Ransomware Exploits SharePoint! 4L4MD4R Discovered, the Hybrid Attack That’s Even Scare Governments
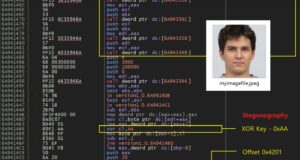
A massive campaign to exploit a series of vulnerabilities in Microsoft SharePoint continues to gather pace, now involving ransomware groups. While analyzing the series of attacks, Palo Alto Networks (Unit 42) discovered the introduction of the 4L4MD4R ransomware, a variant based on the open source code of Mauri870. Its activity is directly related to a series of exploits called ToolShell. The first infection was detected on July 27, when a loader malware was detected that received and launched 4L4MD4R from the server theinnovationfactory[.]it at IP address 145.239.97[.]206. The reason for the detection was an unsuccessful exploit attempt involving PowerShell commands aimed at