
E’ stato sviluppato un proof-of-concept (PoC) di un exploit per una falla critica che consente l’escalation dei privilegi locali, interessando varie distribuzioni Linux principali, come Fedora e SUSE. La vulnerabilità, monitorata con il codice CVE-2025-6019, consente agli utenti non privilegiati di ottenere l’accesso root sfruttando il demone udisksd e la sua libreria backend libblockdev, creando significativi rischi per la sicurezza dei sistemi multiutente e degli ambienti condivisi.
La vulnerabilità sfrutta una vulnerabilità fondamentale nel modo in cui il demone udisksd elabora le richieste di comunicazione D-Bus dagli utenti del gruppo allow_active. Quando i sistemi correttamente configurati ricevono operazioni relative al disco tramite chiamate D-Bus, il demone presuppone erroneamente che la sola appartenenza al gruppo fornisca un’autorizzazione sufficiente per operazioni sensibili.
Ricordiamo che il demone udisksd è un componente di sistema su Linux responsabile della gestione dei dispositivi di archiviazione (dischi rigidi, SSD, chiavette USB, CD/DVD, ecc.). Questo PoC consente agli aggressori di aggirare i controlli di sicurezza previsti ed eseguire operazioni privilegiate con permessi di root.
Il vettore di attacco si concentra sulla gestione impropria dell’autorità dell’utente durante le comunicazioni interprocesso tramite D-Bus. I ricercatori di sicurezza hanno scoperto che il demone udisksd non riesce a convalidare adeguatamente il contesto dell’utente che effettua l’invocazione, affidandosi invece esclusivamente a controlli dei privilegi basati sul gruppo.
Secondo l’analisi di SecureLayer7, questo difetto di progettazione crea un percorso sfruttabile in cui le chiamate D-Bus possono essere manipolate per innescare operazioni privilegiate non autorizzate. L’analisi statica del codice sorgente di udisks2 e libblockdev ha rivelato diversi pattern preoccupanti nel percorso di escalation dei privilegi. Il flusso di esecuzione vulnerabile segue il seguente schema: udisks_daemon_handle_mount → polkit_check → blkdev_mount.
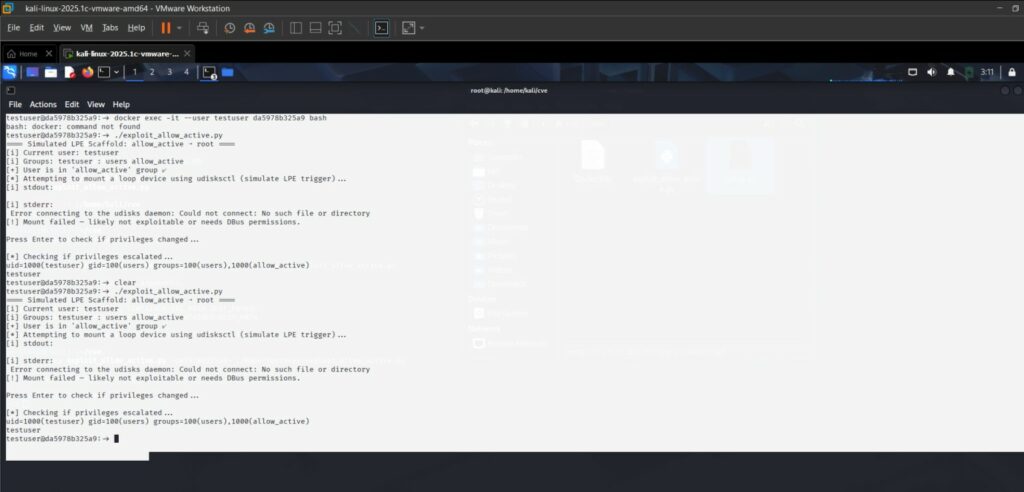
Questa sequenza consente agli utenti non privilegiati di far sì che udisksd esegua operazioni di montaggio con permessi di root, aggirando di fatto il modello di sicurezza previsto. Il processo di exploit richiede una sofisticazione tecnica minima, il che lo rende particolarmente pericoloso. Gli aggressori necessitano solo dell’appartenenza al gruppo allow_active e della capacità di eseguire comandi udisksctl.
La prova di concetto dimostra che un semplice comando come udisksctl mount -b /dev/loop0 può causare operazioni di montaggio controllate da root da parte di utenti non root, portando potenzialmente alla compromissione dell’intero sistema. La vulnerabilità interessa un’ampia gamma di distribuzioni Linux che implementano udisks2 e libblockdev nei loro ambienti desktop. I sistemi Fedora e SUSE sono particolarmente vulnerabili a causa delle loro configurazioni predefinite, che spesso includono utenti nel gruppo allow_active per le funzionalità desktop.
Il problema della sicurezza è particolarmente preoccupante per gli ambienti di elaborazione condivisi, i sistemi multiutente e qualsiasi distribuzione in cui la separazione dei privilegi è fondamentale. I responsabili della distribuzione hanno risposto con aggiornamenti di sicurezza che risolvono la vulnerabilità principale attraverso diversi meccanismi. La correzione principale prevede una verifica basata sull’UID più rigorosa, anziché basarsi esclusivamente sull’appartenenza al gruppo. Il codice aggiornato ora richiede sia l’appartenenza al gruppo che un contesto UID appropriato prima di consentire operazioni privilegiate.
Gli amministratori di sistema dovrebbero aggiornare immediatamente i pacchetti udisks2 e libblockdev alle versioni corrette. Le organizzazioni dovrebbero inoltre verificare le autorizzazioni basate sui gruppi e implementare regole polkit più rigorose per prevenire vulnerabilità simili.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…
 Cyber Italia
Cyber ItaliaNegli ultimi giorni è stato segnalato un preoccupante aumento di truffe diffuse tramite WhatsApp dal CERT-AGID. I messaggi arrivano apparentemente da contatti conosciuti e richiedono urgentemente denaro, spesso per emergenze come spese mediche improvvise. La…