
The threat actor APT28 , classified as an Advanced Persistent Threat, active since at least 2004, identified by the alias BlueDelta, but even better known under the name IRON TWILIGHT or Fancy Bear , has recently been associated by Insikt Group (Recorded Future) with an alleged credential harvesting campaign.
The operation reportedly targeted individuals linked to a Turkish energy and nuclear research agency, as well as support staff at a European think tank and several agencies operating in Uzbekistan and North Macedonia. Currently available information comes from cyber threat intelligence and public industry sources. These describe a series of targeted operations, spread across various time frames throughout 2025.
According to published analyses, the observed activity appears to be part of a broader strategy of gathering legitimate access, consistent with the operational profile historically attributed to this group. APT28’s operations are generally characterized by targeted campaigns, a high focus on persistence, and a marked ability to adapt to the defensive countermeasures adopted by target organizations. Its reputation is linked to the continuity of its operations, coherence of objectives, and the ability to reuse consolidated operational patterns, adapting them to different geopolitical contexts.
Considered one of the longest-running and most active groups, APT28 is a group historically associated with cyber espionage operations linked to Russia’s General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS) military unit 26165.
Over the years, the group has been linked to numerous campaigns involving government institutions, international organizations, research institutions, and defense and foreign policy settings. According to MITRE ATT&CK, it is also believed responsible for the 2016 compromise of Hillary Clinton’s campaign, the Democratic National Committee, and the Democratic Congressional Campaign Committee in an attempt to interfere in the U.S. presidential election.
These elements make APT28 particularly relevant from the perspective of strategic threat intelligence and risk assessment.
At this time, we cannot confirm the authenticity of this news, as the organizations involved have not published any official statements on their respective websites regarding the incidents described. The information reported comes from publicly accessible sources and intelligence sources, and should therefore be interpreted as intelligence and not as definitive confirmation.
Analysis of the attack chain associated with the alleged credential harvesting campaign attributed to APT28 reveals a carefully constructed operational flow to guide the victim through a seemingly coherent and unremarkable sequence of steps. The entire process appears designed to maintain a low profile, reduce the possibility of detection, and maximize the likelihood of successful credential harvesting.
The initial phase begins with a targeted phishing email campaign, crafted with contextualized content, both linguistically and thematically. The content is aligned with the professional interests of potential victims and draws on real-world, current contexts, such as research, international cooperation, or geopolitical analysis. This phase represents the entry point for the interaction, a fundamental prerequisite for the development of the subsequent phases of the chain.
The message contains a link to a shortened URL, shortened using shortener services to obscure the final destination and make it harder for the user to evaluate the link. Clicking the link directs the victim to legitimate web services hosting an intermediate resource, the first point in the redirect chain.
At this stage, a decoy document is displayed: a genuine, publicly available PDF displayed for a very limited time. The use of legitimate content reinforces the perception of trustworthiness and helps reduce any suspicions on the part of the victim, who may encounter material consistent with what was advertised in the email.
After a few moments, the user is redirected to a fake authentication page, also hosted on legitimate, temporary infrastructure. The page faithfully reproduces the appearance of access portals widely used in enterprise contexts, requiring a login to access or continue browsing the content.
Some examples of spoofed credential harvesting pages include webmail logins, VPN services such as Sophos, Microsoft Outlook Web Access (OWA), or Google.


examples of counterfeit portals
When the page is opened, a signal (open beacon) is generated that allows attackers to confirm the victim’s actual involvement and monitor the progress of the campaign.
As soon as the user enters their credentials, they are collected and transmitted to the threat actor’s controlled infrastructure. This is the crucial phase of the entire operation, allowing for the acquisition of valid access that can be used at later stages, over time, for intelligence gathering activities or for further compromises.
A notable element is the final phase of the flow, which involves a redirect to the original PDF document, hosted on a legitimate site. From the victim’s perspective, the experience appears straightforward and free of obvious anomalies, significantly reducing the likelihood of the event being immediately reported or recognized as a phishing attempt.
Overall, this attack chain reflects an operational model consistent with the activities historically attributed to APT28, characterized by extensive use of social engineering and legitimate infrastructure, while maintaining a strong focus on reducing operational noise. From a CTI perspective, the effectiveness of the workflow lies not in individual technical elements, but in the sequential combination of phases, which makes the entire user experience credible from start to finish, significantly complicating detection based on isolated indicators.
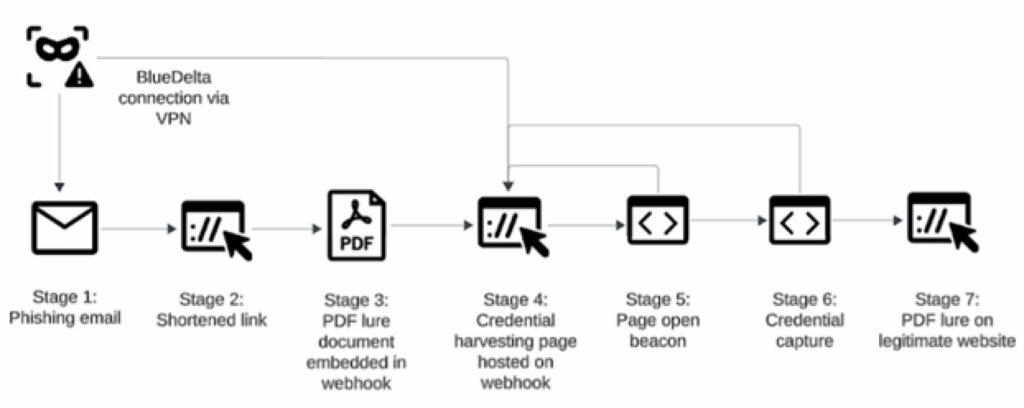
Attack chain
The activities described are consistent with the tactics and techniques of the MITRE ATT&CK framework. The Initial Access tactic to obtain credentials through phishing emails and deceptive links falls under the Spearphishing Link techniques. Impersonation techniques They can be characterized by the abuse of legitimate websites and are part of Defense Evasion tactics.
The use of harvested Valid Accounts techniques will be part of future Initial Access , Persistence , and Privilege Escalation tactics in the actual compromise of target systems.
Taken together, these techniques rank at the highest levels of the so-called Pyramid of Pain, rendering a defensive approach based solely on blocking individual technical indicators ineffective, as it can be easily circumvented, and underscoring the need for behavioral and contextual monitoring to force the threat actor to profoundly modify its modus operandi.
Currently available information suggests that the alleged campaign attributed to APT28 further confirms the group’s interest in credential harvesting as a means of gaining legitimate access to contexts of strategic interest. The use of campaign monitoring systems and increasingly cutting-edge evasive techniques to reduce the noise of threat actors’ operations confirms the need for a broader view of defensive strategies, integrating CTI (Cyber Threat Intelligence) and TTP (Tactics, Techniques, and Procedures) analysis to counter their activities.
In the absence of official confirmation from the organizations involved, this news should be interpreted exclusively as intelligence useful for understanding the evolution of advanced phishing techniques and the operational models adopted by state actors.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
