
A new threat is lurking, exploiting our greatest weakness: habit.
How many times, in fact, do you find yourself clicking on verification boxes without thinking twice? Now, it seems that malicious people have created a new malware campaign that uses fake CAPTCHAs to trick users into executing commands on their PCs. In short, it’s as if the user has been tricked and, without realizing it, has opened the door to their data to strangers.
The attack is not limited to a simple click, but requires manual manipulation by the victim, a detail that makes the infection particularly effective at bypassing defenses built to detect obvious threats.
It all begins with a socially engineered message prompting the user to prove they’re not a robot. Instead of selecting images, the victim is asked to paste and manually execute a command in the Windows “Run” dialog box. This critical step allows attackers to initiate an infection chain that exploits legitimate operating system tools to disguise themselves as normal administrative activity.
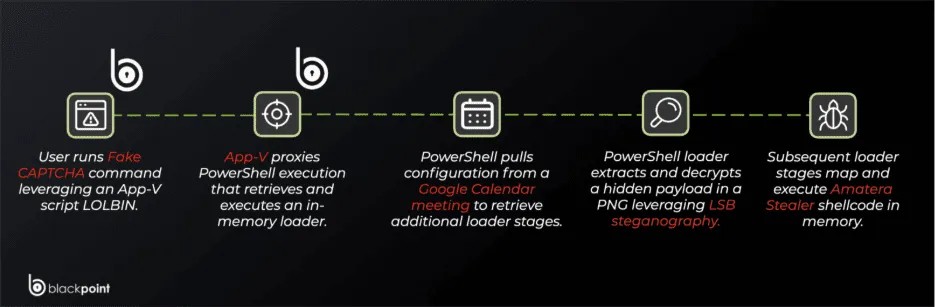
To evade controls, cybercriminals use a technique that relies on trusted components. Instead of launching PowerShell directly, the attack is delivered through a legitimate Windows script called SyncAppvPublishingServer.vbs. This component, normally dedicated to managing virtualized applications, acts as a ” LOLBIN ” (Living Off the Land Binary) to control how execution begins.
Through this method, the process appears as an ordinary system activity, allowing malicious code to slip past monitoring environments.
The campaign is designed to activate only when the user completes the required manual steps; otherwise, the process silently stops. This strategic behavior significantly complicates malware analysis by security systems that attempt to automatically identify suspicious payloads.
One of the distinctive features of this operation is the abuse of trusted cloud infrastructures. Once a victim’s presence is confirmed, the malware doesn’t contact a suspicious server, but downloads its configuration from a public file hosted on Google Calendar. By using a standard .ics file, attackers can maintain flexible delivery logic without having to modify files already sent.
Using such a common service ensures that network traffic appears completely harmless to defense tools. This operational choice allows criminals to leverage third-party infrastructure to manage the attack phases, maintaining control over the instructions the malware must follow. This is an effective method for hiding malicious directives within a data stream that most companies consider secure.
The final stage of delivery uses steganography to hide the malicious code. The malware downloads seemingly benign PNG images from public hosting sites . Concealed within the pixels of these photos is an encrypted payload that is extracted, decrypted, and unpacked entirely in the computer’s memory. This means execution switches from PowerShell to native code without leaving any obvious traces.
The end result is the activation of Amatera Stealer, a software designed to harvest credentials and data from victims’ browsers. While the payload is a known threat, it’s the distribution method that concerns experts. The combination of Microsoft scripts and Google Calendar maximizes the attack’s reliability, ensuring it only works when intended.
According to research published by Blackpoint SOC , this campaign demonstrates a deliberate pursuit of maximum invisibility along the entire infection chain.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
