
Millions of people and businesses rely on Google Drive to store contracts, reports, photos, and work documents, using the Windows desktop client to sync files between local and cloud folders. But it was this very application that proved vulnerable: a serious bug was discovered that allows anyone on a shared computer to gain full access to the contents of someone else’s Google Drive account without having to request new authorization.
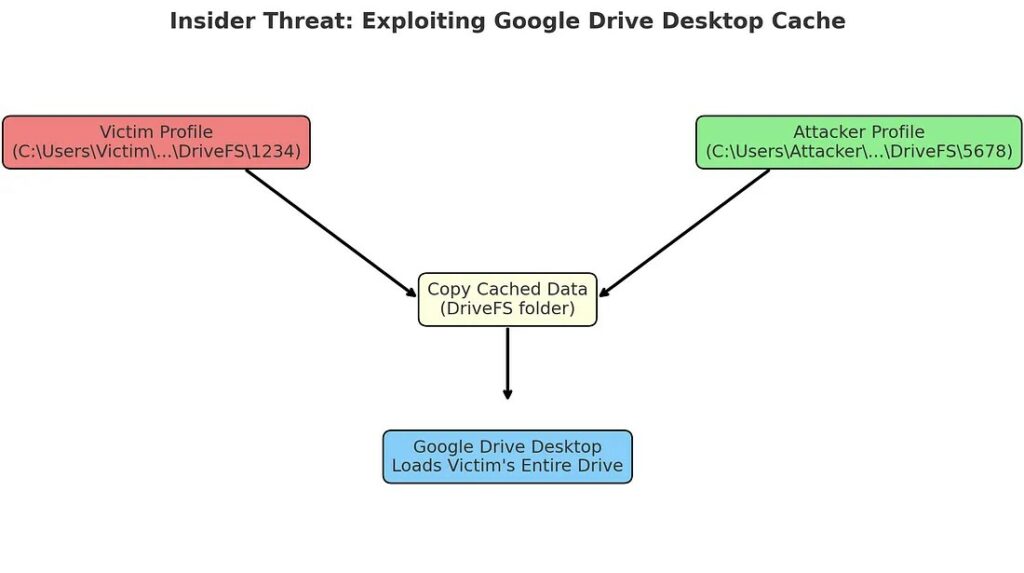
Researchers discovered that the program saves copies of synchronized data in a hidden DriveFS folder within the Windows profile. This directory should be accessible only to the owner, but the application doesn’t check access rights when connecting to the cache. Simply copy the contents of another user’s DriveFS folder to your profile, and the client will then load someone else’s data as if it were your own. Upon launch, Google Drive Desktop perceives the transferred cache as legitimate, bypassing authentication checks and allowing access to personal and corporate files.
A practical test has shown that on Windows 10 and 11 with client version 112.0.3.0 the procedure is simple: the attacker logs in to Google Drive with their account, closes the application, copies the victim’s DriveFS directory (C:/Users/[victim]/AppData/Local/Google/DriveFS/[ID]) to their own directory (C:/Users/[attacker]/AppData/Local/Google/DriveFS/[ID]), and restarts the program. As a result, it gains full access to the victim’s main drive, as well as all shared drives, without passwords or notifications.
Source code, financial statements, personal photos, and any other documents are in open format.
This mechanism violates the core principles of Zero Trust, which require mandatory verification. identity at each login, and also compromises the protection associated with data encryption.Cached files are stored in the clear and can be accessed by anyone with access to the system. This violates NIST, ISO 27001, GDPR, and HIPAA standards and regulations, which require strict isolation and periodic verification of credentials.
Until a fix is released, organizations are advised to stop using Google Drive Desktop on computers with multiple users. Temporary measures include clearing the cache when switching accounts, using separate Windows profiles with strict access rights, and restricting the client to running only on trusted devices. To permanently address this issue, Google should implement individual encryption of cached data, a new mandatory login when mounting a folder, and strict file system permissions.
Since a significant percentage of leaks are caused by internal personnel, relying on an unprotected cache becomes a direct threat. Until the company closes this loophole, users and IT departments are at risk of unauthorized access to their most critical data.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
