The developers of the Redox OS operating system, written in Rust, have enabled multithreading support by default for x86 systems. Previously, the feature was experimental, but after some bug fixes,...
The Israeli government has awarded the American company Clock Tower X LLC a $6 million contract to conduct a large-scale media campaign in the United States, Nick Cleveland-Stout reports on...
The Microsoft Teams collaboration platform has become a popular target for attackers, as its widespread adoption has made it a high-value target. Messaging, calling, and screen-sharing features are being exploited...
A fire at a government data center in South Korea has reduced the country's digital infrastructure to rubble and starkly demonstrated the dangers of relying on a single hub. The...
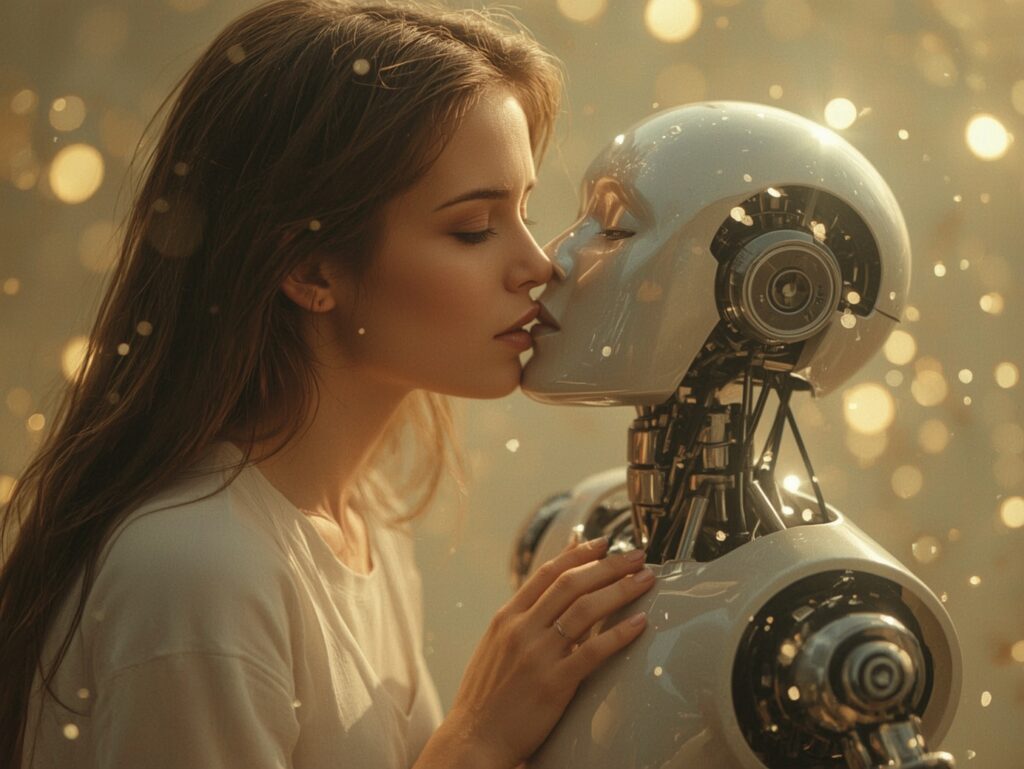
Disillusionment with online dating is increasingly pushing women to seek emotional intimacy in the virtual world. More and more women are turning to artificial intelligence, namely chatbots designed for romantic...
Amid China's long battle against cross-border fraud, authorities have issued a verdict in one of the most high-profile cases in recent years. It concerns a large-scale criminal network operating in...
In the UK, they've started testing an unusual way to heat homes: using mini data centers powered by Raspberry Pis. The project is being implemented by UK Power Networks as...
A group calling itself Scattered LAPSUS$ Hunters has resurfaced after months of silence and the arrest of its members. On a new leak site, the attackers published a list of...
OpenAI appears to be preparing ChatGPT to become a social platform, not just a traditional AI-powered chat app. The company already has Sora 2, which offers a feed of generated...
The Chinese company DeepSeek has presented an experimental version of its language model, DeepSeek-V3.2-Exp, which for the first time implements its own version of sparse attention, a technique that significantly...