
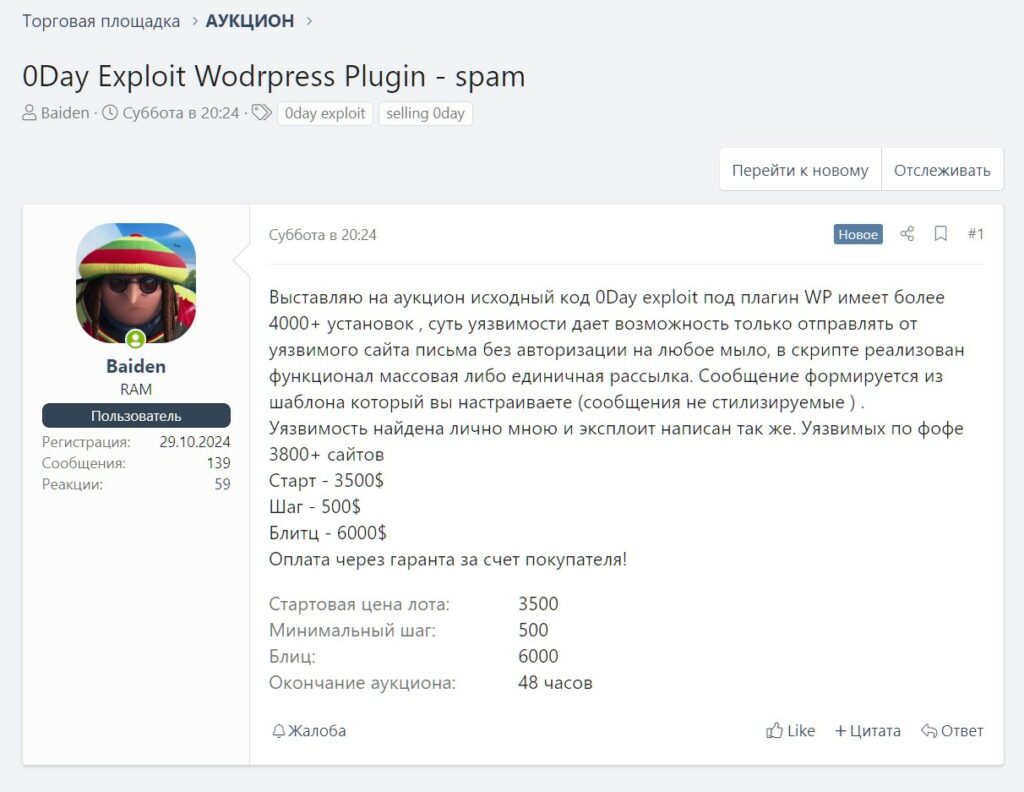
On one of Russia’s most popular forums for buying and selling vulnerabilities and attack tools, the thread appeared as a standard commercial ad, but the content is anything but trivial. The user who goes by the username “Baiden” is offering for sale the source code of an alleged zero-day bug for a WordPress plugin—a flaw that, according to the author, affects thousands of installations.
The post states that the vulnerability allows for ” unauthorized ” emails to be sent from vulnerable sites, either individually or in bulk, with messages generated from a configurable template.
The author claims to have personally discovered the flaw and written the exploit; he estimates that around 3,800-4,000 sites were affected . The offer is structured like an auction: starting price is $3,500, with minimum bids of $500, and a “blitz” option at $6,000, with payment via a guarantor required and paid by the buyer.
The ad lasts 48 hours.
The message format is typical of those markets: numbers for trading leverage, a guarantee of anonymity, and payment methods designed to minimize the risk of fraud between anonymous sellers and buyers. But beyond the form, what’s worrying is the very nature of the item for sale: the source code for an exploit that, in the wrong hands, could be transformed into a tool for large-scale campaigns.
Vulnerability trading isn’t a single thing: it’s an ecosystem. On one side, there are researchers—some more “ethical,” others solely interested in profit—who discover vulnerabilities. Then there’s a network of brokers, forums, and private channels that connect discoverers and buyers: cybercriminals, groups offering commercial attack services, and, in extreme cases, actors with state resources. Prices are determined based on concrete factors: how many installations are potentially exploitable, how easy it is to use the exploit, the level of impact, and how likely it is that the vulnerability will remain undetected.
Selling the source code— not just a PoC, but the complete implementation— increases the value of the offering, as it allows the buyer to adapt, automate, and integrate the exploit into malicious campaigns. Forums like XSS act as marketplaces where these transactions take place, often with escrow and reputation mechanisms built over time to “secure” agreements between anonymous parties.
An exploit that allows emails to be sent from a vulnerable site has immediate and tangible impacts. A compromised site sending messages under the legitimate domain name dramatically increases the success of phishing operations: the sender appears authentic, spam filters are more easily bypassed, and the potential victim rate increases. This type of breach can tarnish the domain’s reputation, blacklist IPs and names, and compromise the deliverability of legitimate communications for weeks or months.
The emails may contain links to credential theft pages, malware attachments, or instructions for targeted fraud. But the damage doesn’t stop with a single campaign: a compromised site can become a launching point for attacks on customers, partners, or service users, and may harbor backdoors that allow subsequent access. If the site contains personal data or sensitive information, the exploit can also be used to exfiltrate that data, creating legal and financial repercussions for the owner (think, for example, of the GDPR in Europe).
The appearance of such an announcement is a wake-up call. The exploit doesn’t have to be “out there” to take action: the mere fact that someone claims to have it and sell it increases the risk of it falling into the hands of groups ready to exploit it. For site managers, this means prioritizing updates, checking installed plugins, and monitoring logs: unusual volumes of outgoing emails, suspicious requests to known email sending endpoints, and changes to site files warrant attention.
Behind the numbers and auctions lies a human consequence: the proliferation of exploits in unregulated markets fuels fraud, identity theft, economic losses, and a general increase in distrust in digital communications. Responsible disclosure remains the key to limiting the damage: reporting the vulnerability to the plugin maintainer or using bug bounty channels helps close the flaw before it becomes raw material for real attacks.
The announcement about XSS reminds us that cybercrime has become a sophisticated market, where a software flaw becomes a commercial product. For website owners, the practical response is as simple as it is urgent: update, limit attack surfaces, and monitor. For the rest of digital society, the challenge remains to reduce the economic incentives for this underground trade, helping to move discoveries and reports from underground marketplaces to channels that repair the damage rather than multiply it.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
