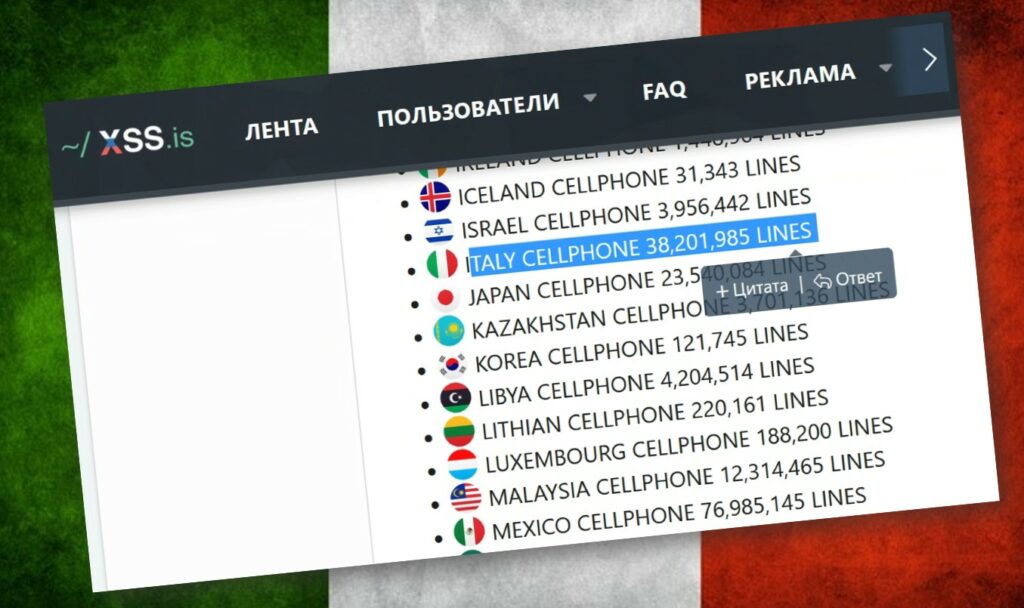
Seven out of ten Italians have their phone numbers included in this database. But what does it mean to have such a large number of phone numbers concentrated within a...
The U.S. Department of Justice has filed a lawsuit against Apitor Technology, accusing it of secretly collecting children's location data through a Chinese partner without their parents' knowledge or consent....
An independent security specialist, known by the nickname BobDaHacker, discovered security flaws in Pudu Robotics (the world's leading provider of commercial service robots). The vulnerabilities allowed attackers to redirect the...
California-based company Figure has unveiled another milestone for its humanoid Figure 02: the robot loaded a dishwasher with high precision using the versatile Helix model, based on the Vision-Language-Action (VLA)...
Cybercriminals have launched a new wave of attacks using SVG files to distribute phishing pages. Experts at VirusTotal have reported that attackers are impersonating the Colombian prosecutor's office, distributing email...
A recent study conducted by Workday's Offensive Security team highlighted a vulnerability in Windows drivers that effectively bypasses Endpoint Detection and Response (EDR) tools. This technique exploits direct disk reading,...
A vast Chinese cyberespionage operation, dubbed "Salt Typhoon," was recently described as the most ambitious ever attributed to Beijing. According to the report, this campaign resulted in the theft of...
A cybercriminal group, dubbed GhostRedirector by ESET researchers and linked to the Chinese ecosystem, has quietly deployed a global search engine manipulation scheme based on hacked Windows hosts. According to...
Microsoft has announced that the August 2025 Windows security updates may cause unexpected User Account Control (UAC) prompts and issues when installing apps. The bug affects non-administrator users on all...
The world of supercomputers has entered the era of exascale computing. The June 2025 TOP500 ranking recorded three American systems at the top, a sensational debut from Europe, and a...