
In una nuova analisi basata su 10 milioni di password compromesse, Specops ha dimostrato quanto le reti aziendali rimangano vulnerabili all’errore umano. Tutte le password sono state estratte da un elenco di oltre un miliardo di perdite. I risultati sono stati allarmanti: solo l’1,5% di tutte le password analizzate poteva essere classificato come “forte”.
I criteri per questa definizione erano rigorosi: una password era considerata sicura se era lunga 15 caratteri e conteneva almeno due tipi di caratteri diversi, come lettere e numeri. Questa lunghezza è stata scelta per un motivo: ogni carattere aggiuntivo aumenta di molte volte il numero di combinazioni possibili.
Ad esempio, una password di 15 lettere minuscole ha 1,7 quintilioni di combinazioni. L’aggiunta di un carattere aumenta il numero di combinazioni di quasi 26 volte e, utilizzando tutti i caratteri validi (lettere, numeri e caratteri speciali), il numero totale di combinazioni raggiunge i 2,25 ottilioni. Persino i computer con GPU più potenti non saranno in grado di gestire un compito del genere nel prossimo futuro.
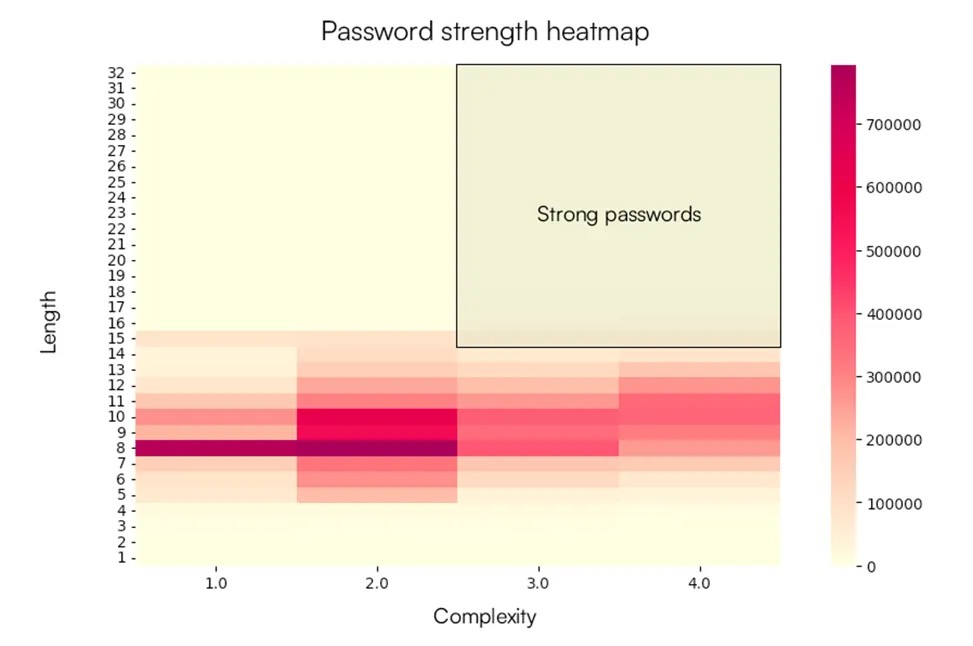
Mappa di calore: lunghezza della password vs. complessità della password (Specops)
Tuttavia, nonostante queste prospettive, gli utenti continuano a scegliere combinazioni brevi e semplici. Il tipo di password più comune è composto da 8 caratteri con due tipi di caratteri (ad esempio, lettere e numeri), che rappresenta il 7,9% di tutte le password. Seguono password della stessa lunghezza, ma ancora meno affidabili: un solo tipo di carattere, il loro 7,6%. E le password lunghe fino a 8 caratteri in generale costituiscono la stragrande maggioranza e possono essere violate in poche ore.
L’analisi ha mostrato che solo il 3,3% di tutte le password superava il limite di 15 caratteri. Ciò suggerisce che le policy sulle password nelle organizzazioni non sono regolamentate o sono ignorate. Allo stesso tempo, aumentare la lunghezza anche di pochi caratteri aumenta drasticamente la resistenza agli attacchi: un’estensione di quattro caratteri di una password di 12 caratteri aumenta lo sforzo richiesto per un attacco brute-force di 78 milioni di volte.
Lo studio presta particolare attenzione alla tendenza verso una complessità insufficiente. Più della metà di tutte le password analizzate includeva un massimo di due tipi di caratteri. E sebbene le raccomandazioni moderne (in particolare quelle del NIST) si concentrino maggiormente sulla lunghezza, l’aggiunta di un terzo o quarto tipo di carattere ne aumenta significativamente la sicurezza. Tuttavia, la lunghezza rimane il fattore principale: 16-20 caratteri offrono una protezione migliore rispetto a password brevi, seppur complesse.
Per aumentare la sicurezza, si consiglia di passare dalle password tradizionali a frasi significative. Frasi lunghe ma facili da ricordare come “SunsetCoffeeMaroonReview” sono molto più affidabili e pratiche di set di caratteri come “!x9#A7b!”. Questo approccio riduce il numero di errori di digitazione, le richieste di supporto tecnico e la fatica derivante dal continuo cambio di password.
Le principali minacce legate all’utilizzo di password deboli rimangono le stesse.
Allo stesso tempo, anche una buona implementazione dell’hashing non salva dalla debolezza della password stessa: se il database viene rubato e la password viene facilmente forzata tramite attacco brute force, né il salt né gli algoritmi saranno d’aiuto.
I risultati dello studio portano a una semplice verità: le password deboli sono ancora onnipresenti. Solo una politica completa che includa il controllo su lunghezza, complessità, unicità e aggiornamenti tempestivi può proteggere l’infrastruttura aziendale dagli attacchi più comuni. E, come dimostrano le statistiche, la maggior parte delle aziende ha ancora molto lavoro da fare in questo ambito.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…