
This isn’t the first time criminal hackers make mistakes, and it won’t be the last.
The pro-Russian hacktivist group CyberVolk launched the RaaS service VolkLocker (also known as CyberVolk 2.x). However, security researchers discovered that the malware’s developers made several flaws that allowed victims to recover their files for free.
SentinelOne researchers report that the attackers embedded the master encryption key directly into the malware binary and saved it as a plain text file in the %TEMP% folder.
The file is called system_backup.key, and everything needed to decrypt the data can be easily extracted from it. Researchers speculate that it’s some sort of debugging artifact that wasn’t cleaned before release.
RaaS operators are apparently unaware that their customers are distributing builds with the backupMasterKey () function.
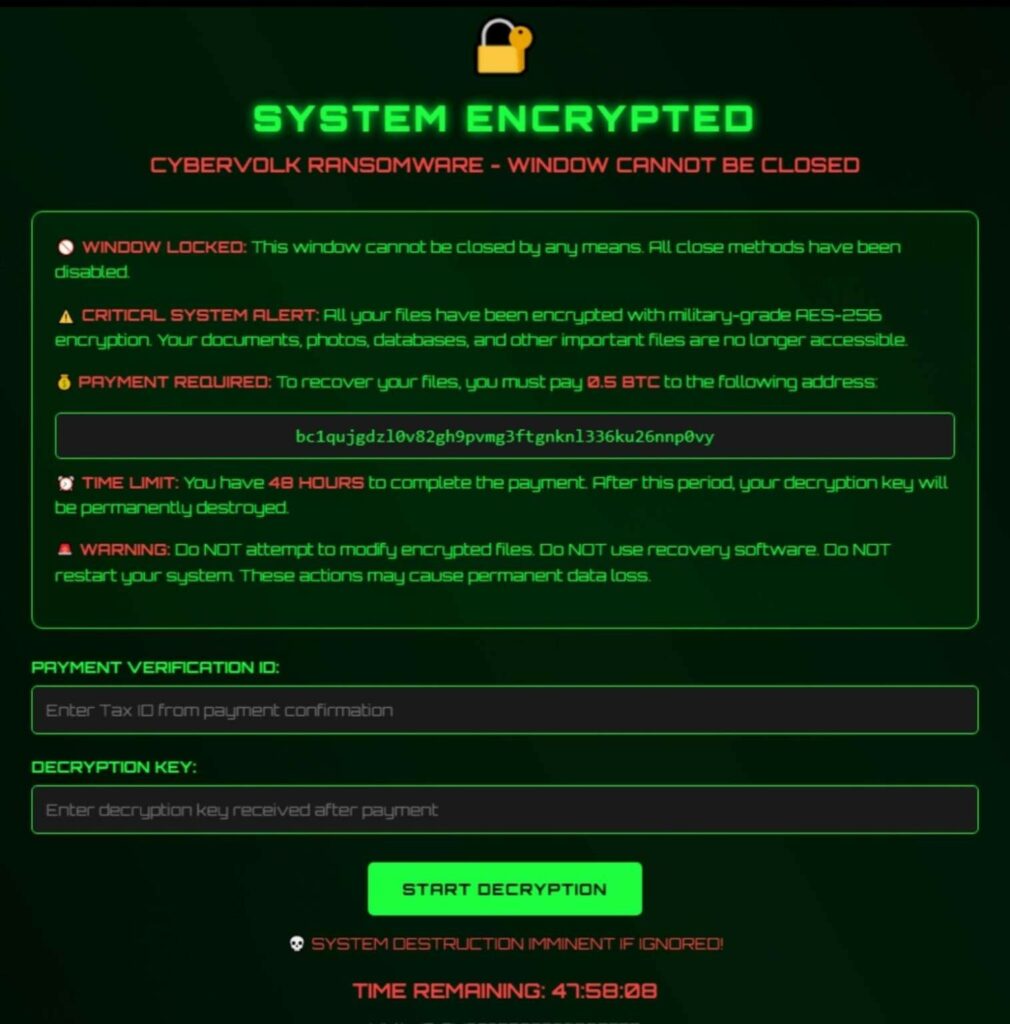
CyberVolk is believed to be a pro-Russian group based in India that operates independently. While other hacktivists typically limit themselves to DDoS attacks, CyberVolk has decided to take on the challenge of creating its own ransomware.
The attackers first announced it last year, and while they were subsequently banned from Telegram several times, in August this year the group unveiled the VolkLocker (CyberVolk 2.x) malware and its Ransomware-as-a-Service (RaaS) platform.
VolkLocker is written in Go and runs on both Linux (including VMware ESXi) and Windows. Access to RaaS for a single operating system costs between $800 and $1,100, while Linux and Windows versions cost between $1,600 and $2,200, while a standalone RAT or keylogger costs $500. Purchasers of the malware gain access to a Telegram bot generator, where they can configure the ransomware and receive the generated payload.
To create your ransomware, you need to specify a Bitcoin address, a Telegram bot token, a chat ID, a ransom payment deadline, an extension for encrypted files, and set self-destruction options.
Once launched on the victim’s system, VolkLocker escalates privileges by bypassing Windows User Account Control, selects files to encrypt from a pre-configured exclusion list, and encrypts data using AES-256 in GCM mode.
Researchers also noted that the code contains a timer that activates a wiper that destroys the user’s folders (Documents, Downloads, Pictures, Desktop ) after the ransomware expires or when an incorrect key is entered into the HTML ransom window.
According to experts, the malware’s main weakness lies in its encryption. VolkLocker doesn’t generate keys dynamically, but uses the same hardcoded master key for all files on the infected system. As mentioned above, this key is written to the executable file as a hexadecimal string and duplicated in a text file in the %TEMP% format.
Experts believe these errors indicate quality control problems: the group is trying to aggressively expand by attracting new, inexperienced “partners,” but is failing to complete even the most basic tasks.
It’s generally considered best not to disclose details about ransomware vulnerabilities while the attackers are still active. Instead, experts typically notify law enforcement and companies specializing in ransomware negotiations, who can then assist victims privately. Because CyberVolk remains active, SentinelOne explains that disclosing information about VolkLocker vulnerabilities is unlikely to hinder the efforts of colleagues and law enforcement to combat the group.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
