
Security flaws have been discovered in network communication between Microsoft Defender for Endpoint (DFE) cloud services , allowing attackers, following a breach, to bypass authentication, manipulate data, release sensitive information, and even upload malicious files within investigation packages.
A recent analysis by InfoGuard Labs detailed these vulnerabilities , which highlight the risks still present within Endpoint Detection and Response (EDR) systems, which could undermine incident management efforts.
The main concern, as identified by InfoGuard Labs , is requests sent by the agent to endpoints, such as https://[location-specific-host]/edr/commands/cnc, to execute specific commands, including isolation, forensic data collection, or scanning.
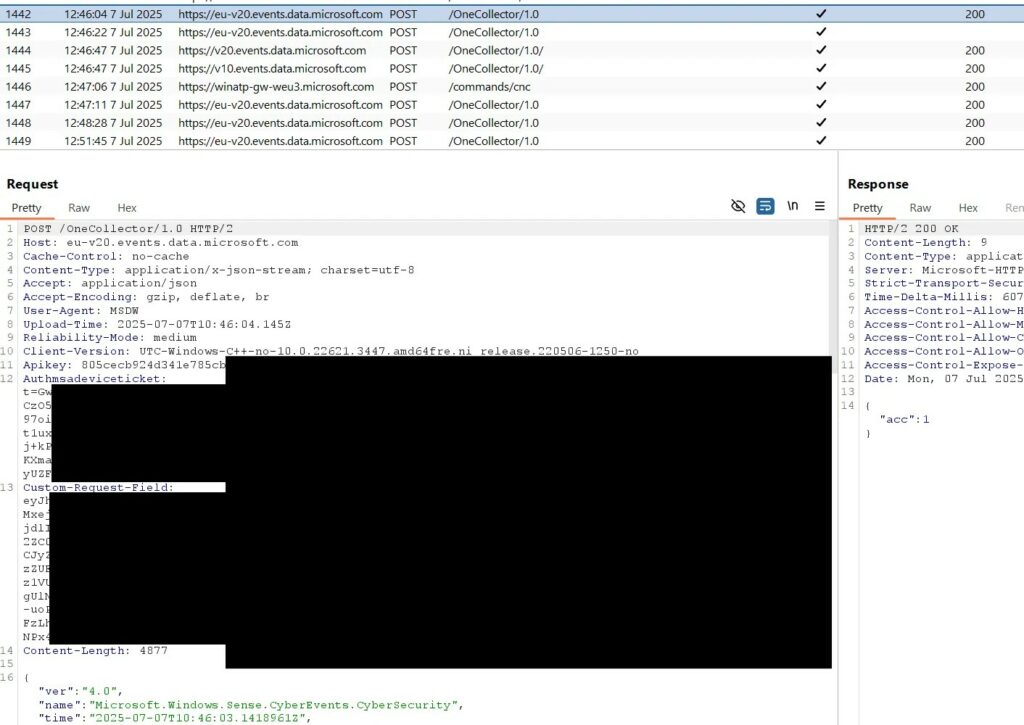
The research builds on previous explorations of EDR attack surfaces, focusing on the agent’s interaction with cloud backends. By intercepting traffic using tools like Burp Suite and bypassing certificate pinning via memory patches in WinDbg, the analysis revealed how DFE’s MsSense.exe process handles commands and data loading.
Certificate pinning, a common security measure, has been circumvented by modifying the CRYPT32!CertVerifyCertificateChainPolicy function to always return a valid result, allowing plaintext inspection of HTTPS traffic. Similar patches have been applied to SenseIR.exe for full interception, including Azure Blob uploads.
A low-privileged user can easily obtain the machine ID and tenant ID by reading logs, allowing an attacker to impersonate the agent and intercept its responses. For example, an intrusion prevention tool like Burp’s Intruder can continuously query the endpoint, stealing available commands before the legitimate agent receives them.
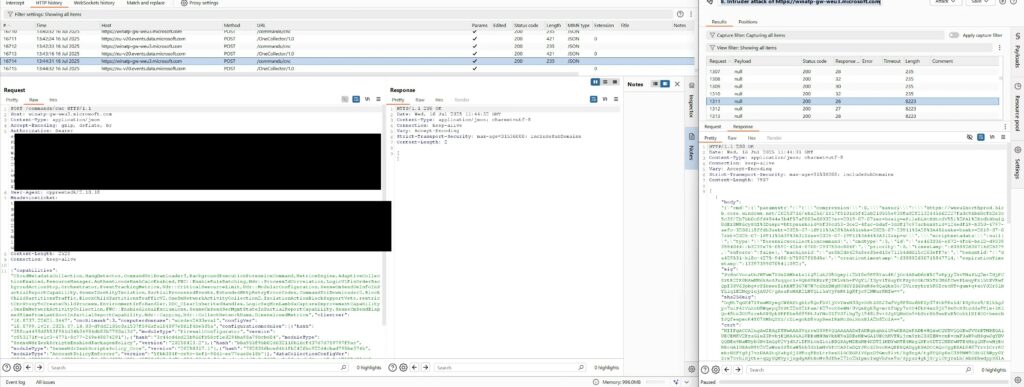
A parallel vulnerability affects the /senseir/v1/actions/ endpoints for Live Response and Automated Investigations. In this case, CloudLR tokens are similarly ignored and can be obtained without authentication using only the machine ID.
Attackers can decode action payloads with custom scripts by leveraging large language models for deserialization and upload fabricated data to Azure Blob URIs provided via SAS tokens, which remain valid for months. Unauthenticated access extends to Incident Response (IR) exclusions via the registration endpoint, requiring only the organization ID from the registry.
Even more alarming is the fact that querying /edr/commands/cnc without credentials produces an 8 MB configuration dump, which includes RegistryMonitoringConfiguration, DriverReadWriteAccessProcessList, and ASR rules. While not tenant-specific, this data reveals valuable detection logic for evasion.
After the breach, attackers can enumerate file system probe packets, readable by any user, containing autorun programs, installed programs, and network connections. For ongoing investigations, spoofed uploads on these packets allow malicious files to be embedded with benign names, tricking analysts into performing the operation during review.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
