
A metà agosto, i ricercatori hanno incontrato il ransomware Cephalus in due incidenti separati. Tra le recenti emergenze di famiglie come Crux e KawaLocker, una richiesta di riscatto che iniziava con le parole “Siamo Cephalus” ha attirato l’attenzione. In entrambi i casi, gli aggressori hanno ottenuto l’accesso iniziale tramite RDP utilizzando credenziali compromesse senza autenticazione a più fattori e hanno utilizzato il servizio cloud MEGA per potenzialmente far trapelare i dati.
L’aspetto più rilevante della catena di attacco è stato il metodo di lancio del ransomware. I criminali hanno fatto ricorso alla sostituzione delle DLL utilizzando il componente legittimo SentinelOne: il file SentinelBrowserNativeHost.exe è stato avviato dalla directory Download, prelevando la libreria SentinelAgentCore.dll, che a sua volta ha caricato il file data.bin con il codice ransomware.
Su uno degli host, il tentativo è stato bloccato da Microsoft Defender, mentre sull’altro è stata avviata la crittografia. Non sono stati rilevati parametri della riga di comando durante l’avvio, il che indica indirettamente l’assenza di una distribuzione “di rete” tra le condivisioni disponibili.
È importante sottolineare che entrambe le organizzazioni interessate utilizzavano effettivamente i prodotti SentinelOne. Allo stesso tempo, il fatto che SentinelBrowserNativeHost.exe sia finito nella cartella Download appare insolito: la telemetria ha mostrato milioni di avvii legittimi di questo file eseguibile nelle infrastrutture dei clienti al giorno, ma non dalla cartella Download degli utenti, il che rende tale posizione un buon indicatore di attività sospetta. I moderni sistemi SIEM sono in grado di rilevare tali anomalie: ad esempio, la regola DLL_Side_Loading in MaxPatrol SIEM rileva la sostituzione della creazione della libreria nella cartella con il file binario e il suo successivo caricamento nel processo.
Prima della crittografia, Cephalus cerca di privare il sistema di qualsiasi possibilità di ripristino e di accecare le difese. E’ stato osservato l’eliminazione delle copie shadow del volume e una sequenza di comandi PowerShell e modifiche al registro volte a disabilitare i componenti di Windows Defender , aggiungere esclusioni e interrompere i servizi correlati. Queste azioni hanno preceduto la creazione della nota e il processo di crittografia stesso, il che corrisponde alle tattiche tipiche dei gruppi moderni.
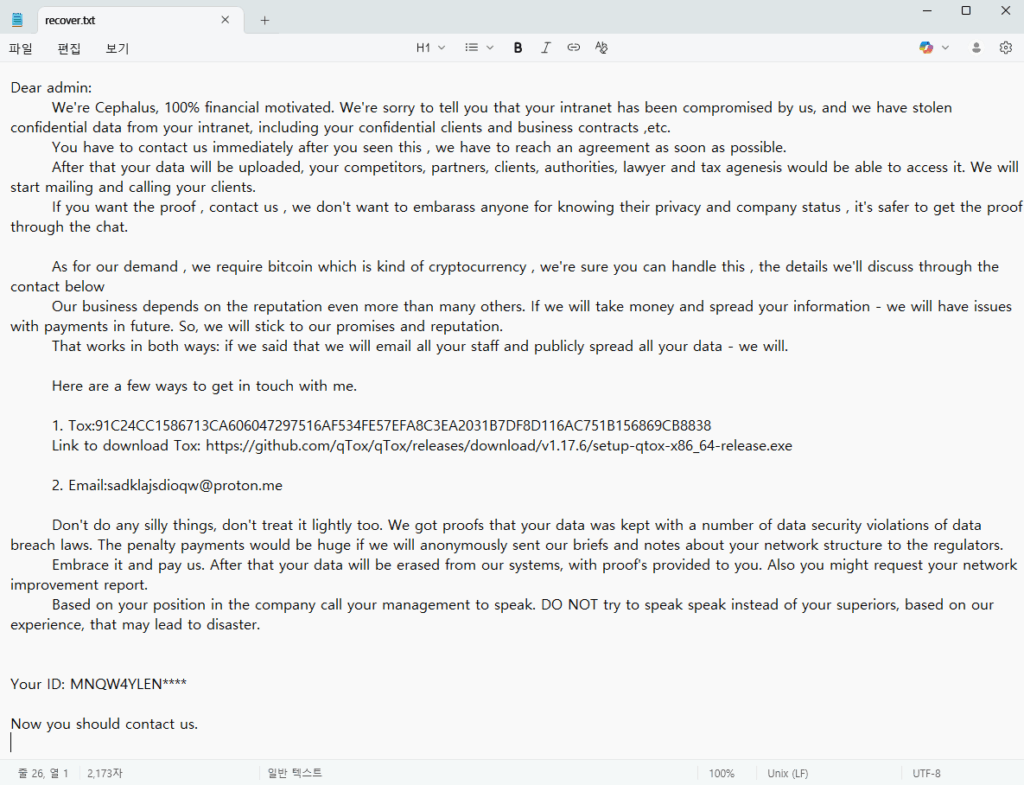
Un altro dettaglio sono le note con le richieste. Nei casi rilevati, il testo iniziava con una presentazione diretta (“Siamo Cephalus”), conteneva affermazioni sul furto di “dati riservati” e istruzioni per contattarli. A differenza delle varianti precedentemente pubblicate sui social network, la nota era indirizzata al dominio dell’organizzazione vittima e includeva link a due “articoli di giornale” su precedenti attacchi Cephalus, presumibilmente per aumentare la pressione e dare un’apparenza di “notorietà“. In alcuni casi, alla vittima veniva chiesto di seguire il link GoFile e, con una password, di controllare un campione dei file presumibilmente rubati.
In entrambi gli incidenti, MEGAsync non era solo un endpoint per lo scambio, ma anche nella linea di processo sull’host: MEGAcmdUpdater.exe veniva avviato e, in uno degli incidenti, persino tramite Task Scheduler. Questo rientra nel modello della doppia estorsione, in cui la crittografia è integrata da un’esfiltrazione preliminare.
L’insieme delle caratteristiche tecniche forma già un profilo riconoscibile. Le osservazioni includevano l’estensione “.sss” per i file crittografati e il file di note “recover.txt”. Gli artefatti includono il percorso C:Users[user]Downloads come directory di lavoro dell’operatore, il nome della workstation Desktop-uabs01 e i checksum dei componenti della catena: SHA-256 per SentinelBrowserNativeHost.exe – 0d9dfc113712054d8595b50975efd9c68f4cb8960eca010076b46d2fba3d2754 e per SentinelAgentCore.dll – 82f5fb086d15a8079c79275c2d4a6152934e2dd61cc6a4976b492f74062773a7.
Cephalus si inserisce nel familiare panorama dei ransomware, ma combina vecchi punti di ingresso con una tecnica di avvio non banale tramite un eseguibile legittimo. Le implicazioni pratiche per i difensori rimangono rilevanti: chiudere RDP senza MFA, monitorare lanci anomali di SentinelBrowserNativeHost.exe, soprattutto dalle directory utente, limitare o controllare l’uso di MEGA e strumenti simili e monitorare qualsiasi tentativo di interferire con le impostazioni e i servizi di Windows Defender. Maggiore è la visibilità delle azioni prima della crittografia, maggiore è la possibilità di fermare l’attacco prima che compaiano “note” e tempi di inattività.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…