
Oltre 320 aziende sono state violate da gruppi legati alla Corea del Nord(DPRK) con attacchi potenziati dall’AI generativa. Gli attori delle minacce sfruttano gli agenti AI rendendo i sistemi autonomi il nuovo perimetro di attacco dell’ambiente aziendale
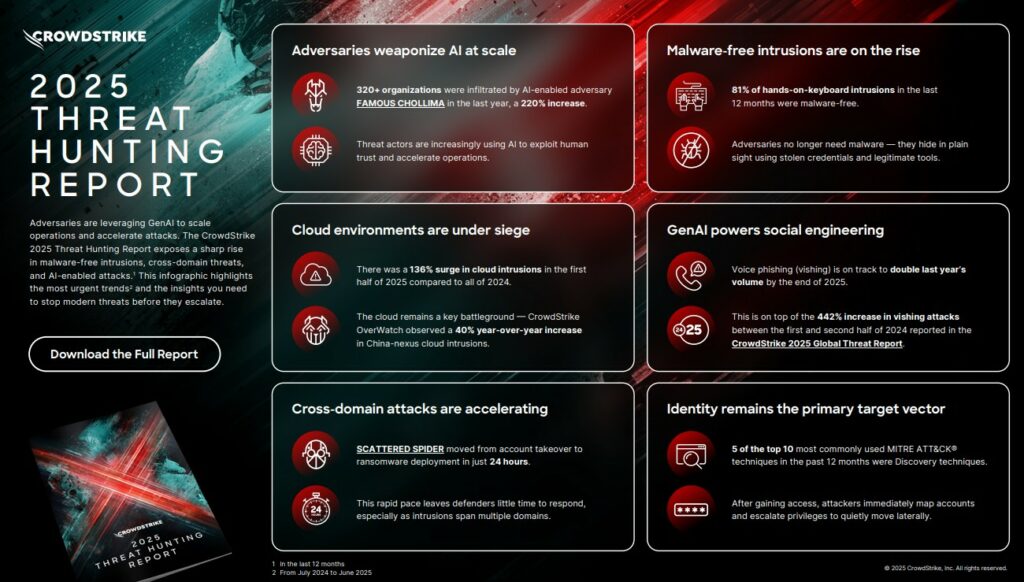
CrowdStrike ha pubblicato il Threat Hunting Report 2025, che rivela una nuova fase degli attacchi informatici moderni: gli avversari stanno sfruttando la GenAI per ampliare le operazioni e accelerare gli attacchi – prendendo sempre più di mira gli agenti di AI autonomi che stanno trasformando le attività aziendali. Il rapporto rivela come gli attori delle minacce stiano puntando agli strumenti utilizzati per sviluppare agenti AI – ottenendo accesso, rubando credenziali e diffondendo malware – un chiaro segnale che i sistemi autonomi e le identità generate dai sistemi sono diventati una componente centrale della superficie di attacco delle aziende.
Basato sulle informazioni raccolte dagli esperti di threat hunting e analisti di intelligence di CrowdStrike, che monitorano oltre 265 avversari identificati, il report rivela che:
“L’era dell’AI ha ridefinito il modo in cui le aziende operano e il modo in cui gli avversari attaccano. Stiamo vedendo i criminali usare l’AI generativa per ampliare le attività di social engineering, accelerare le operazioni e abbassare la barriera d’ingresso per le intrusioni manuali”
Ha affermato Adam Meyers, head of counter adversary operations, CrowdStrike.
“Allo stesso tempo, gli avversari stanno prendendo di mira proprio i sistemi di AI che le aziende stanno implementando. Ogni agente AI è un’identità sovrumana: autonoma, veloce e profondamente integrata, che li rende obiettivi di alto valore. Gli avversari trattano questi agenti come fossero infrastrutture, attaccandoli allo stesso modo in cui prendono di mira le piattaforme SaaS, le console cloud e gli account privilegiati. Proteggere la stessa AI che alimenta il business è il nuovo terreno su cui si sta evolvendo la guerra cibernetica oggi”.
Scarica il CrowdStrike 2025 Threat Hunting Report
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…