
All’inizio si parlava di “virus” poi sono comparsi i “worm” seguiti poi dai “macro virus”.
A questi si sono presto affiancati altri tipi di software ostili come i keylogger o i locker.
Ad un certo punto abbiamo tutti iniziato a chiamarli più genericamente malware.
E proprio come i virus biologici, i malware si sono evoluti nel tempo; alcuni, sono altamente opportunisti, compaiono per sfruttare opportunità a breve termine mentre altri si sono evoluti per sfruttare difetti e problemi più fondamentali presenti nei sistemi IT che non sono ancora stati risolti.
I primi virus della storia informatica risalgono agli anni 70/80. Il primo malware della storia informatica è stato Creeper, un programma scritto per verificare la possibilità che un codice potesse replicarsi su macchine remote.
Il programma chiamato Elk Cloner è invece accreditato come il primo virus per computer apparso al mondo. Fu creato nel 1982 da Rich Skrenta sul DOS 3.3 della Apple e l’infezione era propagata con lo scambio di floppy disk: il virus si copiava nel settore di boot del disco e veniva caricato in memoria insieme al sistema operativo all’avvio del computer.
Nel corso degli anni ottanta e nei primi anni novanta, Con la proliferazione dei floppy disk si ebbe una notevole diffusione dei virus, infatti una pratica assai comune era lo scambio di floppy in ogni ambito lavorativo .Bastavano pochi floppy infetti per far partire un attacco su vasta scala
Dalla metà degli anni novanta, invece, con la diffusione di internet, i virus ed i cosiddetti malware in generale, iniziarono a diffondersi assai più velocemente, usando la rete e lo scambio di e-mail come fonte per nuove infezioni.
Il primo virus informatico che si guadagnò notorietà a livello mondiale venne creato nel 1986 da due fratelli pakistani proprietari di un negozio di computer per punire, secondo la loro versione, chi copiava illegalmente il loro software. Il virus si chiamava Brain, si diffuse in tutto il mondo, e fu il primo esempio di virus che infettava il settore di avvio del DOS.

Il primo file infector invece apparve nel 1987. Si chiamava #Lehigh e infettava solo il file command.com. Nel 1988 Robert Morris Jr. creò il primo #worm con diffusione su internet, il Morris worm. L’anno seguente, nel 1989, fecero la loro comparsa i primi virus polimorfi, con uno dei più famosi: Vienna, e venne diffuso il trojan AIDS (conosciuto anche come Cyborg), molto simile al trojan dei nostri giorni chiamato PGPCoder. Entrambi infatti codificano i dati del disco fisso chiedendo poi un riscatto all’utente per poter recuperare il tutto( il funzionamento è lo stesso degli attuali #Ransomware).
Nel 1995 il primo macrovirus, virus scritti nel linguaggio di scripting di programmi di Microsoft come Word ed Outlook che infettano soprattutto le varie versioni dei programmi Microsoft attraverso lo scambio di documenti. Concept fu il primo macro virus della storia.
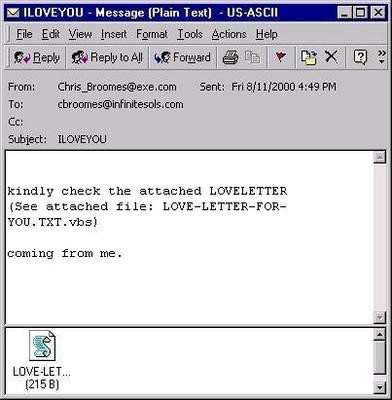
Nel 2000 il famoso I Love You che diede il via al periodo degli script virus.
Sono infatti i più insidiosi tra i virus diffusi attraverso la posta elettronica perché sfruttano la possibilità, offerta da diversi programmi come Outlook e Outlook Express di eseguire istruzioni attive (dette script), contenute nei messaggi di posta elettronica scritti in HTML per svolgere azioni potenzialmente pericolose sul computer del destinatario.
I virus realizzati con gli script sono i più pericolosi perché possono attivarsi da soli appena il messaggio viene aperto per la
lettura. I Love You si diffuse attraverso la posta elettronica in milioni di computer di tutto il mondo, al punto che per l’arresto del suo creatore, un ragazzo delle Filippine, dovette intervenire una squadra speciale dell’FBI.
Era un messaggio di posta elettronica contenente un piccolo programma che istruiva il computer a rimandare il messaggio appena arrivato a tutti gli indirizzi contenuti nella rubrica della vittima, in questo modo generando una specie di catena di sant’Antonio automatica che saturava i server di posta.
Dal 2001 si è registrato un incremento di worm che, per diffondersi, approfittano di falle di programmi o sistemi operativi senza bisogno dell’intervento dell’utente. L’apice nel 2003 e nel 2004: SQL/Slammer, il più rapido worm della storia – in quindici minuti dopo il primo attacco, Slammer aveva già infettato metà dei server che tenevano in piedi internet mettendo fuori uso i bancomat della Bank of America, spegnendo il servizio di emergenza 911 a Seattle e provocando la cancellazione per continui inspiegabili errori nei servizi di biglietteria e check-in di alcune compagnie aeree; ed i due worm più famosi della storia: Blaster e Sasser.
Nel gennaio 2004 compare MyDoom, worm che ancora oggi detiene il record di velocità di diffusione nel campo dei virus. Anche in questo caso il vettore di contagio è la posta elettronica: MyDoom, infatti, altro non è che un tool appositamente sviluppato (su commissione) per inviare spam. E, stando alle statistiche, ha svolto molto bene il suo lavoro.
Nel 2007, invece, nascono e si diffondono Storm Worm e Zeus. Il primo è un trojan horse altamente virale (si pensa che abbia infettato decine di milioni di macchine) che permette ad un hacker di prendere il controllo del computer infetto e aggiungerlo alla rete botnet Storm.
Il secondo, invece, colpisce sistemi informatici basati su Microsoft Windows ed è ideato per rubare informazioni di carattere bancario (credenziali per accedere al conto corrente e dati della carta di credito).

Dal 2010 in poi, gli anni della #cyberwar. La sempre maggiore diffusione di computer e altri dispositivi informatici rende i virus e i malware delle vere e proprie armi a disposizione delle maggiori potenze mondiali. Lo dimostra il virus Stuxnet, un trojan che si diffonde nella seconda parte dell’anno e da molti ritenuto un’arma per colpire i sistemi informatici delle centrali nucleari iraniane. Nel 2012 viene scoperto Flame, malware utilizzato, probabilmente, in azioni di spionaggio in alcuni Paesi del Medio Oriente e scoperto da alcuni informatici iraniani.
Nel medesimo anno cominciò a diffondersi nel 2012. Basato sul trojan Citadel (che era a sua volta basato sul trojan Zeus), il suo payload mostrava un avviso che sembrava provenire dalla polizia federale (da cui prese il nome “trojan della polizia”), affermando che il computer era stato utilizzato per attività illegali (ad esempio per il download di software pirata o di materiale pedopornografico).
L’avviso informava l’utente che per sbloccare il loro sistema avrebbe dovuto pagare una multa usando un voucher di un servizio di credito prepagato anonimo, per esempio
o Paysafecard. Per rendere maggiore l’illusione che il computer fosse sotto controllo della polizia federale, lo schermo mostrava anche l’Indirizzo IP della macchina, e alcune versioni mostravano addirittura dei filmati della webcam del PC per far sembrare che l’utente fosse anche ripreso dalla polizia.
Nonostante l’apertura di un nuovo fronte, i normali internauti restano i bersagli preferiti dei creatori di virus. Lo dimostra il malware Cryptolocker, comparso per la prima volta nel 2013 e ancora attivo , anche se con altre forme e altri nomi .
Nel 2014 si è assistito alla proliferazione del trojan Sypeng che era in grado di rubare i dati delle carte di credito, di accedere al registro delle chiamate, alla messaggistica, ai segnalibri del browser e ai contatti. Il malware è stato inizialmente diffuso nei paesi di lingua russa, ma a causa della particolare dinamica della sua distribuzione, ha messo a rischio milioni di pagine web che utilizzano AdSense per visualizzare messaggi pubblicitari. Diffuso via Internet, dà modo agli hacker di crittografare tutti i dati contenuti nel disco rigido e chiedere un riscatto vero e proprio per ottenere il codice di sblocco.
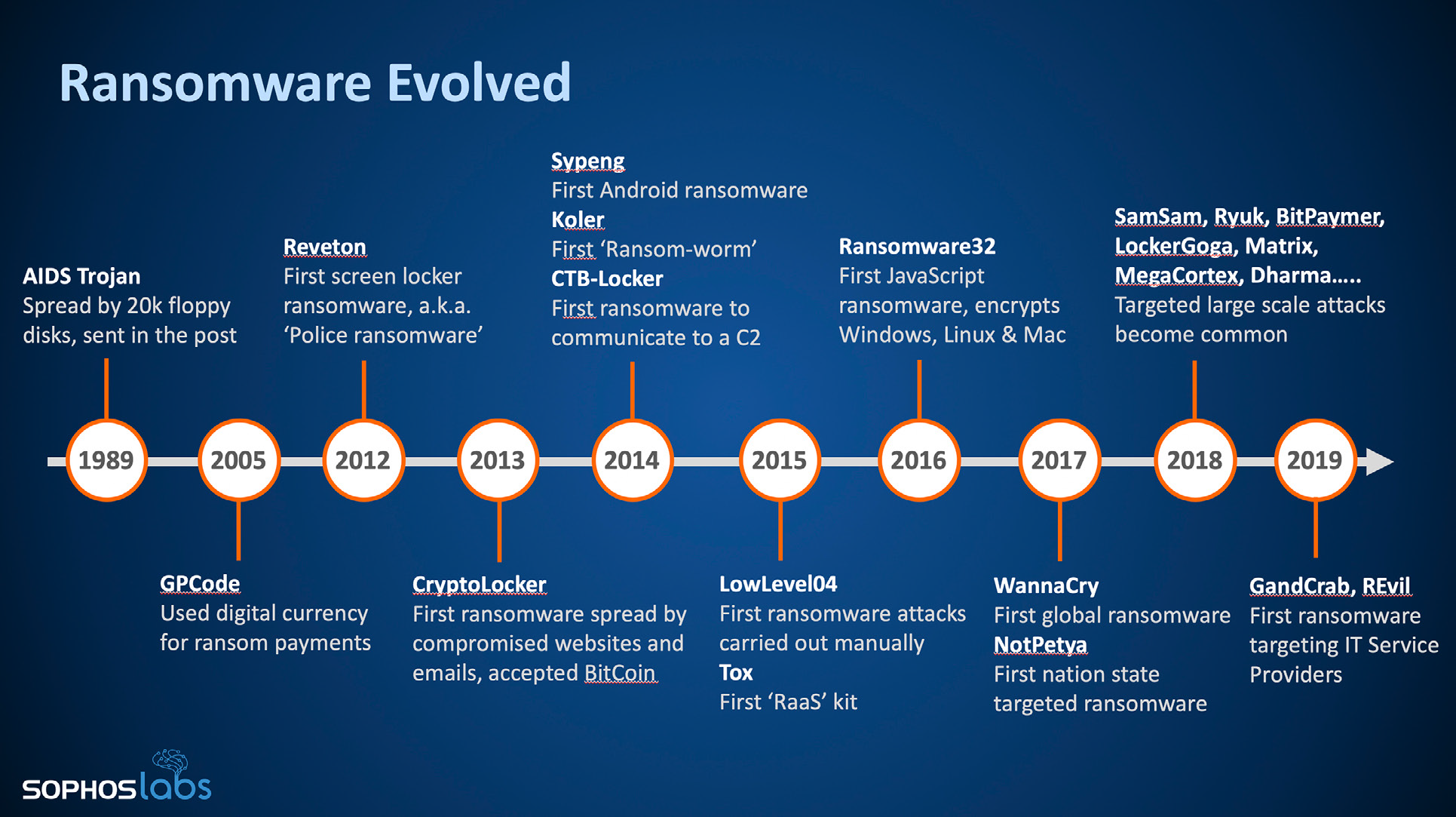
Evoluzione dei Ransomware – Sophos 2020 Threat Report – https://www.sophos.com/threatreport2020
Dopo i fatti di cronaca del 2019 il ransomware è diventato sicuramente il tipo di malware più noto e più temuto. Mentre molte persone potrebbero non sapere esattamente che un Bot o un RAT lo sono, praticamente tutti hanno sentito storie orribili di interi comuni, aziende o fornitori di servizi sanitari bloccati da ransomware. Potrebbero non sapere esattamente di cosa si tratta, ma sanno che è un problema attuale per qualche motivo.
Anche se i ransomware occupano la maggior parte del palcoscenico (in particolare sulla stampa generalista) non sono l’unica minaccia. Anche Keylogger, Data Stealer, RAM crapers, Bot, Banking Trojan e RAT continuano ad essere protagonisti di molti incidenti di sicurezza e provocare danni rilevanti.
I keyloggers sono sorprendentemente semplici ed allo stesso tempo estremamente efficaci e pericolosi. Si agganciano al flusso di dati provenienti dalle nostre tastiere, questo permette di intercettare tutto ciò che viene scritto. Il bersaglio principale sono solitamente le credenziali di accesso, ma questi malware possono intercettare anche altri tipi di informazione.
Possono essere implementati in molti modi diversi sia hardware che software. Ad esempio ne esistono alcuni progettati per essere nascosti nel connettore USB del cavo della tastiera.
“Data Stealers”, è il nome generico utilizzato per definire qualsiasi malware che entra nella nostra macchina e va a caccia nel nostro disco rigido, e forse anche in tutta la nostra rete, se possibile, alla ricerca di file che contengano dati che valgono qualcosa per i criminali.
I malware non riescono sempre a trovare ciò che vogliono nei file presenti sul nostro computer, anche se il malware ha accesso come amministratore o root. Questo perché i dati utili potrebbero esistere solo temporaneamente nella memoria prima di essere deliberatamente cancellati senza mai essere scritti su disco.
Ad esempio la memorizzazione permanente di alcuni dati è ora vietata da regolamenti come PCI-DSS, che è lo standard di sicurezza dei dati del settore delle carte di pagamento.
Però i computer DEVONO, ad esempio, disporre di una chiave privata nella RAM per eseguire la decodifica. I dati segreti DEVONO esistere temporaneamente nella RAM, anche se solo per un breve periodo. Perciò ,cose come chiavi di decrittazione, password in chiaro e token di autenticazione di siti Web sono i tipici bersagli dei RAM scrapers.
Il bot è un programma che accede alla rete attraverso lo stesso tipo di canali utilizzati dagli utenti umani (per esempio che accede alle pagine Web, invia messaggi in una chat, si muove nei videogiochi, e così via). Programmi di questo tipo sono diffusi in relazione a molti diversi servizi in rete, con scopi vari, ma in genere legati all’automazione di compiti che sarebbero troppo gravosi o complessi per gli utenti umani.Fondamentalmente un bot stabilisce una backdoor semi-permanente in un computer in modo che gli attaccanti possano inviare comandi ovunque si trovino.
Una raccolta di bot viene chiamata botnet. L’altro termine popolare per “Bot” è “Zombi” perché possono anche agire un po ‘come agenti dormienti. I bot comprendono l’invio di carichi di spam dal tuo indirizzo IP, la ricerca di file locali, l’annullamento delle password, l’esplosione di altre macchine su Internet con inondazioni di traffico e persino il clic sugli annunci online per generare entrate pay-per-click.
I Trojan bancari meritano la loro sottoclasse di malware a causa della loro specializzazione. Si rivolgono esclusivamente alle informazioni bancarie online della vittima. I trojan bancari in genere includono un componente keylogger, per catturare le password mentre vengono immesse e un componente di furto di dati trovare password non crittografate o dettagli dell’account.
Il RAT – abbreviazione di Remote Access Trojan – ha molto in comune con un “bot”, ma differisce da questo perchè non fa parte di una massiccia campagna per vedere quanti “bot” possono essere richiamati e gestiti per eventi di attacco di massa .
Solitamente i RAT sono impiegati in attacchi più mirati e potenzialmente per eseguire un intrusione dannosa. Possono catturare screenshot, ascoltare l’audio delle nostre stanze attraverso il microfono del PC e accendere le nostre webcam.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…
 Cyber Italia
Cyber ItaliaNegli ultimi giorni è stato segnalato un preoccupante aumento di truffe diffuse tramite WhatsApp dal CERT-AGID. I messaggi arrivano apparentemente da contatti conosciuti e richiedono urgentemente denaro, spesso per emergenze come spese mediche improvvise. La…