
The underground landscape of cybercriminal forums continues to evolve and is changing. With an official announcement published on June 25, 2025 both on Telegram and within the DarkForums forum, the user Knox – current administrator and top figure of the platform – has communicated the transfer of control of the Telegram channel “The Jacuzzi”, also known as baphchat, under the aegis of DarkForums.
This move represents yet another piece in the slow but inexorable disintegration of the ecosystem left vacant by BreachForums, following the legal events that marked its closure in 2023 and subsequent instability in 2024. The “Jacuzzi” channel was originally conceived as an unofficial space for the BreachForums community, where operators, vendors and cybercriminals could interact informally outside the rigidity of the main platform.
BreachForums spiritual successor to the famous RaidForums– had consolidated over time a centralized structure focused on the exchange of breached databases, personal data (PII) and credentials, until the arrest of its administrator “pompompurin” in March 2023 marked a point of no return. Despite several attempts to relaunch it by actors such as Baphomet and other forks of the community, the project never returned to its initial stability.
In this void, DarkForums has been able to play a strategic role, acquiring credibility and users through a similar offer in terms of content (RDP access, combolist, leaks, malware development tools) but with less exposed governance. With the takeover of “The Jacuzzi”, DarkForums is not just incorporating a channel: it is consolidating a communications and reputation infrastructure previously associated with the BreachForums brand.
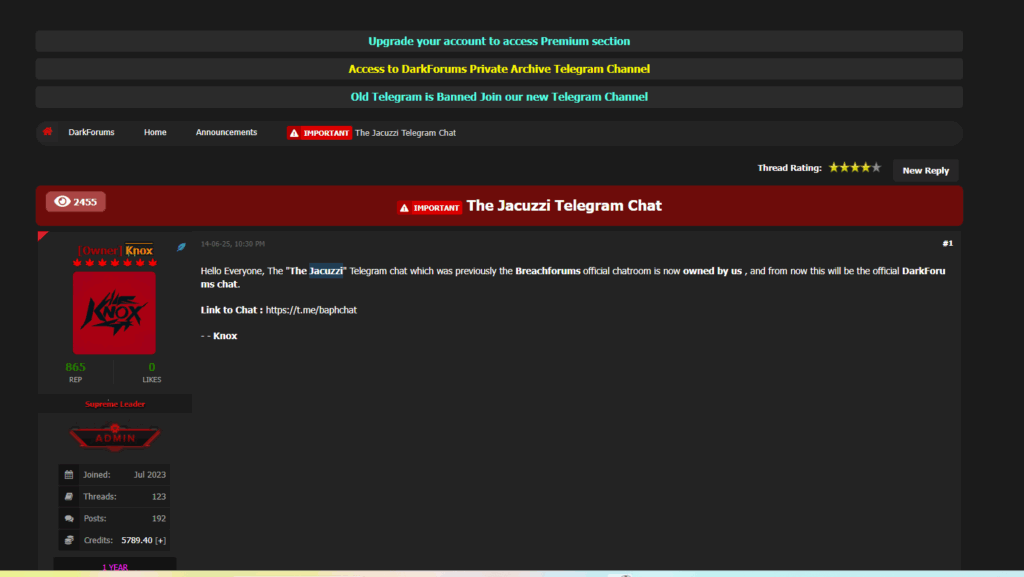
In the forum post, administrator Knox writes:
“The ‘Jacuzzi’ Telegram chat which was previously the Breachforums official chatroom is now owned by us, and from now on this will be the official DarkForums chat.”
At the same time, the following references were made available:
The initiative also strengthens the out-of-band communication ecosystem typical of modern criminal forums, where Telegram channels act as a fallback in case of downtime, seizure or reputation issues of the main domains. The choice to consolidate “The Jacuzzi” as an official affiliate environment allows DarkForums to actively monitor community engagement, attract former BreachForums users and legitimize itself as an alternative hub.
From a Cyber Threat Intelligence perspective, this change represents a further recombination of leadership dynamics in illicit data marketplaces. The maintenance of active Telegram references, now under new management, is an important indicator of the persistence of cybercrime-related activities, even in contexts of structural discontinuity.
Organizations that monitor activities on OSINT/CLOSINT channels should update their tracking models, including this new DarkForums asset as an active source for potential early warnings, internal communications to the threat actor economy and promotion of new dumps or illicit services.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
