
A recent discovery has uncovered a sophisticated technique that bypasses Windows User Account Control (UAC), allowing privilege escalation without user intervention through the use of the private font editor, raising global concerns among system administrators.
The attack disclosed by Matan Bahar exploits eudcedit.exe, Microsoft’s built-in private font editor, located in C:WindowsSystem32, originally designed to create and edit end-user-defined fonts (EUDC).
Security researchers have discovered that this seemingly harmless utility can be exploited to bypass Windows’ primary security gatekeeper.
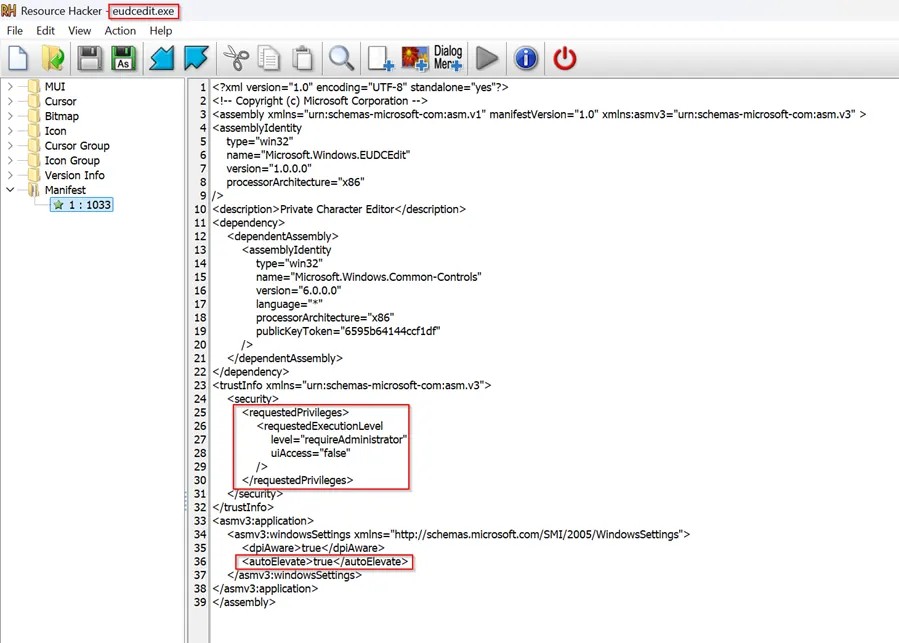
The security flaw is caused by critical settings embedded in the eudcedit.exe application manifest. This vulnerability is triggered by two specific metadata tags. This combination proves particularly dangerous. When UAC is configured with permissive settings such as “Elevate without prompting,” Windows automatically elevates eudcedit.exe from a medium integrity level to a high integrity level without displaying a security warning, Bahar said.
The attack develops through a carefully crafted sequence that exploits the application’s file handling mechanisms. The attackers begin by launching the private font editor, which automatically switches to the “High” integrity level. They then access the font linking functionality within the application interface, typically accessed via the File menu.
The critical vulnerability manifests when users select the font linking options and are prompted to save the files. In this scenario, the elevated eudcedit.exe process can be manipulated to execute arbitrary commands. By simply entering “PowerShell” in the file dialog box, attackers can spawn an elevated PowerShell session that inherits the high integrity level of the parent process.
The eudcedit.exe UAC bypass demonstrates how attackers can exploit legitimate system utilities to achieve malicious goals. The simplicity and effectiveness of this technique make it a significant concern for corporate security teams.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
