Google executives said that hackers created a fake account on the Law Enforcement Request System (LERS), the company's platform used by law enforcement agencies to submit official data requests. Late...
Artificial intelligence systems are increasingly under attack. This data emerges from "Trend Micro State of AI Security Report, 1H 2025". The company urges IT professionals and community leaders to follow...
F6 and RuStore experts report having discovered and blocked 604 domains that were part of the infrastructure of hackers who infected mobile devices with the DeliveryRAT Trojan. The malware masqueraded...
The cyber attack on Jaguar Land Rover, which paralyzed the company's operations, has become one of the most serious crises for the British car manufacturer. The company was forced to...
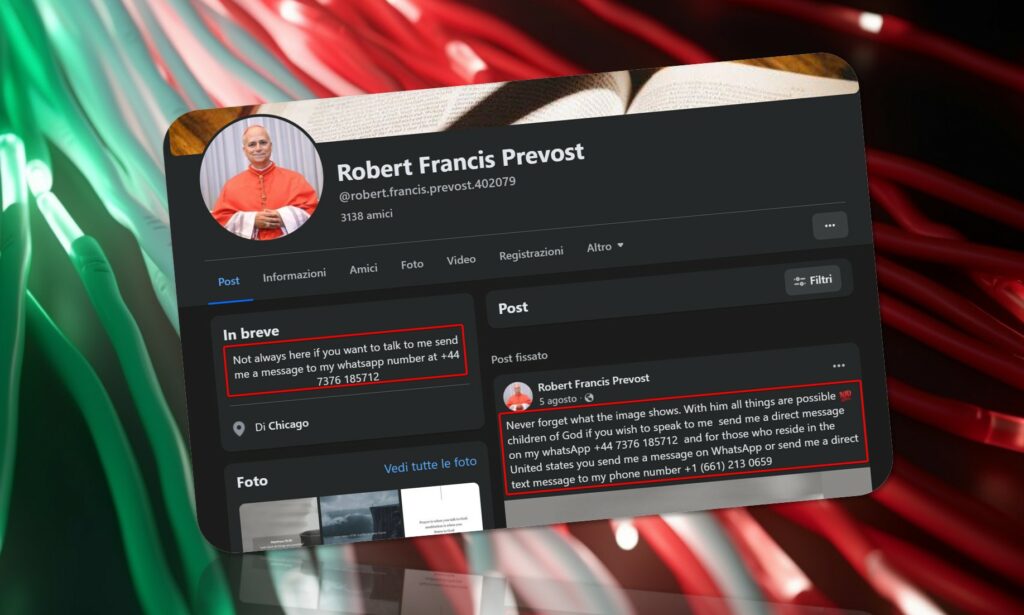
In recent years, online scams have taken on increasingly sophisticated forms, exploiting not only social engineering techniques but also the trust that millions of people place in religious, institutional, or...
IBM X-Force researchers have discovered new operations by the Chinese group Hive0154, better known as Mustang Panda. Experts have documented the simultaneous use of an advanced version of the Toneshell...
Microsoft reminded users that support for the beloved Windows 10 will end in a month. Starting October 14, 2025, the system will no longer receive security updates, bug fixes, and...
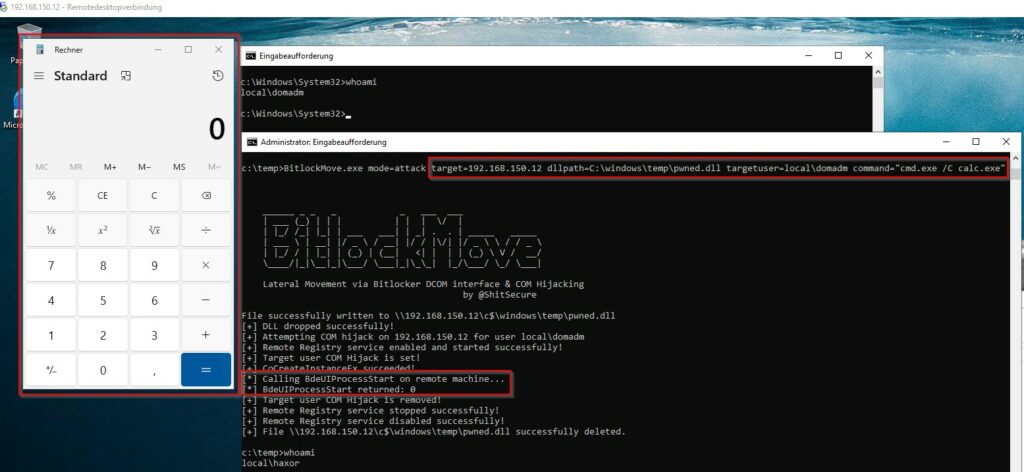
An innovative tool known as BitlockMove has been introduced, which highlights a novel lateral movement technique. This PoC leverages DCOM interfaces and COM hijacking, both of which are functional for...
Researchers have reported a new surge in activity for ChillyHell, a modular backdoor for macOS that was thought to be dormant for years, but which appears to have infected computers...
The Linux world and its surroundings are going through turbulent times. Developers are debating how to integrate Rust into the kernel while key contributors are leaving. Against the backdrop of...