
Attraverso la funzionalità Component Object Model (COM) di BitLocker, gli aggressori possono mettere in atto una tecnica innovativa di pivoting, finalizzata all’esecuzione di codice malevolo sui sistemi presi di mira. Questo approccio, presentato tramite uno strumento di prova chiamato BitLockMove, segna un progresso significativo nelle strategie di movimento laterale, riuscendo a eludere i metodi di individuazione standard grazie all’utilizzo di elementi Windows autentici.
Solitamente abilitato su workstation e laptop per impedire l’accesso non autorizzato in caso di furto o smarrimento del dispositivo, la protezione completa di BitLocker lo ha reso un bersaglio allettante per gli aggressori che cercano di abusare della sua infrastruttura sottostante.
Durante la sua presentazione, il ricercatore Fabian Mosch ha illustrato che l’aggiunta di ogni applicazione o funzionalità a Windows comporta un aumento sostanziale degli oggetti, comprendenti processi, file e chiavi di registro, i quali, nel loro insieme, ampliano la superficie esposta a potenziali attacchi. Nonostante l’efficacia di BitLocker nella protezione dei dati non attivi, gli esperti hanno rilevato che la sua implementazione include aspetti che possono essere sfruttati dai malintenzionati più esperti per creare strumenti offensivi.
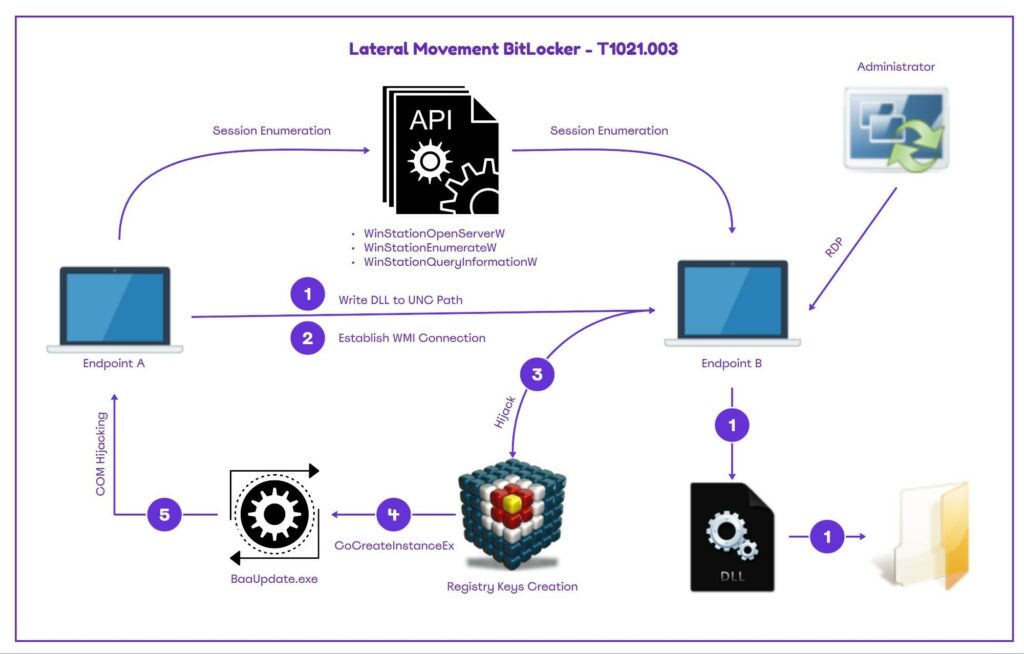
La tecnica appena divulgata mira alla manipolazione remota delle chiavi del registro di sistema di BitLocker tramite Windows Management Instrumentation (WMI) per dirottare specifici oggetti COM. Questo approccio consente agli aggressori di eseguire codice nel contesto dell’utente interattivo sugli host di destinazione, portando potenzialmente all’escalation del dominio se l’utente compromesso possiede privilegi elevati, come i diritti di amministratore di dominio.
Una falla critica nella struttura gerarchica degli oggetti COM di BitLocker è sfruttata dall’attacco, che punta direttamente alla classe BDEUILauncher attraverso l’interfaccia IBDEUILauncher. Gli aggressori possono utilizzare tre metodi principali offerti da questa interfaccia per il loro sfruttamento:
Il processo di exploit si concentra sul CLSID ab93b6f1-be76-4185-a488-a9001b105b94, che genera quattro processi diversi come utente interattivo. Tra questi, il processo BaaUpdate.exe si dimostra particolarmente vulnerabile al COM hijacking quando eseguito con parametri di input. L’attacco prende di mira specificamente il CLSID mancante A7A63E5C-3877-4840-8727-C1EA9D7A4D50, che il processo BaaUpdate.exe tenta di caricare.
Creando una voce di registro per questo CLSID e stabilendo le sottochiavi appropriate, gli aggressori possono reindirizzare il processo per caricare codice dannoso invece del componente legittimo, ha affermato Fabin . Lo strumento BitLockMove dimostra l’implementazione pratica di questa tecnica attraverso due modalità operative:
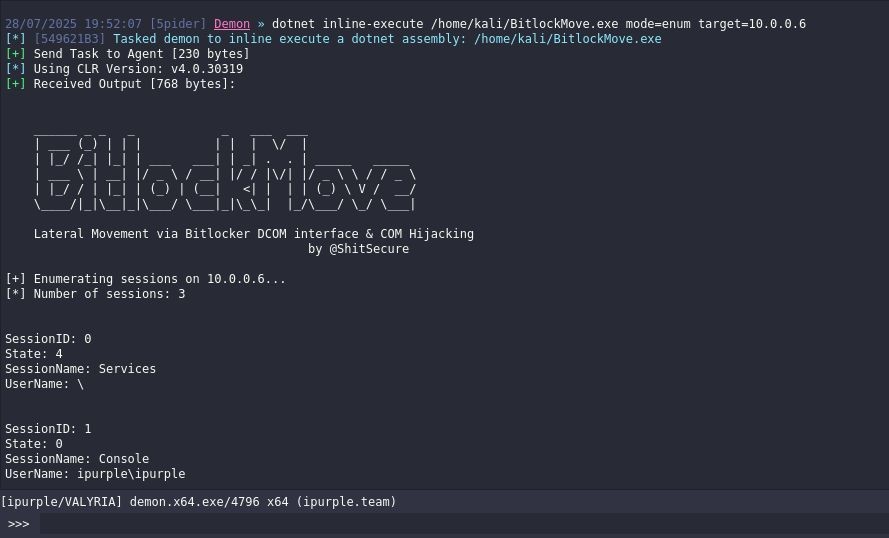
Il processo BdeUISrv.exe rimane attivo sul sistema, a differenza del processo vulnerabile al COM hijacking BaaUpdate.exe che viene terminato.
È importante notare che il processo BdeUISrv.exe è stato eseguito nel contesto dell’utente Amministratore, ovvero l’utente che aveva la sessione interattiva sull’host ed è stato preso di mira.
Sebbene la tecnica tenti di integrarsi nell’ambiente, poiché il comando arbitrario viene eseguito nel contesto di un processo BitLocker attendibile (BdeUISrv.exe ), esistono molteplici opportunità di rilevamento in varie fasi. L’analisi del comportamento dello strumento può rivelare le caratteristiche della tecnica e le aree su cui gli ingegneri del rilevamento dovrebbero concentrarsi.
La tecnica di spostamento laterale tramite dirottamento del modello a oggetti dei componenti BitLocker prevede diverse fasi, ma offre anche numerose opportunità di rilevamento. Le organizzazioni dovrebbero valutare quali log sia possibile abilitare nei propri ambienti e concentrare di conseguenza i propri sforzi di ingegneria del rilevamento.
L’arricchimento del SIEM con tutti i log associati e l’esecuzione di query di threat hunting a breve frequenza consentono il rilevamento con un elevato livello di affidabilità.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…