
In mid-May 2025, Cloudflare blocked the largest DDoS attack ever recorded: 7.3 terabits per second (Tbps). This event comes shortly after the release of the DDoS Threat Report for Q1 2025 on April 27, 2025, which highlighted attacks reaching 6.5 Tbps and 4.8 billion packets per second (pps).
37.4 terabytes isn’t a huge number by today’s standards, but downloading 37.4 terabytes in just 45 seconds is.
That’s the equivalent of flooding the internet with over 9,350 HD movies or streaming 7,480 hours of uninterrupted high-definition video (nearly a year’s worth of back-to-back TV binge-watching) in just 45 seconds.
If it were music, you would download about 9.35 million songs in less than a minute, enough to keep a listener entertained for 57 years straight. Imagine taking 12.5 million high-resolution photos with your smartphone without ever running out of storage space: even if you took one every day, you would be clicking for 4,000 years, but in 45 seconds.
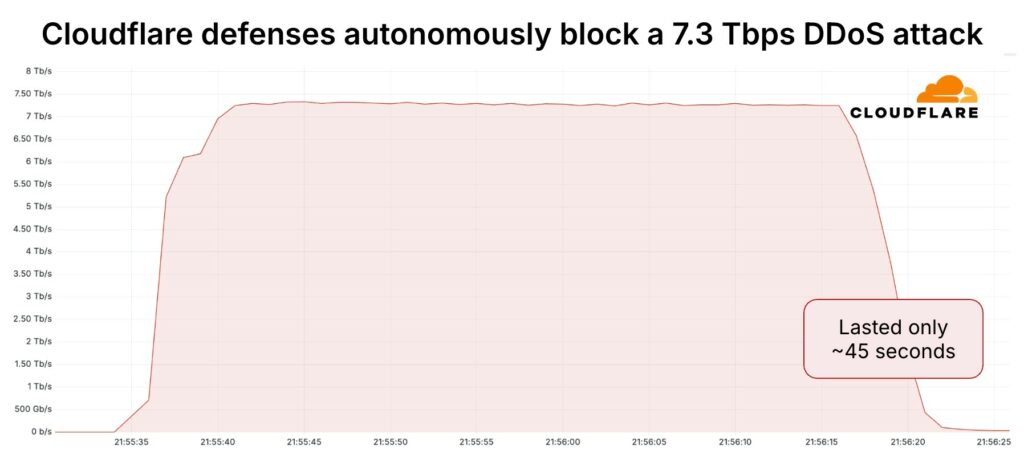
The attack targeted a customer of Cloudflare, a hosting provider, which uses Magic Transit to defend its IP network. Hosting providers and critical Internet infrastructure are increasingly being targeted by DDoS attacks, as reported in the latest DDoS threat report
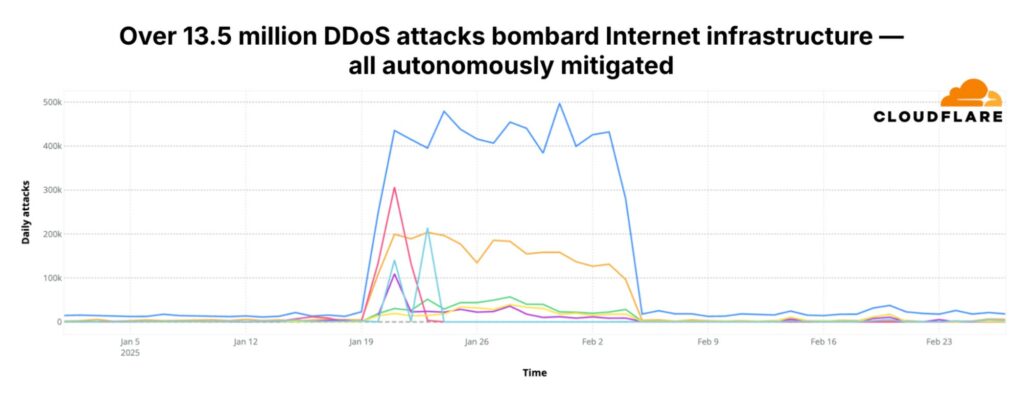
The image below shows an attack campaign conducted between January and February 2025, which resulted in over 13.5 million DDoS attacks against Cloudflare infrastructure and hosting providers protected by Cloudflare.
The attack hit an average of 21,925 destination ports of a single IP address, with a peak of 34,517 destination ports per second. The attack also originated from a similar distribution of source ports.
The 7.3 Tbps attack was a multi-vector DDoS attack. Approximately 99.996% of the attack traffic was classified as UDP floods. However, the remaining 0.004%, or 1.3 GB of the attack traffic, was identified as QOTD reflection attacks, Echo reflection attack, NTP reflection attack, Mirai UDP flood attack, Portmap flood, and RIP amplification attacks
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
