
A malicious actor, under the name “tikila”, has posted an advertisement on a hacking forum for the sale of a local privilege escalation (LPE) vulnerability for Windows. According to the post, this vulnerability has been tested and confirmed to work on various versions of Windows, including Windows 10, Windows 11, and several Windows Server versions (2008, 2012, 2016, 2019, 2022).
The announcement claims that the vulnerability is 100% reliable and does not cause system crashes, ensuring process continuity. The author specifies that the vulnerability has been tested on fully updated and patched systems, implying it might exploit an unknown zero-day flaw.
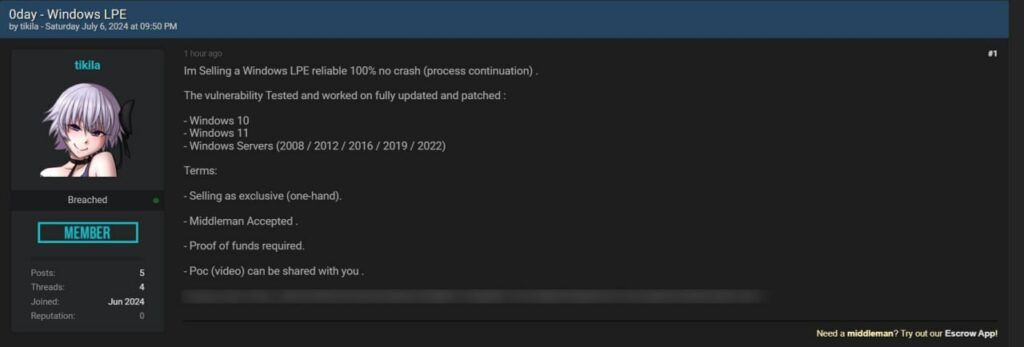
The terms of sale for the vulnerability include:
The sale of an LPE vulnerability for Windows represents a serious cybersecurity threat, as it could allow attackers to gain elevated privileges on compromised systems. This type of access can be used to execute malicious code, steal sensitive data, or take full control of victim machines.
Organizations should be vigilant and monitor their systems for signs of compromise. It is advisable to keep all software updated and apply security patches released by vendors. Additionally, it is crucial to implement defensive security measures, such as using antivirus software and firewalls, and limiting user privileges to reduce the risk of privilege escalation.
Tikila’s announcement once again highlights the continuous evolution of cyber threats and the need for constant vigilance in protecting IT infrastructures. Companies must stay updated on new vulnerabilities and adopt a proactive security strategy to defend against these potential threats.
In case of suspected compromise, it is essential to immediately conduct a thorough investigation to identify and mitigate any potential damage. Collaboration with cybersecurity experts can provide additional support in protecting and strengthening corporate defenses against emerging threats.
To stay updated on Microsoft vulnerabilities, you can check the Security Update Guide service.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
