OpenAI appears to be preparing ChatGPT to become a social platform, not just a traditional AI-powered chat app. The company already has Sora 2, which offers a feed of generated...
The Chinese company DeepSeek has presented an experimental version of its language model, DeepSeek-V3.2-Exp, which for the first time implements its own version of sparse attention, a technique that significantly...
An unknown iPad with an M5 chip has been spotted on Geekbench . The device scored 4,133 in the single-core test and 15,437 in the multi-core test . The listing...
China is preparing to launch one of the first commercial underwater data center projects . In mid-October, a capsule containing servers will be lowered into the sea off the coast...
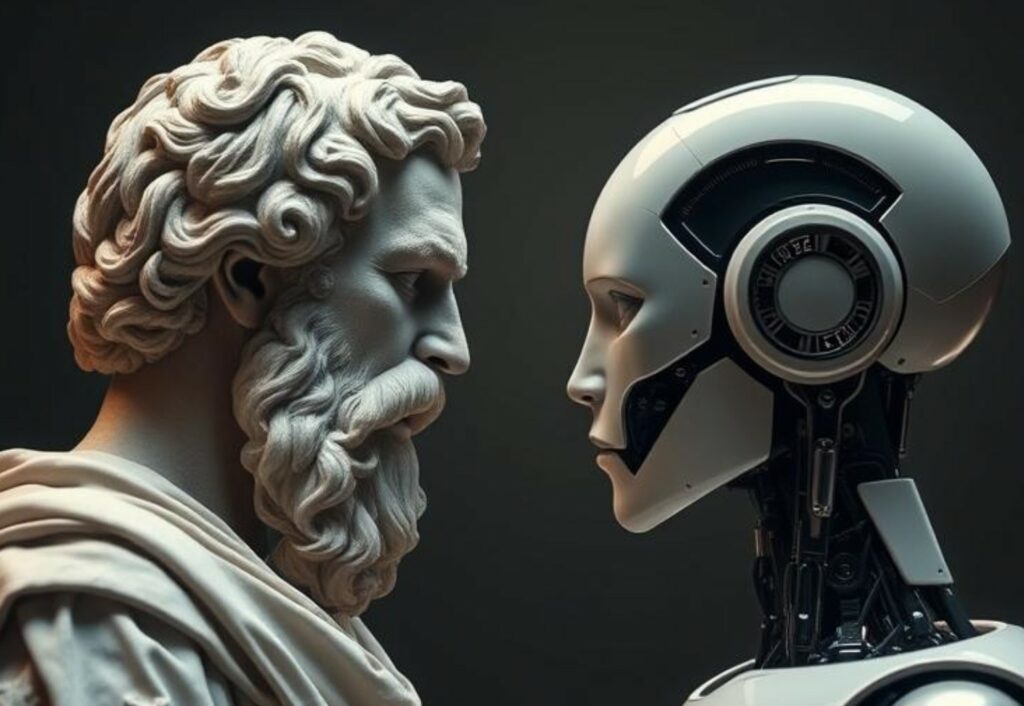
In 1950, Alan Turing, considered the father of artificial intelligence, was still wondering "Can machines think?" Today, more than seventy years later, public perception seems to have changed radically: more...
Antibiotics for inflammatory bowel disease can be a double-edged sword. While they suppress inflammation, they also kill beneficial bacteria, not just harmful ones. This often worsens symptoms. In this situation,...
A third-party customer service provider was compromised by hackers, who gained access to partial payment information and personally identifiable information for some Discord users. The attack, which occurred on September...
On October 2, the Financial Times published an analysis by Mike Kuiken, a senior national security adviser and fellow at the Hoover Institution. The expert warned of a little-discussed but...
The United Kingdom has again attempted to force Apple to access encrypted backups of user data stored on iCloud . The new request comes six months after the company disabled...
A post recently appeared on a popular underground forum that's attracting the attention of the cybersecurity community. A user with the handle KaruHunters , already known for his activities within...