
Il più grande costruttore navale francese per la difesa, Naval Group, sta affrontando un incidente di sicurezza informatica potenzialmente grave a seguito delle affermazioni degli autori della minaccia che riportano di aver compromesso sistemi interni critici, compresi quelli legati alle operazioni navali militari francesi.
Gli hacker hanno pubblicato la presunta violazione su un noto forum specializzato in fughe di dati, sostenendo di aver avuto accesso a materiale sensibile come il codice sorgente dei sistemi di gestione del combattimento (CMS) utilizzati nei sottomarini e nelle fregate francesi. Gli aggressori non mirano a vendere i dati rubati, ma a estorcere denaro all’appaltatore della difesa, minacciando di divulgare informazioni riservate se le loro richieste non saranno soddisfatte.
Naval Group, con sede a Parigi e oltre 15.000 dipendenti, è un importante fornitore di soluzioni navali di livello militare in tutta Europa. Con un fatturato annuo superiore a 5 miliardi di dollari (4,3 miliardi di euro), l’azienda è di proprietà congiunta del governo francese e del gigante dell’elettronica per la difesa Thales Group.
Disclaimer: Questo rapporto include screenshot e/o testo tratti da fonti pubblicamente accessibili. Le informazioni fornite hanno esclusivamente finalità di intelligence sulle minacce e di sensibilizzazione sui rischi di cybersecurity. Red Hot Cyber condanna qualsiasi accesso non autorizzato, diffusione impropria o utilizzo illecito di tali dati. Al momento, non è possibile verificare in modo indipendente l’autenticità delle informazioni riportate, poiché l’organizzazione coinvolta non ha ancora rilasciato un comunicato ufficiale sul proprio sito web. Di conseguenza, questo articolo deve essere considerato esclusivamente a scopo informativo e di intelligence.
Di seguito il post tradotto in lingua italiana presente all’interno del forum underground.
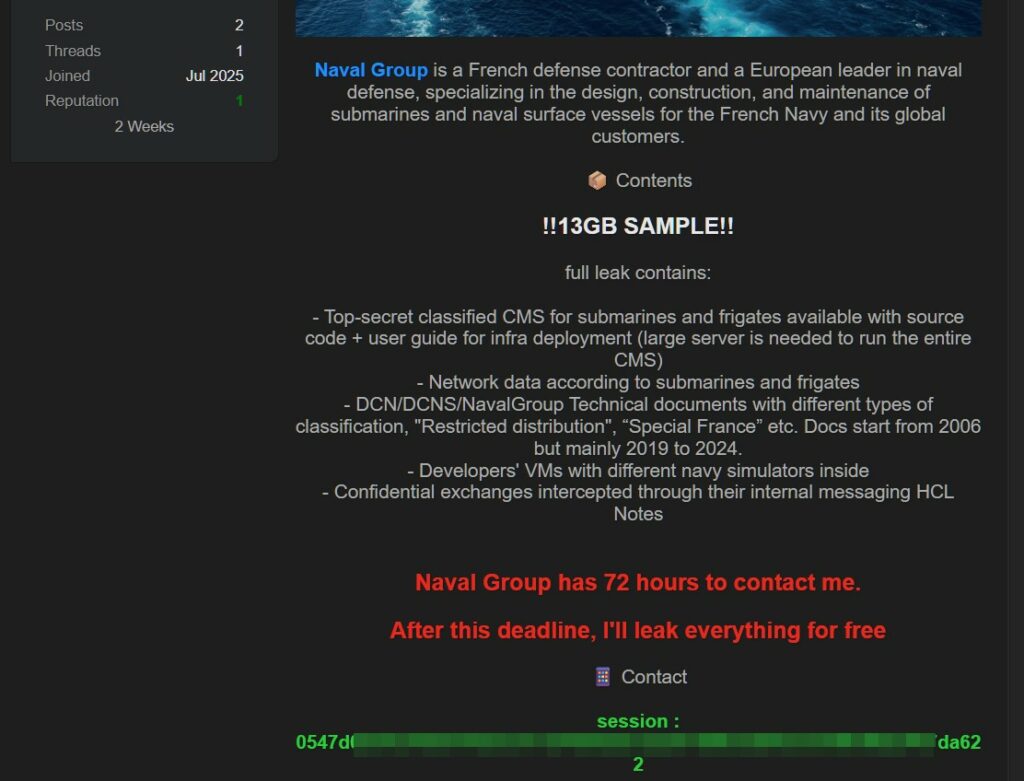
la perdita completa contiene:
- CMS top secret classificato per sottomarini e fregate disponibile con codice sorgente + guida utente per l'implementazione infrastrutturale (è necessario un server di grandi dimensioni per eseguire l'intero CMS)
- Dati di rete in base ai sottomarini e alle fregate
- Documenti tecnici DCN/DCNS/ Naval Group con diversi tipi di classificazione, "Distribuzione limitata", "Francia speciale", ecc. I documenti iniziano dal 2006, ma principalmente dal 2019 al 2024.
- VM degli sviluppatori con diversi simulatori della marina al loro interno
- Scambi riservati intercettati tramite la loro messaggistica interna HCL Notes
Naval Group ha 72 ore per contattarmi.
Dopo questa scadenza, farò trapelare tutto gratuitamente
Secondo il post condiviso dai criminali informatici, durante la violazione sarebbe stato effettuato l’accesso ai seguenti asset:
Gli aggressori hanno anche incluso nel loro post un campione di dati di 13 GB come prova. Tra i file trapelati ci sono risorse multimediali, tra cui anche dei video.
La prospettiva che soggetti stranieri o gruppi criminali possano ottenere accesso al software che governa i sistemi di combattimento a bordo di navi militari operative è estremamente allarmante. Se confermata, la divulgazione del codice sorgente e della documentazione riservata del CMS (Combat Management System) non solo comprometterebbe l’integrità tecnologica di Naval Group, ma costringerebbe anche il Ministero delle Forze Armate francese a costosi interventi correttivi, tra cui audit di sicurezza, aggiornamenti dei sistemi e verifiche approfondite.
Sebbene la reale entità dei danni e la portata della violazione non siano ancora stati verificati, è noto che gli aggressori mossi da finalità estorsive tendono a sovrastimare il valore e l’impatto delle informazioni sottratte, per aumentare la pressione psicologica e finanziaria sulle vittime. Resta da capire se questo sia uno di quei casi.
Fondato nel XVII secolo e precedentemente noto come DCN (Direction des Constructions Navales), Naval Group occupa da sempre un ruolo centrale nella strategia di difesa marittima francese. L’azienda ha realizzato, tra l’altro, l’unica portaerei francese a propulsione nucleare, la Charles de Gaulle, a testimonianza della sua importanza strategica per le capacità difensive del Paese.
Una compromissione dell’infrastruttura digitale di Naval Group non si limiterebbe a esporre dati operativi sensibili, ma evidenzierebbe anche la crescente vulnerabilità degli appaltatori militari di alto profilo in Europa. L’esito di questa possibile violazione, se confermata, potrebbe avere conseguenze rilevanti e durature sulla sicurezza nazionale francese e sulla strategia industriale di cybersecurity.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…