
American aviation and defense components manufacturer ADC Aerospace has found itself in the spotlight due to a possible cyber attack by the Play ransomware group, which appeared on their blog where criminal hackers claim to have compromised company data and customer documents.
Disclaimer: This report includes screenshots and/or text from publicly available sources. The information provided is for threat intelligence and cybersecurity risk awareness purposes only. Red Hot Cyber condemns any unauthorized access, improper dissemination, or misuse of this data. It is currently not possible to independently verify the authenticity of the information reported, as the organization involved has not yet released an official statement on its website. Therefore, this article should be considered for informational and intelligence purposes only.
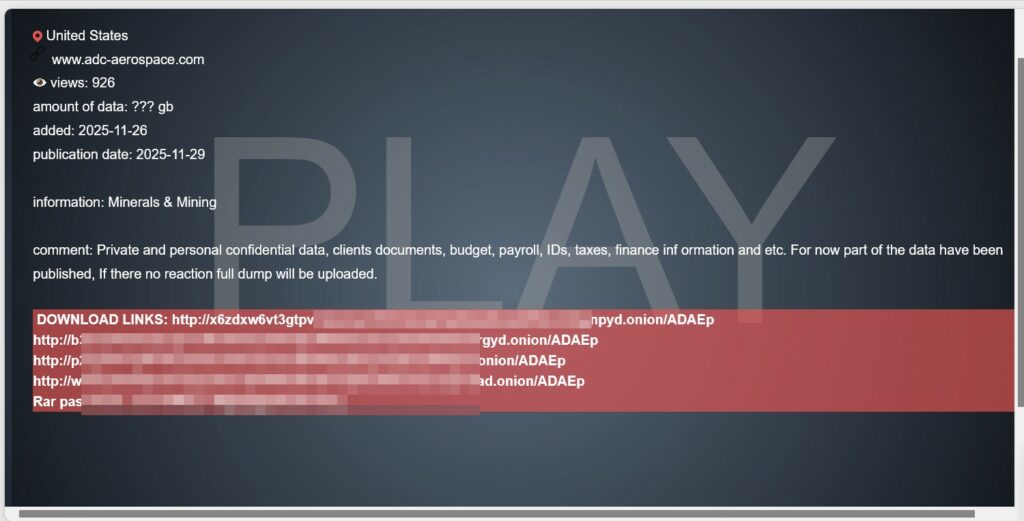
According to a post on the ransomware website, access was gained to customer records, financial and balance sheet information, payroll records, identity documents, and other sensitive personal information. However, no evidence in the form of file samples was provided, so the veracity of these claims cannot currently be verified.
Such ads are often used as the first warning to the victim that their data has been stolen, followed by pressure to pay a ransom.
If the leak is confirmed, the consequences of the incident could be severe for ADC Aerospace. The stolen data could be sold on darknet markets, where information on US defense contractors is traditionally in high demand. Employee payroll data, which contains a rich set of personal identifiers suitable for identity theft, poses an additional threat.
The combination of financial and personal information opens up ample opportunities for social engineering attacks. Attackers gain the resources to create plausible cover stories, even when attempting to impersonate industry representatives and gain deeper access to internal systems.
The risks are particularly acute given ADC Aerospace’s position in the supply chain. The company supplies components to giants such as Northrop Grumman, Collins Aerospace, Philips, Honeywell , and other major aerospace and defense players, potentially expanding the range of affected counterparties.
The Play group is considered one of the most active ransomware operations in recent years. In August, it claimed responsibility for an attack on Jamco Aerospace, a supplier of components for commercial and military aircraft that works with the U.S. Navy, Boeing, and Northrop Grumman, among others. Previously, Play has been attributed to attacks on the Palo Alto County Sheriff’s Office in Iowa and the Donald W. Wyatt Maximum Security Prison in Rhode Island, as well as cloud services provider Rackspace, the German hotel chain H-Hotels, and the French subsidiary of BMW.
According to Adlumin, Play was one of the first groups to use intermittent encryption , which locks down only specific portions of the file system. This approach accelerates infrastructure disruption and data exfiltration, and was later adopted by other well-known ransomware groups, including ALPHV/BlackCat, DarkBit, and BianLian.
ADC Aerospace has not yet released an official statement regarding the ransomware allegations. Cybernews was unable to obtain a response from the company at the time of publication.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
