
Non è raro trovare nei videogiochi delle citazioni a delle innovazioni del mondo dell’Information Technology.
Ada Lovelace (il primo programmatore della storia), ha dato il nome al robot di follaut 4, ma anche il famoso Creeper, il mostro di Minecraft, prende il nome dal primo worm informatico della storia, del quale parleremo oggi, con questo articolo.
Ma sempre oggi scopriremo anche Reaper, il software creato per eliminare le infezioni create da Creaper, ritenuto da molti il primo software antivirus della storia.
La caratteristica più importante di un virus informatico è la sua capacità di auto-replicarsi (in un certo senso ogni programma autoreplicante può essere chiamato virus).
L’idea di programmi autoreplicanti può essere fatta risalire al 1949, quando il matematico John von Neumann immaginò computer specializzati o automi autoreplicanti, che potevano costruire copie di se stessi e trasmettere la loro programmazione alla loro progenie.

Il matematico e pioniere dell’informatica John von Neumann
Se un virus informatico ha la capacità di auto replicarsi su una rete di computer, ad esempio Internet, viene chiamato worm.
Non è noto chi abbia creato il primo programma autoreplicante al mondo, ma è chiaro che il primo worm al mondo (il cosiddetto Creeper worm) è stato creato dall’ingegnere della BBN Robert (Bob) H. Thomas intorno al 1970.
La società BBN Technologies (originariamente Bolt, Beranek e Newman) era un’azienda ad alta tecnologia, con sede a Cambridge, in Massachusetts, che ha svolto un ruolo estremamente importante nello sviluppo delle reti a commutazione di pacchetto (tra cui ARPANET e Internet).
Un certo numero di noti luminari del computer hanno lavorato alla BBN, tra cui Robert Kahn , JCR Licklider , Marvin Minsky, Ray Tomlinson, ecc. Tra di loro c’era il ricercatore Robert H. (Bob) Thomas, che lavorava in un piccolo gruppo di programmatori che stavano sviluppando un sistema di time sharing chiamato TENEX, che girava su un Digital Equipment Corporation PDP-10.

Il DEC PDP-10
Il primo modello del PDP-10 (KA10), aveva una grande configurazione: delle unità disco e stampante, DECtapes e grandi armadi di memoria con nastri a 9 tracce. Appena sopra il pannello di controllo e sotto l’unità DECtape, si trova il lettore/perforatrice di nastri di carta.
Chiariamoci, il Creeper non era un vero worm, ma era in realtà un programma sperimentale autoreplicante, non destinato a danneggiare, ma a dimostrare che un programma potesse replicarsi in maniera autonoma.
Creeper era scritto in assembly PDP-10, girava sul vecchio sistema operativo Tenex (Tenex è il sistema operativo che ha visto i primi programmi di posta elettronica, SNDMSG e READMAIL, oltre all’uso del simbolo “@” sugli indirizzi di posta elettronica), e usava l’ARPANET (predecessore dell’attuale Internet) per infettare altri computer DEC PDP-10 che eseguono il TENEX.
Creeper, una volta che aveva “infettato” un altro computer, scriveva il seguente messaggio “I’M THE CREEPER : CATCH ME IF YOU CAN”, ovvero “sono il Creeper, prendimi se puoi”.
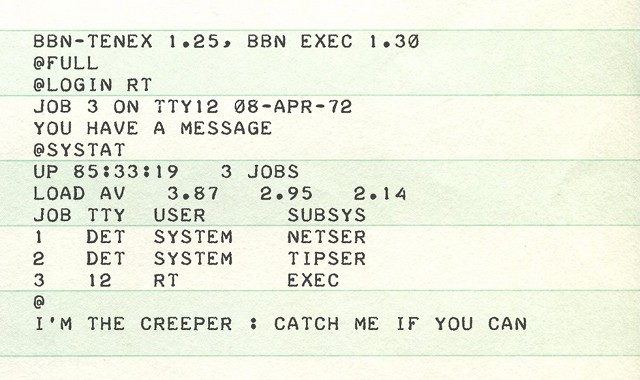
Un modulo continuo con la stampa di Creeper
Il Creeper, subito dopo aver mostrato il messaggio di testo, iniziava a stampare un file (come riportato sopra), ma poi si fermava fino a quando non trovava un altro sistema Tenex, sul quale aprire una nuova connessione, trasferirsi sull’altra macchina e quindi ricominciare tutto da capo. Insomma, ben diverso dagli attuali ransomware, non è vero?
Il programma raramente si è replicato da solo, piuttosto si è “spostato” da un sistema all’altro, tentando di rimuoversi dai sistemi precedenti mentre si propagava in avanti, quindi Creeper non ha installato più istanze di se stesso su diversi obiettivi e probabilmente è ritornato sulle stesse macchine più di una volta.
Le tecniche sviluppate in Creeper sono state successivamente utilizzate nel McROSS “Multi-computer Route Oriented Simulation System”, un simulatore di traffico aereo, per consentire a parti della simulazione di muoversi attraverso la rete.
Non è chiaro quanti danni (se presenti) il Creeper abbia effettivamente causato. La maggior parte delle fonti afferma che il worm era poco più di un fastidio. Alcune fonti affermano che Creeper si è replicato così tante volte, che ha spiazzato altri programmi, ma l’entità del danno non è specificata. Ad ogni modo, è stato subito rivelato il problema chiave, ovvero il controllo di questi programmi malevoli.
Il programma Creeper ha portato a ulteriori lavori, inclusa una versione di un collega di Thomas, Ray Tomlinson (l’inventore della posta elettronica), che non solo si è mosso attraverso la rete, ma si è anche replicato.
Ma per completare questo Creeper “potenziato”, è stato creato il programma Reaper, che si muoveva attraverso la rete, replicandosi, cercando di trovare delle copie di Creeper attive e quindi disconnetterle.
Quindi, se Creeper è stato il primo worm, allora Reaper è stato il primo software antivirus.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…