
Since June 12, a 700% increase in cyber activity has been detected, resulting in a wave of DDoS attacks, infiltration attempts, data theft and malware distribution against government websites, financial institutions, telecommunications companies and critical infrastructure: these operations have not created permanent damage but given the situation the risk of more effective and destructive operations remains high but also an intensification of information operations, through possible botnets on social media and disinformation campaigns to undermine public trust in institutions and amplify destabilizing narratives. It remains very difficult with an ongoing information war at this time to establish what the truths and lies are and I apologize from this moment if I will not name any group involved at the moment, even though I am very clear about the situation.
IN SHORT:
The increase in cyber activity has had a major leap especially after the Israeli kinetic attack that targeted Iranian nuclear infrastructure, especially some cyber attacks – on both sides – are visibly part of a broader strategy that has combined operations in cyberspace with air strikes and drones directed against targets strategic.
To defend themselves from such operations and contain the damage, both Iran and Israel have adopted restrictive measures such as the ban on the use of social networks especially in military bases, while Iran has imposed a blackout of 80% of the public network, blocked apps such as WhatsApp or Instagram – to avoid probable geolocation – and forced the population to use a national intranet to protect internal communications and infrastructure. Whatsapp has denied the accusations, however the information collected by these apps can be used to map human networks, identify targets for air strikes or drones, conduct psychological operations and disinformation campaigns and the “invitation” to uninstall is a preventive measure to reduce intelligence vulnerabilities and protect national security in a context of cyber and military conflict. The use of geotagging and metadata from posts and images on social media has already caused tactical damage, as in the case of the Hamas attack on the Israeli military base of Nahal Oz, facilitated by public content from soldiers. It must be said that data represents a strategic weapon and technologies based on commonly used apps amplify the capacity for surveillance and control, with impacts that go beyond individual privacy: for countries like Iran, addressing these threats requires drastic measures to reduce exposure.
As in the Russian-Ukrainian conflict, the Israeli-Iranian conflict only highlights that kinetic warfare is part of a broader hybrid war. Cyberspace has thus become a primary strategic front, with hacktivist groups, mercenaries, APTs and state-sponsored groups and government-affiliated hackers using sophisticated malware and creating disinformation campaigns to damage critical infrastructure and influence public opinion.
There is evidence of an increasingly strong alignment in the underground between the groups: hundreds of digital formations are involved and their attacks are increasingly coordinated, integrating conventional military actions with high-impact cyber operations including targeted DDoS attacks on the websites of Israeli radio stations during missile attacks, with the aim of creating confusion and hindering the spread of alarm alerts. Not only that, alleged attacks against nuclear and military research centers, with the spread of malware for stealing information, have also been published. Every cyber action on one side generates a response on the other, but DDoS attacks remain the main attack vector.
There have been highly coordinated attacks such as the attempted attack on Sepah Bank in Iran – the website appeared offline on Thursday 12th but state agency IRNA said all banking operations are running without interruption – with the intention of striking the financial capacity and Iranian morale, in parallel and DDoS attacks against Israeli government sites, which temporarily blocked access to key institutional portals and created disruption during moments of military tension. Added to this is the attack on the hot wallets of the Nobitex exchange, a critical hub in the Iranian cryptocurrency ecosystem, leading to the theft of over 100 million dollars in cryptocurrencies, including Bitcoin, Ethereum, Dogecoin, XRP and Solana. Following this, the Central Bank of Iran imposed an operational curfew for domestic cryptocurrency exchanges, limiting their operations between 10:00 a.m. and 8:00 p.m., to facilitate the management of any further attacks and better control transactions at a time of high geopolitical tension. This represents a further development in hybrid warfare and the transformation of cyberspace into a strategic front of high tension.
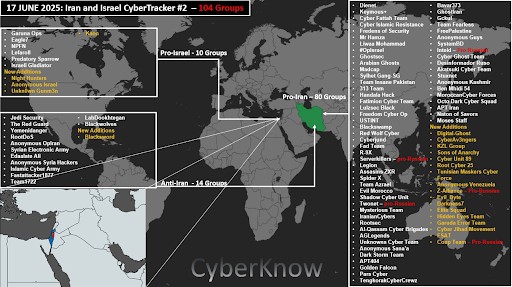
Another example of concrete alignment and disciplined coordination between hacker groups in the context of the cyber conflict between Iran and Israel was a Security Advisory distributed among the “OpIsrael” formations, i.e. instructions and protective measures of the groups to protect digital infrastructure and ensure business continuity in the context of a likely formal US involvement in the conflict.
Finally, we highlighttwo important events:
Everything we have analyzed so far tells us how the digital underground is structuring itself in an increasingly professional and strategic way, integrating cyber actions with geopolitical developments on the ground, also providing zero trust ‘military recommendations’ in line with the best practices relating to cyber security in high-risk environments against the use of intelligence techniques based on commonly used apps that amplify the capacity for surveillance and control and platforms with uncontrolled access to geolocation and metadata represent critical vulnerabilities, especially after the declarations aimed at destabilizing the regime by part of a popular revolution.
A revolution that, applying game theory to the parties involved and the possible strategies, seems like a rational move by one of the parties involved that transforms a costly military conflict into an internal game of a country, on its domestic front, but on the other hand unethical and unjust, which would violate the fundamental principles based on the sovereignty of States and the right of non-intervention in the internal affairs of a country. However, considering the game of the parties, on the one hand the success would depend on multiple factors such as the capacity for coordination, the coherence of international support and the symbolic effectiveness of targeted attacks. In the absence of these factors, the risk turns into an unfavorable balance with military escalation and regime consolidation.
Again, in many contexts, supporting an internal revolt in a country can be perceived as imperialist interference, fueling feelings of resentment and nationalism. This could also damage the international image of those who intervene and complicate the construction of a global consensus.
Whereas, instead, better economic stability with a country’s greater international weight could lead to possible concessions and a democratic transition. Recent history shows that situations of isolation, economic crisis and international pressure often strengthen the most rigid and authoritarian positions within a regime, while greater prosperity and global integration can favor political openings and reforms.
In the current context, sanctions and hybrid warfare (cyber and military) have contributed to hardening the Iranian position and strengthening the security apparatus, limiting the space for dialogue and reform, while an economically stable and isolated population has little possibility to influence the political process. If Iran could instead count on sustained economic growth, foreign investment and a gradual normalisation of international relations following an easing of sanctions, the leadership would have more room to negotiate, make concessions and perhaps start a more inclusive transition, without perceiving every opening as an existential threat.
At such a delicate moment at the international level, the SPIEF 2025 (St. Petersburg International Economic Forum) concluded, attended by around 20,000 guests from 140 countries, including official delegations from China, India, Indonesia, South Africa, ASEAN, the Middle East, Latin America, CIS and EAEU, highlighting the the vast international scope and emphasizing that Russia is absolutely not isolated, something that Donald Trump, President of the United States, recognizes very well, being pragmatically aware of it. Precisely for this reason he proposed at the G7 held in Canada to reintegrate Russia, but not only that, to promote peace and international dialogue he proposed to also include China in the group, despite strong criticism from other world leaders. (Reactions to the G7 also came from hacktivists from both oppositions, highlighting the rather complex moment where diplomacy is proving to be complicated, especially the position supported by Italy which however reaffirmed its commitment to promoting dialogue and peace, the de-escalation of hostilities, the ceasefire in Gaza and the importance of protecting civilians).
Trump’s proposal should be seen as a function of facilitating agreements and with the intent of reducing global tensions, recognizing in fact that Russia is not isolated and that diplomacy should involve all the major players. Peace and international dialogue are in fact fundamental because they go well beyond the simple absence of conflict or violence; represent an active process of building positive, just and lasting relationships between States, communities and individuals, based on mutual respect rather than fear.
If these same rules were applied to cyberspace we could witness a profound and positive transformation in this crucial area of our digital life based on 5 factors:
Aware that this is a romantic vision of the world, we must also realize that there are military and strategic, economic and technological interests and a shared global legal framework that instead highlight a high risk and a climate of competition that is reflected in the strategies global, where vital digital infrastructures become strategic levers, innovation such as artificial intelligence (AI) translates into an increase in sophisticated threats. In this regard StarMag has recently highlighted also how OpenAI in recent years has radically changed its position with respect to relations with the military sector: if in the internal rules that prohibited the use of its technologies in the war field, today it is officially part of the technology companies that actively collaborate with the American military-industrial complex.
Precisely following the significant increase in cyber attacks, the rule becomes the race to develop advanced defensive and offensive capabilities, as well as the arms race for strategic independence. However, among the most important points of Cybersec 2025 it was highlighted how international law can be fully applied to cyberspace to promote responsible behavior of States and maintain peace, security and global stability. Even if the great powers agree on this, they then diverge on interpretations and applications of the rules. But the future will certainly be better than the present, where we will focus on development instead of hatred, especially in view of what will be left to future generations of Internet users, especially because widespread access to information and digital technologies, if well guided, can foster a culture of mutual understanding and cooperation, countering divisions and conflicts.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
