
Active Directory (AD) contains the organization’s digital keys: unauthorized access to this service exposes sensitive information and credentials that can lead to a complete domain compromise.
Among the most critical assets is the NTDS.dit file, which stores the domain dataset and password hashes. This article reconstructs a real-world case in which malicious actors gained elevated privileges, extracted NTDS.dit, and attempted to exfiltrate it by bypassing common controls.
In a Windows environment dominated by Active Directory, the NTDS.dit (NT Directory Services Directory Information Tree) file represents the central database for the domain: it contains user accounts, group policies, computer objects, and—crucially—the password hashes of all accounts, including those with Domain Administrator privileges.
Stealing this file allows an attacker, once in possession of the system hive (SYSTEM) to decrypt the contents, extract the hashes, attack them offline, and impersonate any identity within the domain. Essentially, they obtain a “map” of the organization’s digital identity.
According to Trellix research, after gaining administrative privileges on a host, attackers often leverage native tools (such as vssadmin ) to create Volume Shadow Copies and bypass file locks, copying NTDS.dit without interrupting AD processes. They then repair the file with esentutl and extract credentials with utilities such as SecretsDump , Mimikatz , or even simple copy commands. These operations can be surprisingly silent for many traditional defenses, which is why behavior-based detection is crucial.
The case analysis shows a typical chain of actions: initial login, hash collection, use of hashes to authenticate, lateral movement, and then extraction of NTDS.dit along with the SYSTEM registry hive, which is essential for obtaining the boot key needed for decryption.
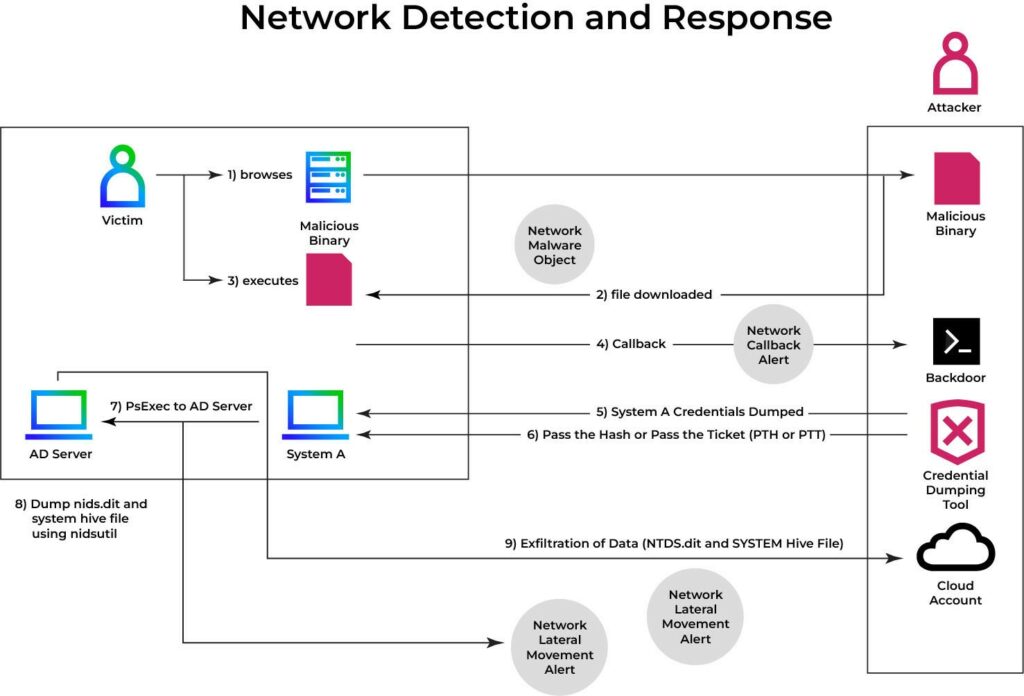
Main phases illustrated:
lsass.exe process (e.g., with Mimikatz), which requires elevated privileges on the compromised host./ntlm , /aes128 , /aes256 ) to connect to network resources or launch remote processes.NTDSUtil.exe or DSDBUtil.exe to export data. From the snapshot, attackers take NTDS.dit and the SYSTEM hive, place them in a staging folder, verify them with hex editors or AD parsing tools, and then archive them for exfiltration to external servers.
The analysis reveals concrete mitigation recommendations: monitor and block unusual SMB movements and file transfers, control and limit the use of remote administration tools such as PsExec, strengthen the protection of highly privileged accounts, and enable checks to detect Volume Shadow Copy creations and other known file lock bypass techniques.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
