
At the DefCon security conference, researchers presented a significant exploit chain that allows attackers to gain administrator permissions for vehicle entertainment systems through Apple CarPlay.
The attack known as “Pwn My Ride” targets a series of vulnerabilities in the protocols that govern the operation of wireless CarPlay. These vulnerabilities can be exploited to remotely execute code (RCE) on the vehicle’s multimedia unit, jeopardizing the security of the system.
The attack, in its nature, consists of a sequence of weaknesses inherent in the protocols that govern wireless CarPlay. This allows remote code execution on the vehicle’s multimedia unit, potentially allowing attackers to take control of the system.
At the heart of this exploit is CVE-2025-24132, a severe stack buffer overflow within the AirPlay protocol SDK. Oligo Security researchers have detailed how this flaw can be triggered when an intruder infiltrates the vehicle’s Wi-Fi network.
The vulnerability affects a broad spectrum of devices using versions of the AirPlay Audio SDK earlier than 2.7.1, versions of the AirPlay Video SDK earlier than 3.6.0.126, as well as specific versions of the CarPlay communications plug-in.
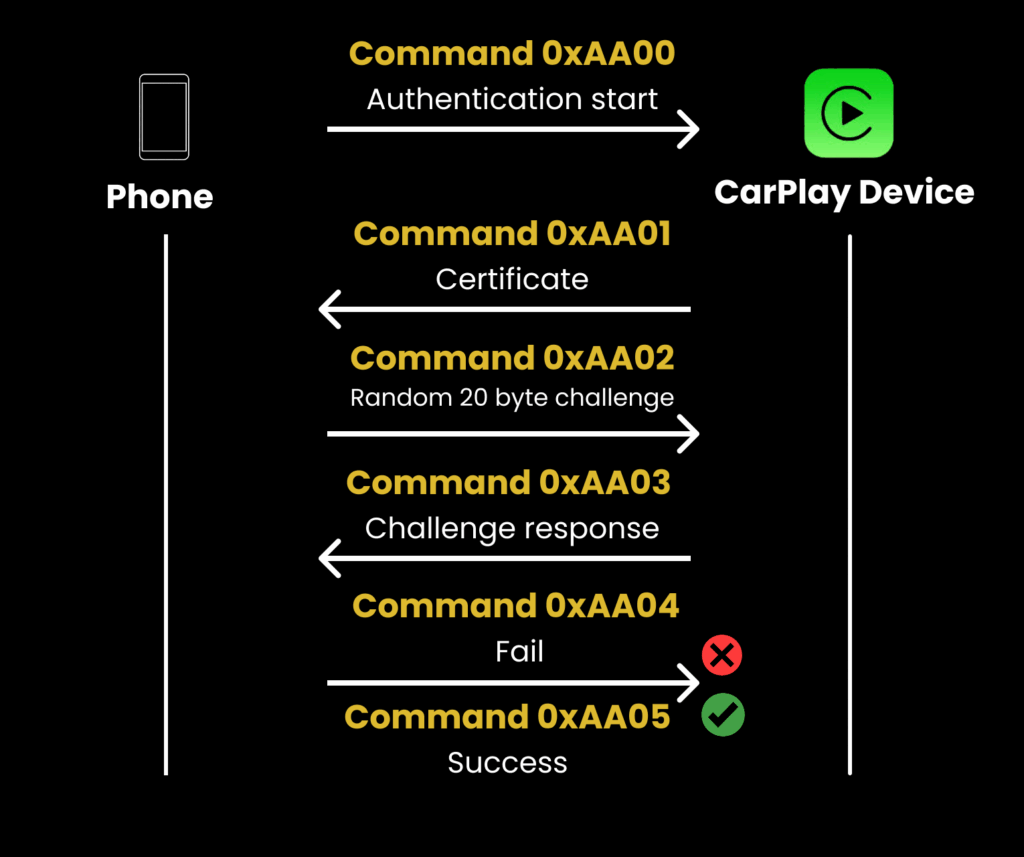
By exploiting this stack buffer overflow, an attacker can execute arbitrary code with elevated privileges, effectively taking control of the infotainment system. The attack begins by targeting CarPlay’s initial wireless connection phase, which relies on two key protocols: iAP2 (iPod Accessory Protocol) over Bluetooth and AirPlay over Wi-Fi.
Researchers discovered a fundamental flaw in the iAP2 authentication process. While the protocol requires the car to authenticate the phone, it neglects mutual authentication, allowing the phone to go unverified by the vehicle. This one-way authentication allows an attacker’s device to masquerade as a legitimate iPhone.
The attacker can then pair with the vehicle’s Bluetooth, often without a PIN due to the prevalence of the insecure “Just Works” pairing mode on many systems. Once paired, the attacker exploits the iAP2 vulnerability by sending a RequestAccessoryWiFiConfigurationInformation command, effectively tricking the system into revealing the vehicle’s SSID and Wi-Fi password.
With the Wi-Fi credentials in hand, the attacker gains access to the vehicle’s network and activates CVE-2025-24132 to protect root access. The entire process can be executed as a no-click attack on numerous vehicles, without requiring any interaction from the driver.
Although Apple released a patch for the vulnerable AirPlay SDK in April 2025, researchers noted that, as of their latest report, no car manufacturer had implemented the fix, according to Oligo Security.
Unlike smartphones, which benefit from regular over-the-air (OTA) updates, vehicle software update cycles are notoriously long and fragmented.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
