The Chinese company Zhaoxin presented a new generation of KH-5000 server processors at Expo 2025 in Shanghai. These chips are intended for the domestic market and should significantly strengthen the...
In the first months of Donald Trump's new presidency, the U.S. federal government made drastic cuts to cybersecurity spending, cutting budgets, staff, and a range of initiatives aimed at protecting...
In red teaming, the term "tailgating" refers to a technique in which a team member attempts to gain unauthorized access to a protected area or computer system, such as by...
Living off the land means surviving on what you can forage, hunt, or grow, making the most of what nature provides. There could be multiple reasons for doing this: maybe...
The Lovense platform, which has long carved out a niche market for itself with app-controlled sex toys (including models such as Lush, Gush, and Kraken), is affected by a security...
Physicists at Aalto University (Finland) have set a new world record for the duration of the coherent state of a superconducting qubit, the core of a quantum computer. They achieved...
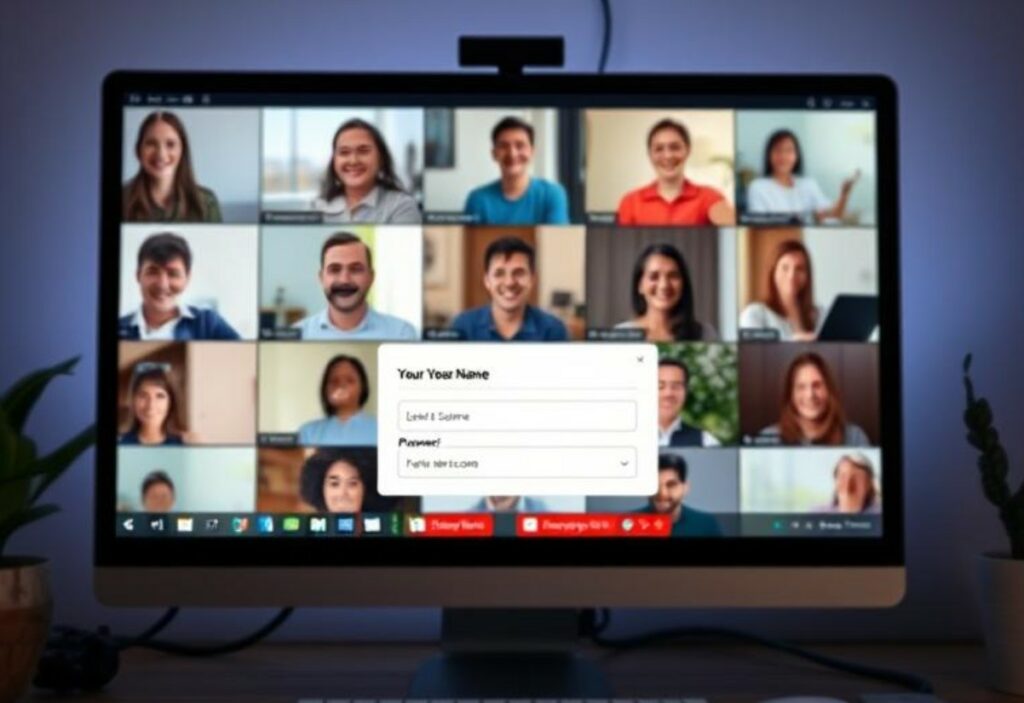
A phishing attack that mimics an urgent Zoom meeting is being used by cybercriminals to steal corporate credentials, using a fake interface so realistic it's nearly indistinguishable from a real...
The FBI has issued a warning about a rapidly growing threat from IRL Com, a subgroup of the underground group The Com that actively recruits teenagers to commit real-world crimes....
The compromise of a widely used JavaScript library has put millions of projects worldwide at risk. The package in question has been a fundamental, yet unnoticed, component of the Node.js...
If weeds aren't pulled out by the roots, they'll grow back, much more vigorous than before. This is cybercrime, and this is the new rebirth, the fifth ever from the...