPsec e Shadowsocks, presentano inoltre sovrapposizioni significative nel codice e utilizzano vari meccanismi per l’anti-analisi e l’aggiramento dei controlli di sicurezza automatici.
Tutte le app esaminate dai ricercatori erano vulnerabili ad attacchi di manomissione della connessione e di iniezione di pacchetti. Tutte raccolgono segretamente informazioni sulla posizione dell’utente, utilizzano una crittografia debole e contengono la stessa password hard-coded per la configurazione di Shadowsocks.
Utilizzando questa password, Citizen Lab ha scoperto che tutti e tre i provider VPN che offrono queste app utilizzano la stessa infrastruttura, il che conferma ulteriormente la connessione tra loro.
Si noti che un altro gruppo di fornitori (Matrix Mobile PTE LTD, ForeRaya Technology Limited, Wildlook Tech PTE LTD, Hong Kong Silence Technology Limited e Yolo Mobile Technology Limited) potrebbe essere associato al trio sopra menzionato, dato l’utilizzo di protocolli identici, codice simile e offuscamento.
Si è scoperto che le loro soluzioni VPN, scaricate più di 380 milioni di volte, sono vulnerabili ad attacchi di manomissione della connessione, contengono password offuscate e si connettono allo stesso set di indirizzi IP.
Altri due provider, Fast Potato Pte. Ltd e Free Connected Limited, offrono client VPN che si basano sulla stessa implementazione di protocollo proprietario.
Secondo Citizen Lab, i problemi di sicurezza e privacy identificati nelle app studiate hanno un impatto diverso sugli utenti. Ad esempio, potrebbero violare la fiducia e la privacy raccogliendo furtivamente dati sulla posizione e potrebbero esporre le persone al rischio di intercettazione e modifica del traffico.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…