The new cable cutter, developed by the China Shipbuilding Research Center, is designed for use on advanced submarines such as the Fengdou and Haidou series. The device is capable of...
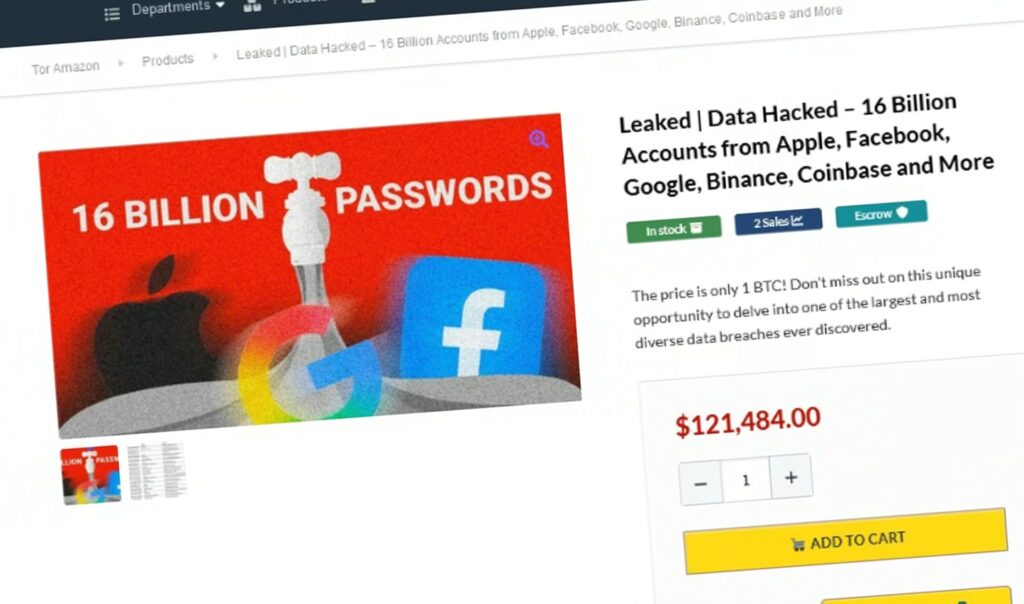
The Darklab team, Red Hot Cyber's community of threat intelligence experts, has identified an ad on the dark web marketplace "Tor Amazon", the criminal counterpart of the popular e-commerce site...
Chess.com, the online chess giant, has reportedly suffered a data breach that exposed the personal information of 4,541 individuals, according to a filing with the Maine Attorney General's Office. The...
In recent years, a particularly insidious form of phishing has become widespread: Quishing or QRishing, a strategy based on the use of QR codes containing malicious links that, once scanned,...
An advanced backdoor system associated with the notorious Russian cyberespionage group APT28 allows attackers to download data, upload files, and issue commands to infected PCs. This recently discovered, next-generation backdoor...
Today, Thursday, September 4, 2025, US President Donald Trump will host over two dozen technology and business leaders for a dinner in the newly renovated White House Rose Garden. An...
Microsoft today introduced POML (Prompt Orchestration Markup Language), a new markup language for prompt orchestration and specifically designed to enable rapid and structured prototyping of large language models (LLMs). POML...
A unified and secure approach to support digital transformation, enable hybrid working, and reduce operational complexity. By Federico Saraò, Specialized System Engineer SASE, Fortinet Italy The nature of a company's...
Automaker Jaguar Land Rover (JLR) announced that it was forced to disable several systems due to a hacker attack. The incident appears to have impacted the automaker's manufacturing and retail...
The record for the largest DDoS attack ever recorded in June 2025 has already been broken. Cloudflare said it recently blocked the largest DDoS attack in history, which peaked at...